Stringent Active Directory monitoring enables companies to identify suspicious changes and take prompt action to prevent an attack and lessen its impact. Active directory monitoring is the process of making sure that Active Directory (AD), the main identity and access management system used by most businesses today, is functioning correctly. AD replication, security, and auditing are all critical parts of AD monitoring.
Best Practices for Active Directory Monitoring
Use these strategies to monitor Active Directory effectively:

- Log Gathering and Analysis at Centralized Repository: Keeping hundreds of devices will result in millions of events every day in a large area. Since you will only need a portion of those, sorting through the events by the event IDs listed above across different servers and regions will take a lot of time. There are ways to keep them in one place so that you can do a better analysis. It is simpler to specify which events to monitor while addressing a problem when logs are gathered in one location. Aggregate logs from every source onto a single platform, such as servers, applications, network devices, and security products. A complete image of your infrastructure is given by this centralization that facilitates search, analysis, and correlation of data across scattered systems.
- Monitoring User Activity: User activity monitoring is regarded as the best active directory monitoring technique. Tracking successful logins, unsuccessful attempts, and odd login timings should be the focus. It is advised to use brute-force assaults or stolen credentials if there is an increase in unsuccessful login attempts from a single IP address or if login attempts occur outside of regular work hours. Users with administrator access should pay close attention to everything they do. Any action taken by users with administrative privileges should be closely monitored. Password resets, group membership changes, and access to critical information should all be closely monitored. Any unusual activity from privileged accounts needs to be looked into right away.
- Recognize Tier 0 Assets: The Active Directory domains and forests are administratively under the direct or indirect control of accounts, groups, and other assets are referred as Tier 0 assets. These assets are the most important and delicate systems and components in an organization’s infrastructure. If these assets are compromised, the operations, reputation, and even financial viability of the company may suffer serious harm. Understanding the tier 0 assets is essential for active directory monitoring. In order for an attacker to take control of your domain in a few simple steps after breaching a regular user account, the attack vectors must be planned out. To reduce risk, minimize the choke points that attack routes share and keep a careful eye on activities near all remaining Tier 0 assets.
- Modifications in Group Policy Objects: GPOs are used to specify the security configurations throughout your domain. These items give administrators the ability to implement cybersecurity safeguards and limit user access to the network from a single location. Any modifications made to GPOs must be tracked to ensure that no unapproved changes take place. Check security settings, password policies, and access rights for any strange changes. Keeping an eye on these items will increase environmental stability and help prevent security threats.
- Setting Up Audit Policy: Making sure that every action taking place in the environment is recorded in the security log is a crucial first step in monitoring the active directory environment. Granular event collection and noise reduction are made possible by the configuration of the audit policy. In addition, to avoid data loss and overwrites, a flexible retention strategy and a suitable security log size are crucial.
- Analyze AD Health: Since users, PCs, printers, and other Active Directory objects will come and go, provisioning and provisioning procedures are necessary. As much as feasible, these processes must be automated using workflows that rely on permission. Finding dormant user and computer accounts on a regular basis is crucial to preventing misuse. Additional best practices include monitoring the health of domain controllers and replicating data in real time between them. Failure to do so may result in users having trouble accessing the resources they need to finish their tasks or login in. Replication ensures that the data is identically replicated across all Domain Controllers on the network. Inconsistent data and secure vulnerabilities may result from unhealthy replication. For the directory to remain healthy, it is essential to keep an eye on the Active Directory Health Check service’s status. Account lockouts, login issues, and many other problems are caused by directory service faults.
- Maintain Alerting and Reporting: Continue to monitor Active Directory (AD), including alerting, and reporting. These aspects are essential for performance optimization, security assurance, and compliance. These features give insight into AD activity, enabling proactive problem-solving and identification while streamlining security investigations. It is not enough to merely monitor Active Directory; one must be able to comprehend the massive volume of data collected and respond quickly to any threats to availability, performance, or security. Thus, it is necessary to have robust policies, advanced alerting, and comprehensive and customizable reporting.
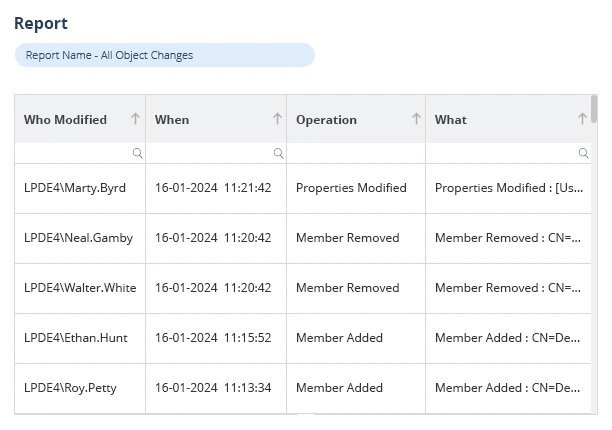
How Lepide Helps in AD Auditing and Monitoring
Lepide Auditor for Active Directory is a dedicated Active Directory monitoring and auditing solution that helps companies simplify and elevate their AD monitoring practices. Lepide overcomes the limitations of native auditing, proving more accurate than PowerShell, less noisy than event logs, and simpler to use than any other solution. Lepide monitors and reports on all manner of AD events, changes, and states, including permissions, configurations, logon behavior, and more. With a simple interface, customisable reports, and real time alerts, Lepide helps companies achieve enterprise-level AD auditing and monitoring without the enterprise price-tag.
Looking to simplify your AD auditing and monitoring? Schedule a demo with one of our engineers or download a free trial