Detect and prevent insider threats.
Protect your organization from malicious, negligent, and compromised insiders through proactive auditing, user behavior analysis, and automated threat response.














Traditional security tools focus on keeping the threats out, but most data breaches happen because of disgruntled employees, compromised accounts, or innocent mistakes. The key is visibility into what trusted users do once they’re in.
Know which users you’ve trusted with privileged access. Spot and remediate excessive access. Keep an eye on permission changes and privilege creep.
With AI-back user behavior analytics and anomaly spotting, you can detect and respond to the symptoms of a compromised user account or insider threat in real time.
Real time alerts and automated threat models / workflows spot and react to the symptoms of insider threats so that you can contain the affected account quickly.
Keep track of which users are accessing and interacting with sensitive data across your key on-premises and cloud data stores. User behavior analytics and anomaly spotting will enable you to detect when user behavior changes – a critical sign of an insider threat.
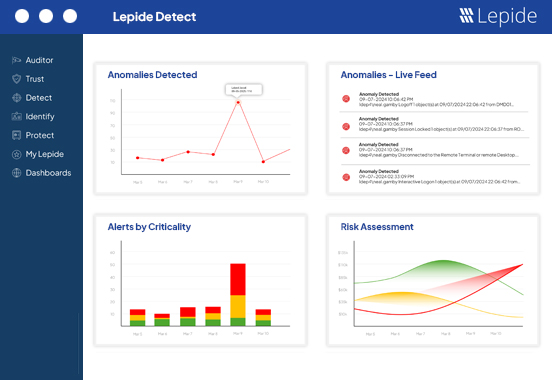
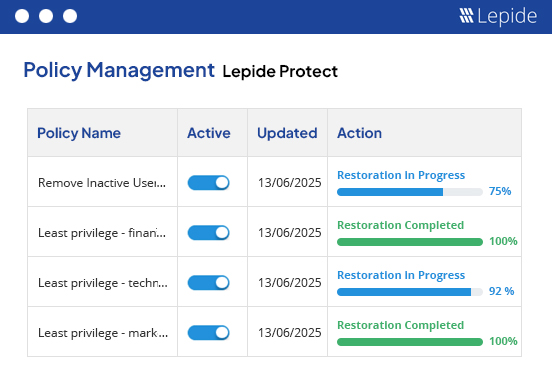
Identify who your privileged users are and see how they are getting access. Report on users that have excessive access to sensitive data based on their data usage patterns. Automate remediation with custom policies to ensure least privilege and mitigate the risks of compromised accounts impacting sensitive data.
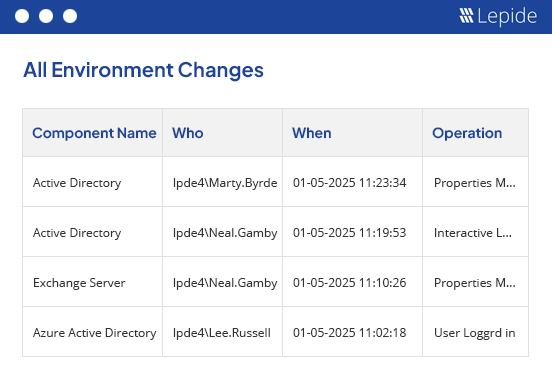
Clear, searchable records of every event, change, or user interaction make it easy to investigate incidents with speed and clarity. Find out what happened, who was involved, and what data was affected.
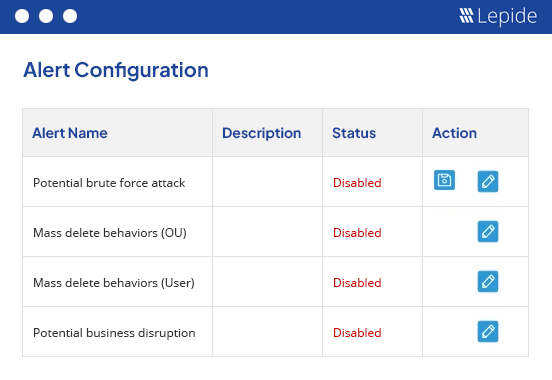
Pre-defined threat models and workflows, combined with real time alerts, mean you can take a more hands off approach to insider threat prevention. When the signs of a compromised account are detected, you can automate actions like disabling the account, and get notified of everything through our mobile app.
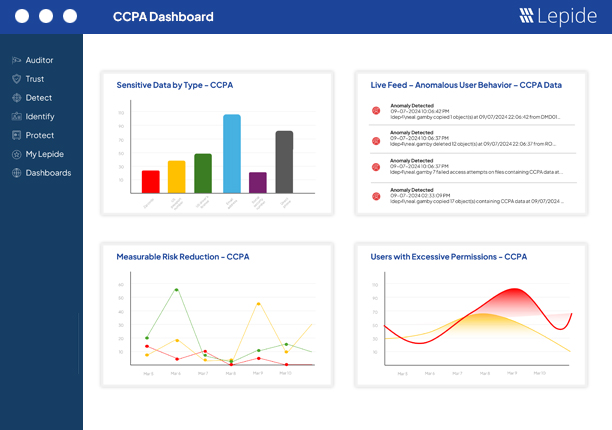
Need to get a quick overview of your compliance posture to share internally or with auditors? Our dedicated compliance dashboards make this possible with real time, customisable awareness.
From CISOs to SecOps teams, find out how data protection is evolving and what you need to do to keep up.
Get the free guide now!