NTFS Permissions Reporting Tool
Instantly see who has which permissions on your shared folders and from where the permissions are being assigned.














Lepide’s NTFS permissions reporting tool enables IT teams to analyze NTFS permissions applied to shared files and folders. It helps you ensure that only the right people have access to the right data, thus minimizing the risk of security breaches. With Lepide, you can instantly see who has received which permission, and from where, on a shared file or folder in your File Server.
Lepide File Server Auditor generates reports that clearly show the current permissions of Active Directory objects on the shared files and folders of Windows File System. With numerous options available, you can get a summarized view of the different kinds of permissions very easily. Our automated solution scans the permissions of the selected shared files and folders either manually or at scheduled intervals.
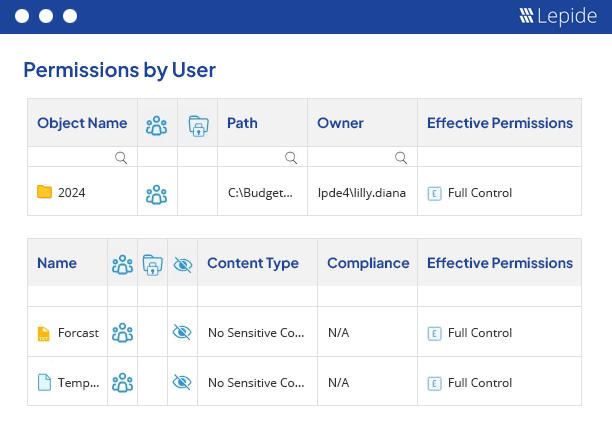
Lepide File Server Auditor evaluates the current effective permissions after calculating the NTFS permissions and Share permissions. That way, you can see the exact current permission for any user on any shared file or folder. All 13 permissions are evaluated one by one, and the final current permissions applied on a selected file or folder for an Active Directory user, group or another object. Each permission is denoted with a different icon and a different color.
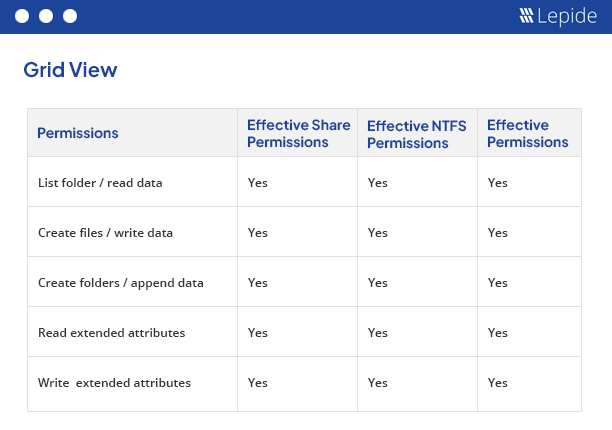
Our File Server change auditing solution has dedicated features that help you analyze the inherited permissions applied on shared files and folders. You can view the inherited permissions report and sort it by users in a different tab. In the section where the list of sub-folders and files of the selected folder are displayed, a red icon will denote where the inherited permissions broke. Our solution also provides a dedicated screen to view the group memberships for a user who has inherited permissions on the selected file or folder.
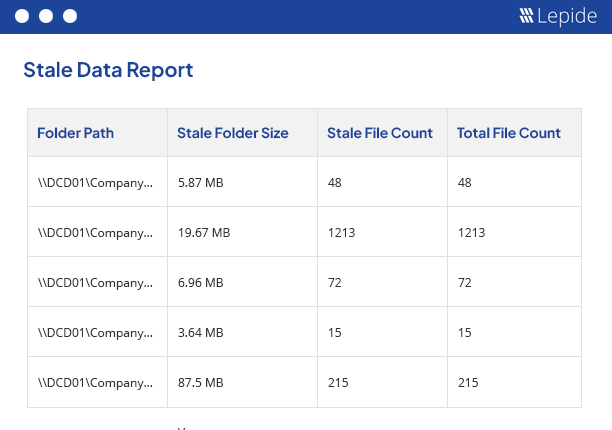
Stale objects in the File Server are actually unused files and folders. It is necessary to monitor these objects to prevent insiders from misusing them. Some files or folders are not meant to be used for long, as they store critical business information. Using them can increase the chances of data loss. Lepide File Server Auditor shows you which objects are stale at any one time. It can reveal any change made to stale files and folders and can send you real-time alerts.
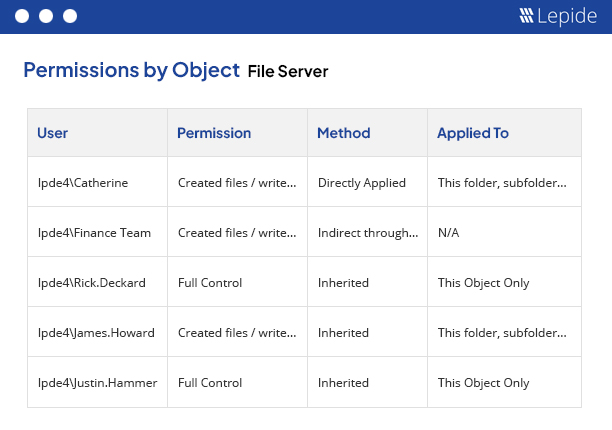
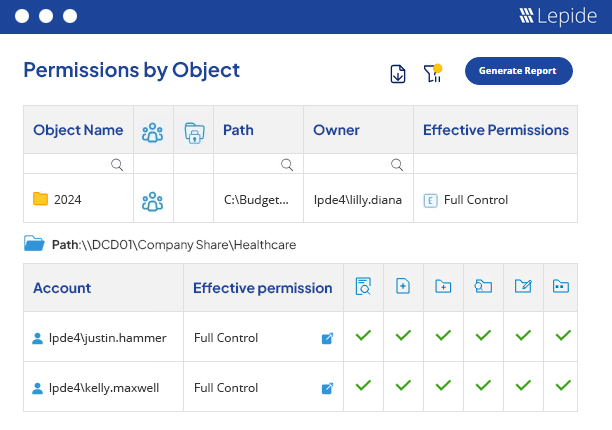
After viewing the current permissions of a selected file or folder, you can investigate how the permissions to this file or folder have been applied and what changes have been made. The investigation opens in a separate and dedicated window, where you can apply the filters and check the permission changes for other objects in the hierarchy.
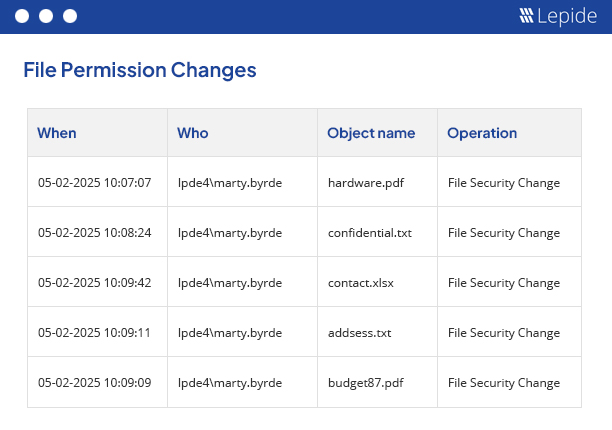
In the Current Permissions report, you have three levels of filtration to gather the required data. Filters can be applied to folders and types of files in File Server. After generating the report, you can further filter the content (sub-folders and files) of the selected folder to find which permissions you want to see. The third level further enhances the detail of the report by filtering by account; helping you determine direct permissions, indirect permissions and inherited permissions. You can switch to the “Permissions by User” tab to view reports sorted by users. All these reports can be saved in multiple formats like PDF, MHT and CSV.
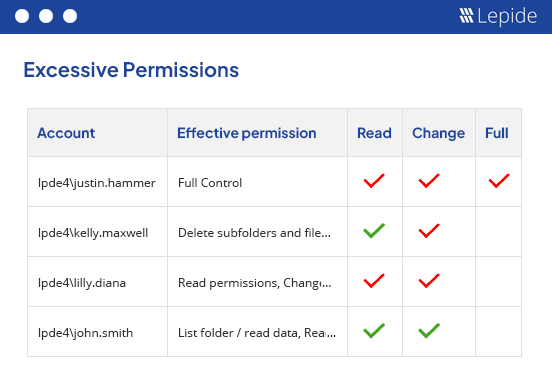
Just as important as understanding who has got access to your most critical data is having a better understanding of if they actually need access and if the level of access is appropriate. With our excessive permissions reporting we can help you adopt a stronger least privilege model and revoke privileges from users who are not actually utilizing them. Thus, giving you the visibility you need to further improve the security surrounding your organization’s data.
By following the guidelines outlined in this paper, your organization can establish a robust data access governance program that supports its business objectives and protects your valuable data assets.
Get the free guide now!