Last Updated on April 25, 2025 by Satyendra

Active Directory (AD) is a database and set of services that connects users with the resources they need to do their work. It enables administrators to manage permissions and control access to network resources, specifying which users and computers are available and who’s allowed to do what.
Active Directory is a fundamental element of any Microsoft Windows environment and plays an essential part in authentication, access management, account management, and authorization. It is because of this that it’s crucial to engage in Active Directory auditing and reporting best practices.
What is Active Directory Auditing and Why is it Important?
Active Directory auditing refers to the process of monitoring and recording events related to the use of Microsoft’s Active Directory. Active Directory is a directory service used by many organizations to manage users, computers, and other resources on their network.
AD auditing involves collecting and analyzing data on activities such as user logins, changes to user accounts, modifications to group policies, and other actions performed within the Active Directory environment. This information is then used to identify potential security threats and ensure compliance with regulatory requirements.
Auditing is important for several reasons. Firstly, it helps to maintain the integrity of the Active Directory environment by detecting unauthorized access and changes to important system components. Secondly, it provides a valuable source of information for incident response and forensic investigations, enabling organizations to quickly identify and respond to security incidents.
Auditing Active Directory also helps organizations to comply with various regulatory requirements, such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA), which mandate that organizations must have appropriate security controls in place to protect sensitive data.
Download Free Tool

How to Enable AD Auditing and Check Audit Logs?
Manually checking Active Directory audit logs involves using the Event Viewer to track changes. While this method can be time-consuming, it provides valuable insights when automated solutions are not available.
Enable Auditing for Active Directory
Here’s are two ways to enable auditing:
- Enable Auditing via GPMC: Before you can review audit logs, you must enable auditing in Active Directory. This can be done through the Group Policy Management Console (GPMC).
- Navigate to Group Policy Management.
- Edit the Default Domain Policy or a specific OU policy.
- Go to Computer Configuration > Windows Settings > Security Settings > Advanced Audit Policy Configuration.
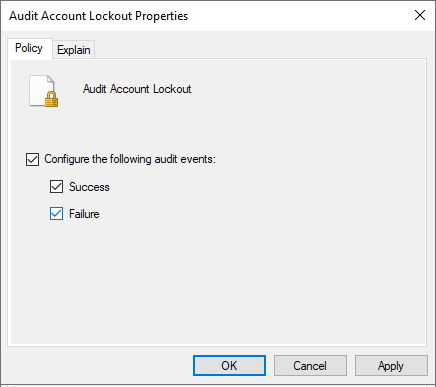
- Configure audit policies for Account Logon, Account Management, DS Access, Logon/Logoff, Object Access, and Policy Change categories.
- Check both “Success” and “Failure” boxes for each policy.
- Now, run gpupdate /force to update GPO
- Enable Auditing via ADSIEdit.msc: Use Active Directory Service Interfaces Editor to view Connection Settings. To do so, establish connections with all four available naming contexts to turn on their auditing for:
- Default Naming Context
- Configuration
- RootDSE
- Schema
How to Check AD Audit Logs
To access the security event log:
- Open Event Viewer (eventvwr.msc).
- Navigate to Windows Logs and select Security.
- In the Event Viewer, right-click on Security and select Filter Current Log.
- Enter the relevant Event ID in the “Event IDs” field to search for specific events (e.g., 4720 for user account creation).
- Double-click on an event to view its details, including the user who made the change, the time, and the object modified.
Which AD Security Events Should Be Tracked?
The difficulty of effective Active Directory auditing is due, in part, to the variety of log events that exist. There’s a lot of noise that you need to sift through. Thankfully, there are some events that you can look for specifically when it comes to ensuring the security of your AD.
| Event Name | Related Event IDs | Description |
|---|---|---|
| User Authentication | 4624, 4625, 4648 | When you track user authentication events your security capabilities improve through detecting attempts to attack your system and understanding atypical login activity and abnormal IP address behavior.
A credential stuffing attack is likely to have occurred when multiple accounts show a pattern of failed logon attempts based on the Event ID 4625. Successful user logons that happen during out of business hours could signal account compromises according to event ID 4624. |
| Account Management | 4720, 4722, 4723, 4726, 4732, 4767 | Auditing user account activity, spanning account creation to deletion as well as password resets and privilege escalation, is a vital aspect of AD security. Event ID 4720 shows when an account gets created, and Event ID 4723 shows when users try to modify their passwords. |
| Directory Service Changes | 5136, 5137, 5139 | Track modifications to critical AD objects like users, groups, or OUs. Event ID 5136 generates an alert when directory object properties are modified, and Event ID 5137 creates logs about new directory object creations.
Monitoring these security events lets you detect unauthorized or suspicious changes before they develop into major security incidents. |
| Policy Change Events | 4739, 4719, 4902 | Aimlessly tracking Group Policy changes during operations is out of the question. Security threats consistently target Group Policies, which regulate password policies and desktop parameters, because attackers want to degrade security or gain persistent access.
Monitoring these security events enables you to confirm that authorized administrators are the only ones making changes to security policies. |
What are the Key Things to Audit in Active Directory?
Effective auditing of AD leads to early threat detection or prevents major data breaches from occurring. The following is a list of the essential events and changes that all organizations must keep under constant observation:

- User Account Activity– The monitoring of account logons and lockouts, and privilege changes should happen continuously. Attackers obtain unauthorized entry to user accounts frequently which the following sentence describes as one of the common methods for gaining unauthorized access. Password spray attacks may be indicated by multiple lockouts yet compromised credentials tend to lead to unusual times of login attempts.
- Privileged Accounts and Groups– Users within the Domain Admins group, along with Enterprise Admins and Schema Admins, maintain distinctive control over your entire network infrastructure. Track all changes made to privilege accounts by monitoring their group modifications together with their logon behavior. Minor privilege elevation that goes unnoticed can result in unlawful control over your full environment.
- Group Policy Modifications– Organizations use GPOs to establish control of their system management processes throughout their network. The tools are equally useful when utilized correctly and when used improperly by attackers. The detection of unapproved Group Policy Object changes should focus on modifications that affect security settings, as well as script deployment and software restriction policy updates.
- Organizational Unit (OU) Changes– The scope of policies depends on Organizational Units, which separate areas and determine management boundaries. OU change tracking helps stop unauthorized model modification, which is a typical method used by privilege abusers.
- Access Control List (ACL) Modifications– Your directory’s Access Control Lists determine the users who receive access permissions by resource type. You won’t notice unauthorized modifications to Active Directory ACLs that end up exposing your organization’s sensitive resources. Tracking changes to resource access helps stop access escalations and implement restricted permission agreements.
- Inactive Accounts– Dormant user and computer accounts are a significant security risk as they provide an open invitation for hackers to gain unauthorized access to systems and data. Inactive accounts often accumulate unnoticed over time, but may still retain access privileges or contain sensitive information. These accounts can be exploited by attackers for unauthorized access or as backdoors into the network if not properly managed and disabled. Regularly identifying and deactivating inactive accounts is crucial for minimizing risks such as data breaches, compliance violations, and privilege escalation.
What Are the Best Practices and Checklist for Active Directory Auditing?
The auditing technique matters more than the actual items being evaluated. Your AD auditing strategy will become dependable and regulated through the adoption of these best practices and checklist:
- Enable Advanced Audit Policy Configuration– The implementation of Windows Advanced Audit Policies should replace legacy auditing methods. These auditing features provide detailed tracking capabilities that enable you to define specific audit criteria to reduce excessive audit data. Without enabling every possible logon event, you can audit logon successes and failures independently.
- Centralize and Correlate Audit Logs– You should accumulate logs into either a Security Information and Event Management platform or use a tool like Lepide for optimized event aggregation and filtering. The placement of essential audit signals becomes more efficient as a result of this method, thus enabling quick incident discovery.
- Set Real-Time Alerts for Critical Events– Some occurrences require your intervention, but others should remain unattended. Your monitoring system must trigger notifications for dangerous system activities that involve privileged group member additions or extensive account locks, or Group Policy Object removals. Active alerts enable teams to respond quickly enough to prevent destructive consequences.
- Conduct Regular Audits and Reviews– Audits need scheduled attention because they never operate on a stand-alone basis. Audit data needs periodic checks, which should concentrate on time-based issues and unexplained patterns in the information. Check both the user access levels and their necessary permissions for their roles.
- Secure and Backup Audit Logs– Make sure audit logs are tamper-proof and stored securely. Ideally, they should be written to write-once-read-many (WORM) storage or backed up frequently to prevent attackers from covering their tracks after a breach.
What are the benefits of Active Directory Auditing?
Active Directory auditing provides organizations with security benefits that go beyond basic compliance checks by serving as the core security approach, which delivers multiple lasting advantages.
- Proactive Threat Detection– Your auditing strategy lets you identify security attacks during their early stages, such as privilege escalations alongside brute-force logins and lateral movements, before serious damage occurs.
- Compliance with Regulations– Under the requirements of HIPAA, GDPR, SOX, and PCI-DSS, organizations need to track and document detailed records of system access activities and critical system modifications. External regulating bodies depend on Active Directory auditing because it delivers the necessary transparency required to pass audits while protecting you from regulatory penalties.
- Improved Incident Response– The occurrence of an incident creates forensic tracks through audit logs to help you understand both the sequence of events as well as revealing who was responsible and when the breach took place. Audit logs offer essential value throughout the investigation, along legal requirements.
- Operational Oversight and Accountability– The auditing process creates a systematic tracking system that connects all changes and system events to individual users or machines. The ability to track user actions through visibility improves both staff responsibility and allows IT groups to implement strong change management controls.
- Reduced Risk of Insider Threats– Your organization can stop malicious acts inside the network by regularly checking privileged user activities to promptly investigate employee or contractor suspicious activities.
How Lepide’s Free AD Auditing Tool Helps
Lepide Change Reporter for Active Directory (Free Tool) provides a comprehensive solution that overcomes the key limitations of native Active Directory auditing:
Centralized Logging: Unlike Microsoft’s decentralized approach that requires checking security event logs on each domain controller, Lepide consolidates all audit data into a single, centralized platform, giving administrators a complete picture of AD activity across the environment.
Comprehensive Coverage: Where native auditing leaves critical gaps in monitoring (especially for Group Policy), Lepide delivers complete visibility into all aspects of Active Directory, including thorough auditing of Group Policy changes, object modifications, permissions changes, user login history, and account lockouts.
Clean, Interpretable Data: Lepide transforms the noisy, difficult-to-interpret native audit logs into clear, actionable information. The solution filters out irrelevant data and presents events in an easy-to-understand format, eliminating duplicate entries that often plague native logging.
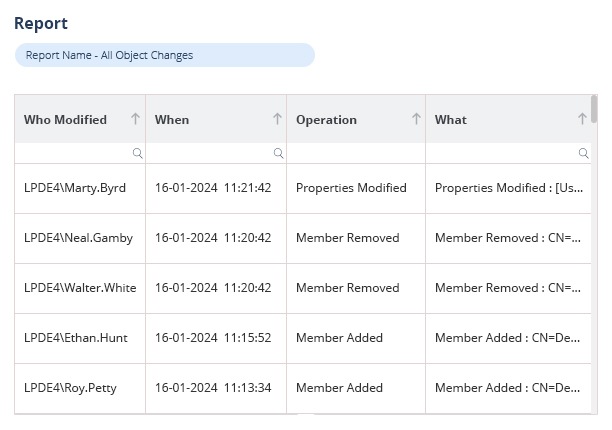
By addressing these fundamental limitations of native AD auditing, Lepide Change Reporter provides a straightforward and efficient approach to monitoring your Active Directory environment, enhancing security posture while reducing administrative overhead.

 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why AD Account Keeps Getting Locked Out Frequently and How to Resolve It
