By 2026, most security teams are already using AI, but many are still overwhelmed by alerts, siloed tools, and slow response times. The real innovation isn’t more AI; it’s AI that delivers clarity by turning fragmented signals into actionable insight.
In this blog, we highlight 10 AI-powered security platforms that go beyond hype, helping organisations solve real operational and security challenges.
Top 10 Most Innovative AI-Powered Security Tools
- Lepide IQ
- Microsoft Security (Defender, Sentinel, Security Copilot)
- CrowdStrike Falcon Platform
- Lepide Protect
- Darktrace Identity
- Vectra AI
- SentinelOne Singularity XDR
- Splunk Enterprise Security
- IBM QRadar (EDR and SIEM)
- Elastic Security (Investigation and Response)
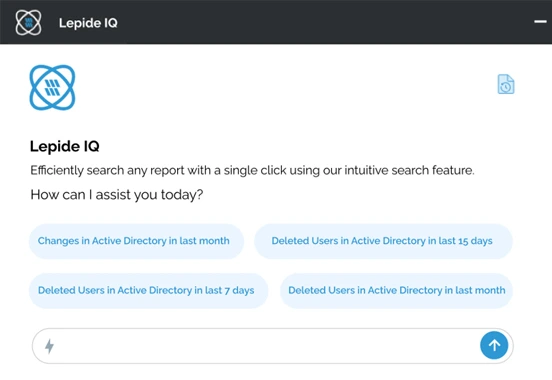
1. Lepide IQ
Lepide IQ was developed to provide clarity for teams experiencing an overwhelming amount of security data. Lepide IQ serves as an additional member of your security team, summarizing information, identifying risks, and delivering an explanation of any changes in easy-to-understand terminology.
What makes Lepide IQ different is its focus on understanding, not detection. It provides teams with the fastest means of reviewing security reports, helping them to learn what has changed and understand the potential impact of the changes on the organization. Additionally, Lepide IQ provides guidance to the user as to where additional investigations need to take place.
Key Features
- AI-driven summarization of security reports
- Contextual insights across identity and data events
- Faster investigation with natural language explanations
- Reduced manual analysis effort
- Works natively within the Lepide platform
2. Microsoft Security (Defender, Sentinel, Security Copilot)
Microsoft’s security ecosystem incorporates a vast amount of information with its current AI-based platform. With Security Copilot layered across Defender and Sentinel, analysts can ask questions in natural language and receive structured, actionable insights drawn from their environment.
However, the true significance lies in scalability. When an organization heavily utilizes Microsoft products, AI can seamlessly integrate information about an individual’s actions (identity), devices (endpoint), data stored within the cloud, and any email activity into one single “flow” of investigation. This leads to organizations being able to focus on making decisions rather than concentrating on various alerts.
Key Features
- Generative AI security assistant (Security Copilot)
- AI-assisted investigation and alert prioritization
- Deep integration with Microsoft identity and cloud
- Automated incident summaries and response guidance
- Enterprise-scale correlation across tools
3. CrowdStrike Falcon Platform
CrowdStrike applies machine learning and AI across endpoints, identities, and cloud workloads to detect threats based on behavior, not signatures. The platform automatically builds threat context so analysts see attacks as stories, not isolated alerts.
Its strength lies in reducing noise. Falcon’s AI filters low-value signals and pushes real threats to the surface, making it a strong choice for teams that want fast detection without endless triage.
Key Features
- AI-native endpoint and XDR detection
- Behavioral threat analysis
- Automated threat correlation
- AI-assisted response workflows
- Cloud and identity signal integration
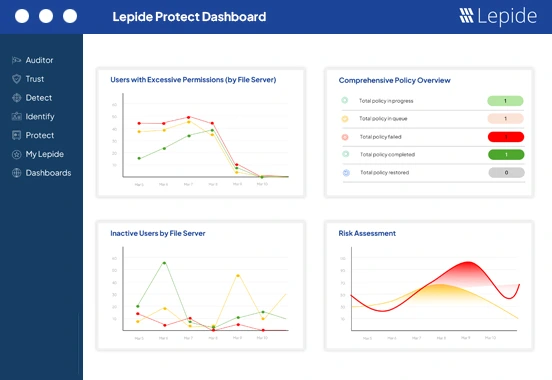
4. Lepide Protect
Lepide Protect is an AI-led permissions management solution that detects, prioritizes, and can automatically revoke excessive or risky permissions. It uses AI and user behavioral analytics to surface who has access to what, understand whether that access is “excessive”, and offers one-click remediation to reduce exposure in minutes rather than weeks.
Key Features
- AI-driven detection of excessive permissions and ownerless access.
- Prioritization and risk scoring to focus cleanup on the highest blast-radius items.
- One-click revoke/rotation workflows to remove or reduce rights at scale.
- Integration with Lepide’s broader DLP and auditing modules for context-rich decisions.
- Dashboards and compliance reports that track remediation progress and provide audit evidence.
5. Darktrace Identity
Darktrace Identity uses self-learning AI to understand how users normally behave. It creates a baseline of identity activity and flags subtle deviations that may indicate compromise, misuse, or insider threats.
This approach is especially effective against slow, low-noise attacks that bypass traditional rule-based systems. Instead of matching known patterns, Darktrace focuses on abnormal behavior.
Key Features
- Self-learning behavioral models
- Identity misuse and anomaly detection
- Real-time risk scoring
- Minimal reliance on static rules
- Insider and credential threat visibility
6. Vectra AI
Vectra applies AI to detect attacker behavior across network, cloud, and identity layers. Rather than alerting to everything, it focuses on identifying actions that resemble real attack techniques.
Its standout capability is prioritization. Vectra ranks detections based on certainty and impact, helping SOC teams focus on what is most likely to be a real threat instead of chasing noise.
Key Features
- AI-driven attacker behavior detection
- Automated threat prioritization
- Network, cloud, and identity coverage
- Reduced alert fatigue
- SOC-focused investigation workflows
7. SentinelOne Singularity XDR
SentinelOne’s Singularity platform uses AI to stitch events together into attack storylines. Instead of presenting isolated alerts, it shows how actions connect across endpoints, users, and systems.
This storytelling approach shortens investigation time and improves response speed. Teams spend less time correlating logs and more time stopping threats.
Key Features
- Autonomous AI-based detection
- Attack storyline visualization
- Real-time response and containment
- Endpoint and XDR coverage
- Reduced manual investigation effort
8. Splunk Enterprise Security
Splunk ES brings AI and machine learning into large-scale log analysis. It helps surface anomalies, suggest correlations, and summarize security activity across massive data volumes.
Splunk’s power comes from flexibility. When configured well, its AI features help analysts extract meaning from chaos. The value depends on how well teams design what they collect and analyze.
Key Features
- ML-based anomaly detection
- AI-assisted alert correlation
- Custom dashboards and searches
- SOC-ready investigation workflows
- Works across any log source
9. IBM QRadar (EDR and SIEM)
SentinelOne’s Singularity platform uses AI to stitch events together into attack storylines. Instead of presenting isolated alerts, it shows how actions connect across endpoints, users, and systems.
QRadar combines traditional SIEM capabilities with AI-assisted analysis to help teams understand complex incidents faster. It correlates events across systems and adds intelligence to support root-cause analysis.
This platform fits structured, enterprise environments where investigations must be thorough, repeatable, and defensible during audits.
Key Features
- AI-assisted event correlation
- Centralized SIEM and EDR visibility
- Threat scoring and prioritization
- Long-term log retention
- Compliance-ready investigations
10. Elastic Security (Investigation and Response)
Elastic Security applies machine learning to detect unusual patterns in massive datasets. Its strength lies in fast search, flexible analytics, and customizable detection logic.
It works best for teams that want visibility and control rather than prescriptive workflows. AI assists discovery, but teams decide how detection and response evolve.
Key Features
- ML-based anomaly detection
- High-speed search and investigation
- Flexible detection rules
- Open and customizable platform
- Scales with large data volumes
Conclusion
The most innovative AI-driven security tools of 2026 are designed not to take over existing Security Staff but to aid faster, calmer, and more effective decision-making and execution processes by helping you focus on Security Data summarization, prioritization, and contextualization.
These tools clearly belong to this category since they allow the users to first understand their Security Data rather than just continuously generating additional Security Data. As Security Complexities continue to grow, Security Analysis Tool’s primary role will focus on providing context rather than just notifying you when something goes wrong.
FAQs
Q- What is an AI-powered security tool?
Ans- AI-powered security tools use machine learning and automated analysis to find threats in logs, network traffic, endpoints, and identity systems. They look for patterns and odd behavior that simple rules might miss, and they help teams group related alerts so analysts can act faster.
Q- How do AI security tools improve threat detection and response?
Ans- They reduce noise and speed triage. AI groups related events, spot unusual behavior, and rank alerts by risk so your team spends time on real problems. Many tools also suggest next steps or automate simple responses, which cuts the time from detection to action.
Q- How do I choose the right AI security tool for my business?
Ans- Pick a tool that fits your data and your team. Use this quick checklist.
- Can it ingest logs and telemetry from your key systems?
- Does it reduce false positives in real use, not just in demos?
- Can it explain why it flagged an alert?
- Does it play well with your SIEM, IAM, ticketing, and cloud tools?
- Can you run a short POC and measure time saved and alert quality?
Q- What types of security data do AI-powered security tools analyze?
Ans- Most AI security tools analyze logs from endpoints, identity systems, cloud platforms, networks, and applications. The strongest tools correlate multiple data sources together, so identity activity, endpoint behavior, and cloud access are viewed as part of the same security story.




