Detect, Prevent and Respond to Data Breaches
Many data breaches are preventable. Lepide enables organizations to take significant measures to prevent, detect and respond to breaches faster than other security vendors.














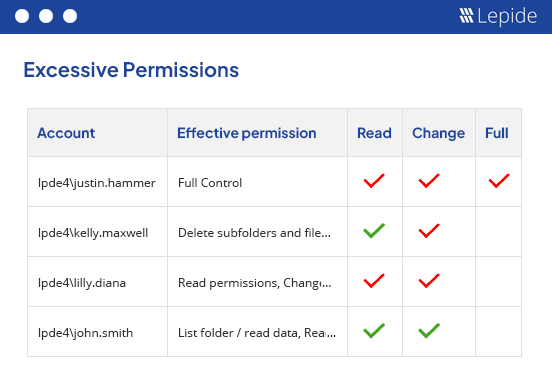
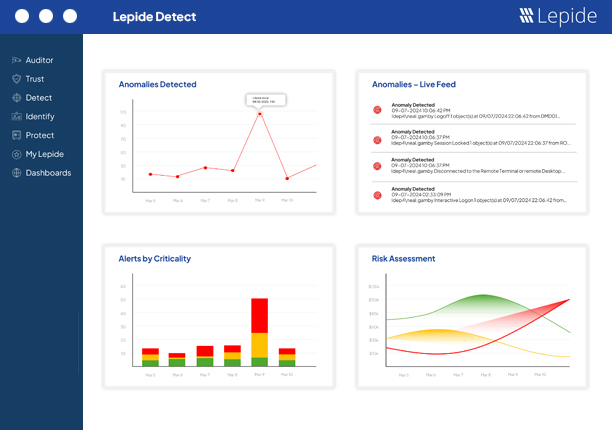
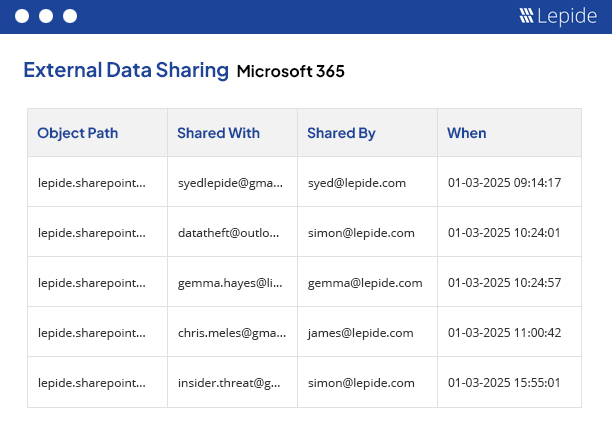
Identify the compromised user and what they have access to
See how the source of the breach gained access to data
Identify which data has been moved, copied or deleted
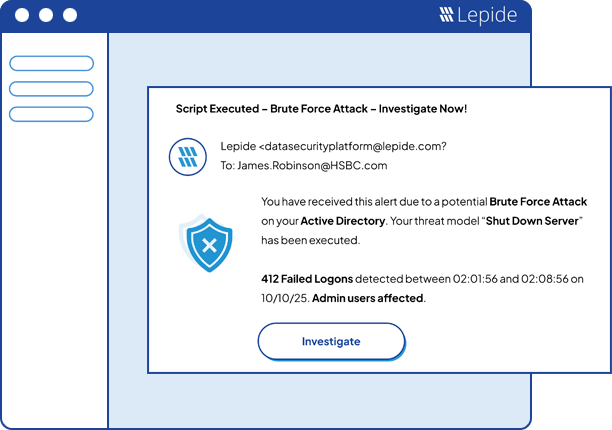
A guided tour of the Lepide Data Security Platform, your ultimate solution for robust and proactive data and identity protection.
View recording