Know the Signs of Compromised Users and Take Action
If privileged users have their accounts compromised, your sensitive data will be at risk. Instantly detect and react to the signs of compromised users to mitigate risks to your sensitive data.














There are numerous ways you can detect potentially compromised users. However, without Lepide, doing this can be incredibly difficult, unreliable and will not enable you to react quickly enough to mitigate any damages. With Lepide, you will be able to easily detect compromised users and react quickly, preventing them from doing any damage to critical infrastructure or sensitive data.
Get alerts in real time for anomalous behavior that could indicate a compromised user, including changes in logon activity.
Ensure passwords are rotated consistently to prevent attackers from having uninterrupted access to systems and data.
Upon detection of unwanted changes, execute automated scripts to take appropriate remediation action.
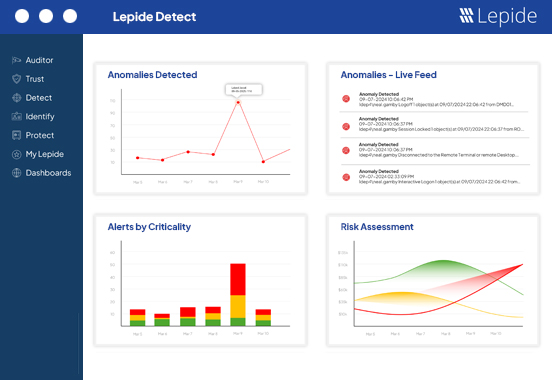
When a user’s behavior changes suddenly, and they start interacting with data in ways they never have before, this could indicate the account has been compromised. Lepide detects anomalies in user behavior automatically and alerts you in real time with detailed breakdowns of what is happening.
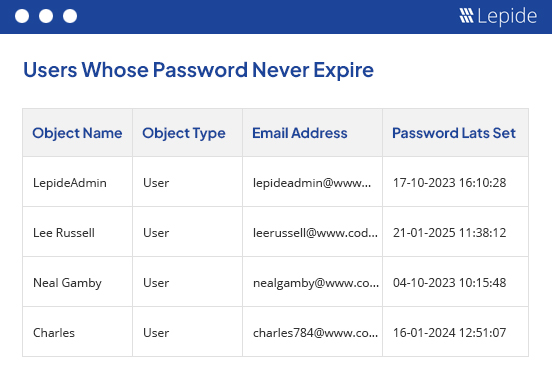
If your password is set to never expire, and an attacker gains access to your user account, they will have access indefinitely and be free to cause serious harm. Lepide enables you to report on users with passwords set to never expire and remind users to reset passwords regularly. You can also lock users out if passwords are entered incorrectly a certain number of times.
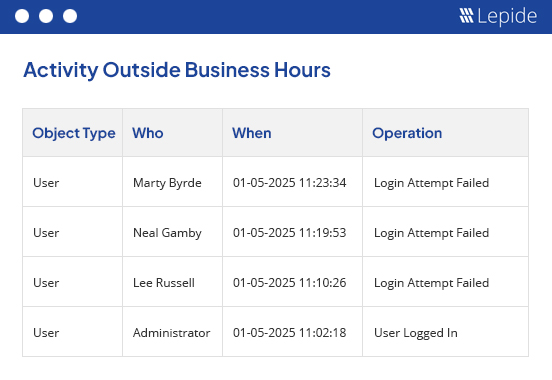
If you notice that a user logs on outside of business hours, or outside of their normal pattern, it could indicate that they have been compromised or plan to act maliciously. With Lepide, you can spot anomalies in logon/logoff activity in real time so that you can respond quickly.
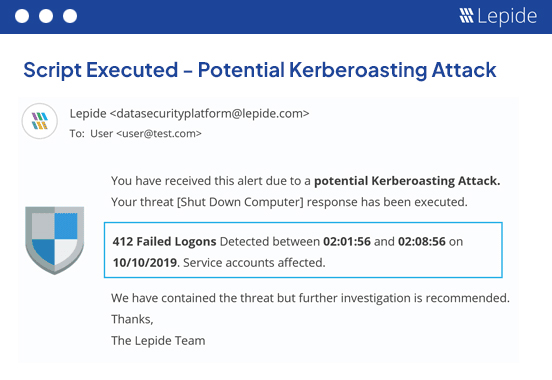
With Lepide, you can execute custom scripts whenever a change or anomaly takes place to contain the potential threat. For example, if a user copies files containing sensitive data for the first time, Lepide can automatically shut down the user account or computer from accessing the server. Quicker response means less potential damage to your business.
A guided tour of the Lepide Data Security Platform, your ultimate solution for robust and proactive data and identity protection.
View recording