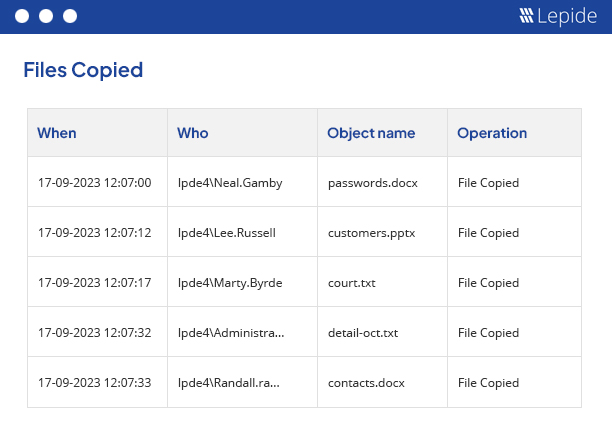
Complete file access monitoring software.
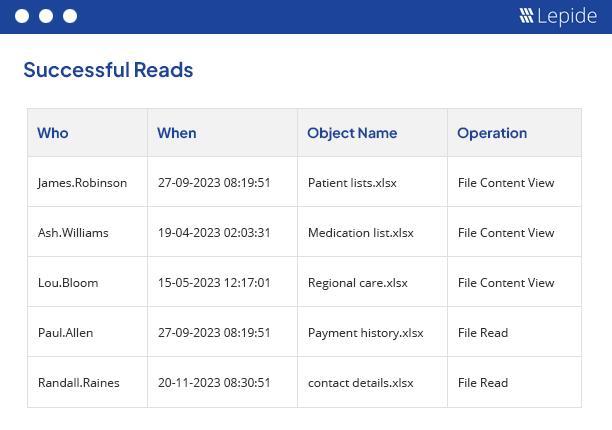
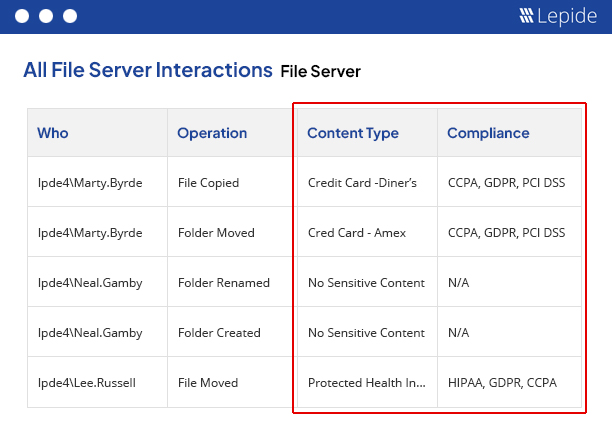
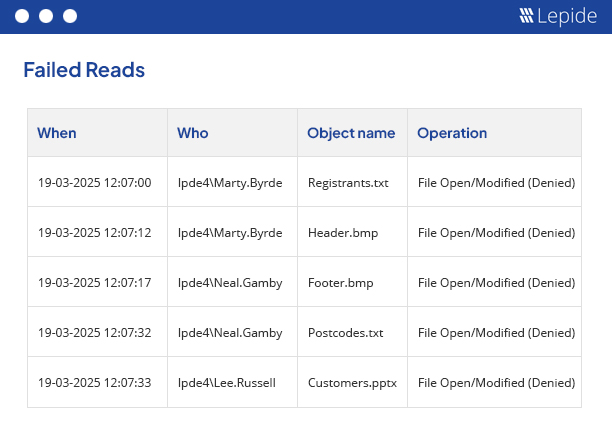
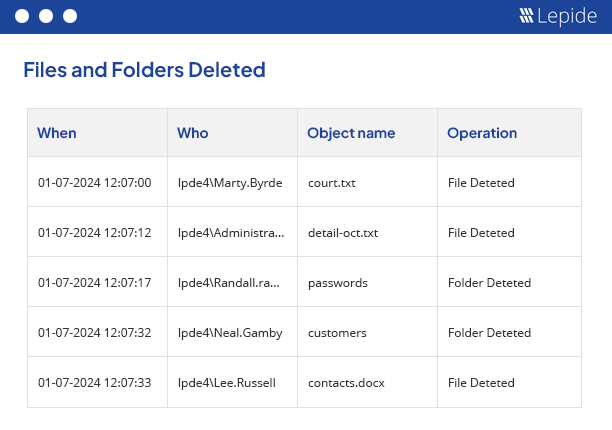
File Access monitoring needs to be undertaken to ensure the safety of critical data and to meet the increasing strictness of regulatory compliance. Whatever your driver, our file access monitoring software provides a simple and effective way of keeping a track of what’s happening to your files and folders. Track, alert and report on file access and permissions. Designed to work on both Windows File Servers and NetApp filers, our file access monitoring software will report on both successful and failed access attempts.