Google Workspace Auditing Software
Get insight into which users are accessing Google Workspace and the changes they are making.
Google Workspace is Google’s answer to a number of different productivity problems that impact many companies and organizations. In one suite of tools, it offers flexible, integrated and centrally managed solutions for email, word processing, spreadsheets, presentation decks, shared calendars and cloud-based storage. As it provides access to an organization’s most valuable systems and data, it’s important to monitor who is attempting to gain access to Google Workspace as well as what they are doing within the array of applications surrounding the most sensitive data within the organization.
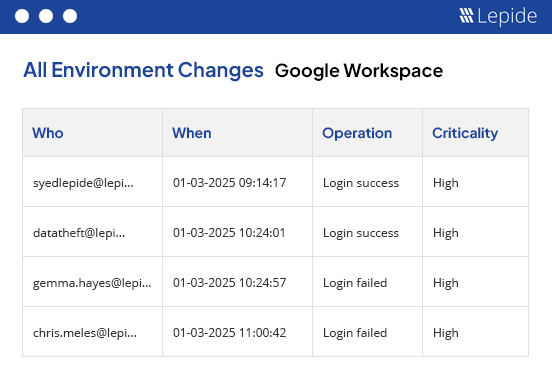
Understanding the logon activity of business users is critical in getting better insight into how and when your organisations employees are gaining access to your core systems and data. We also help you keep track of failed logins to Google Workspace to better understand if there could be a potential security risk or someone is trying to gain access with invalid credentials.
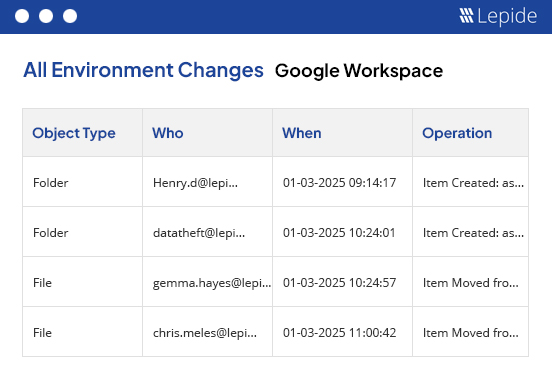
If you are providing access to your companies most sensitive data through Google Drive, then it’s important to understand who interacting with that data. Through creations, deletions, modifications and altering access via permission changes, we help by giving you better insight across your shared data.
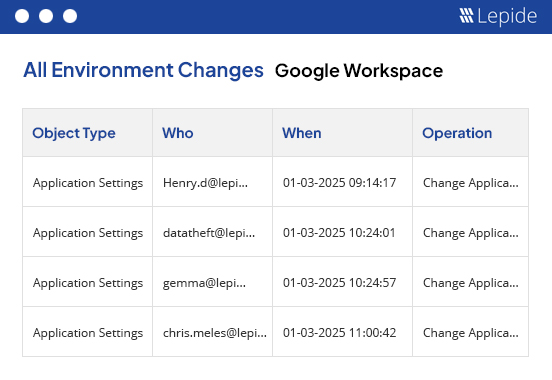
Just as its important to understand how your business users are interacting with the data and the surrounding applications with Google Workspace, you should easily be able to identify how and when users are being given access. Administrators or privileged users hold all the keys to the applications, Lepide Google Workspace Auditor can help you keep account of all administrative activities from privilege escalation to system configuration change ensuring the applications and data are available only to the people who actually need access.
A guided tour of the Lepide Data Security Platform, your ultimate solution for robust and proactive data and identity protection.
View recording