AI-backed threat models, real time alerting, and automated response. Built for IT teams securing hybrid environments.
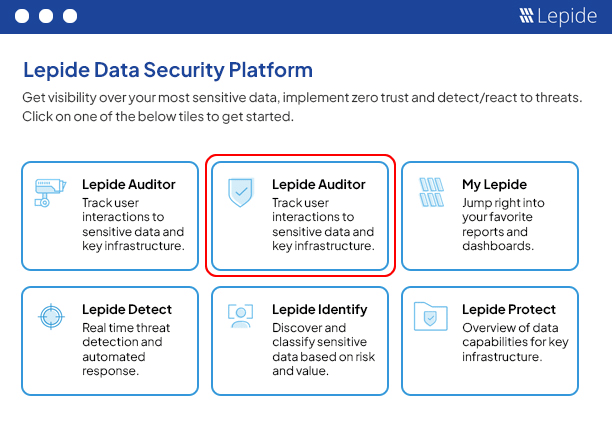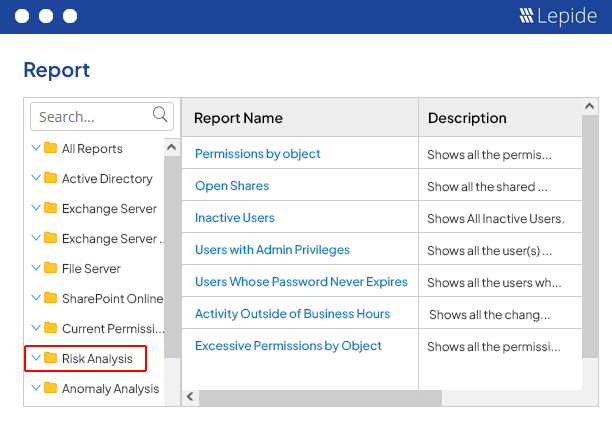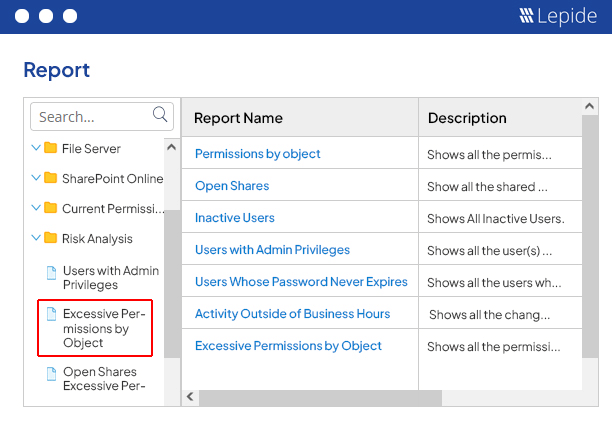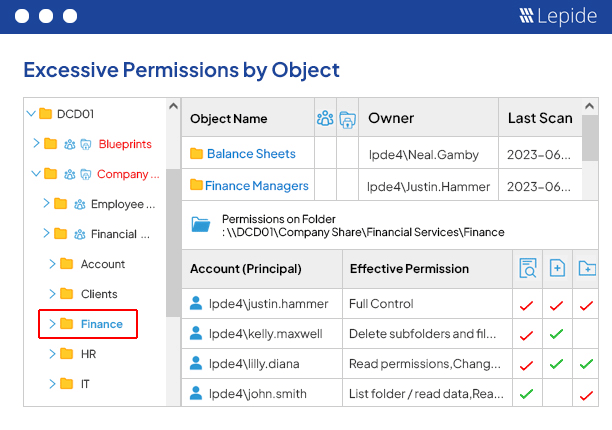
Lepide Detect uses AI-backed technology to automate the detection of security threats and unwanted or suspicious user behavior in real time. Speed up detection of insider threats, compromised user accounts, ransomware, brute force attacks, and privilege creep to avoid damaging security breaches.
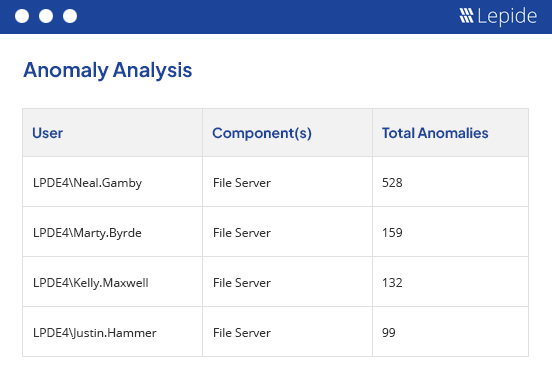
Detect anomalies in user behavior.
Lepide Detect will automatically detect anomalies in user behavior, whether it is copying files with sensitive data, logging into the server out of hours, or simply acting strangely based on learned behavior. The solution uses AI technology to learn what the normal behavior of your users looks like and then can generate real time alerts whenever that behavior changes.
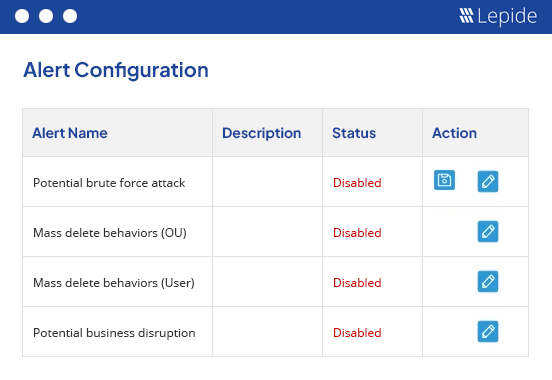
Deploy pre-defined, AI-driven threat models.
Pre-defined threat models detect a wide range of known security threats and will alert you in real time the instant a threat has been detected in your critical systems. Simply activate the threat model, and Lepide Detect will work in the background to ensure that no security threat goes unnoticed by your team.
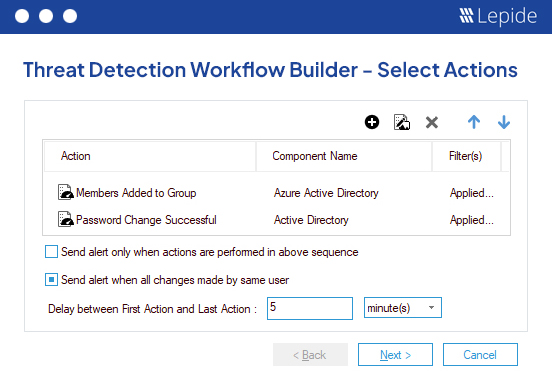
Advanced AI-led threat detection workflows.
Lepide Detect will allow you to chain events together across multiple systems / data stores to identify threats based upon certain attack paths. By doing this, you can configure threat detection workflows for specific known threats that follow the same pattern of events across your systems and data stores. This will drastically improve the effectiveness of your overall threat detection and response strategy.