Detect Ransomware In Your Core IT Systems
The only way to truly defend against ransomware is to keep software up-to-date, take regular backups, secure your network with an endpoint security solution and audit your IT environment. Here at Lepide, our focus is on providing you visibility over what’s happening with your data. Through visibility, you can speed up the detection of potential ransomware and automate your response. Detect and react quicker to ransomware using Lepide.
 Detect suspicious changes.
Detect suspicious changes.
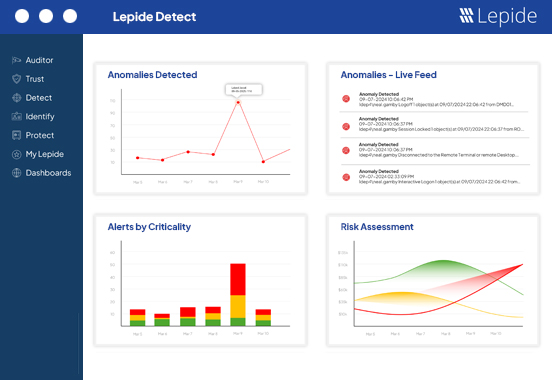
Get real time alerts for suspicious changes being made that could indicate a ransomware attack in progress.
 Reverse unwanted changes.
Reverse unwanted changes.
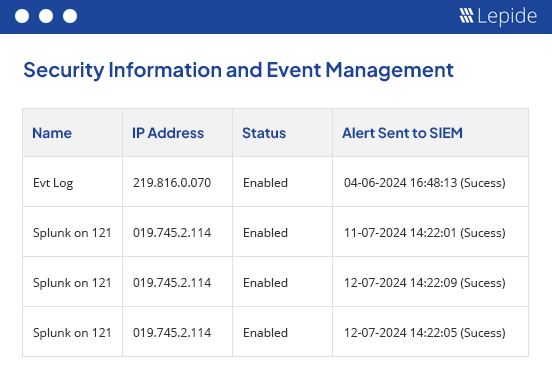
Find out who has access to your data and how it was granted, so that you can ensure proper data access governance.
 Automate response.
Automate response.
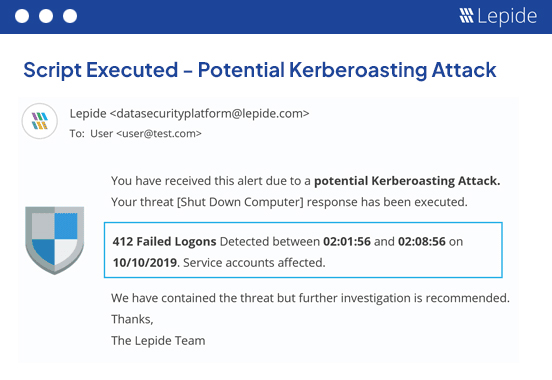
Upon detection of unwanted changes, execute automated scripts to take appropriate remediation action.