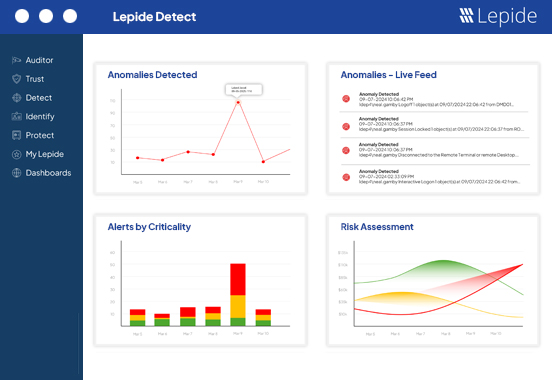
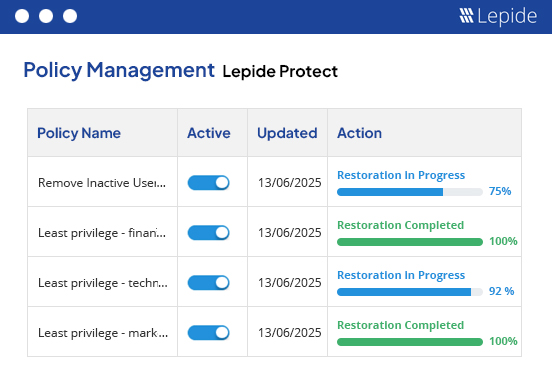
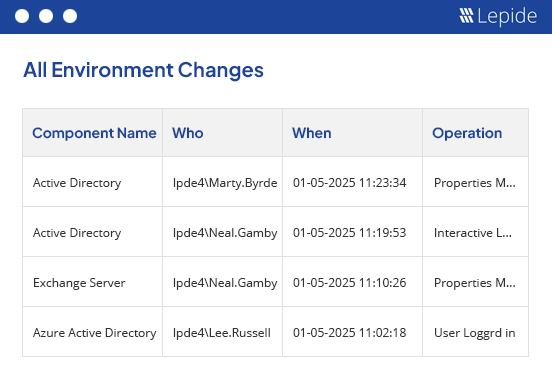
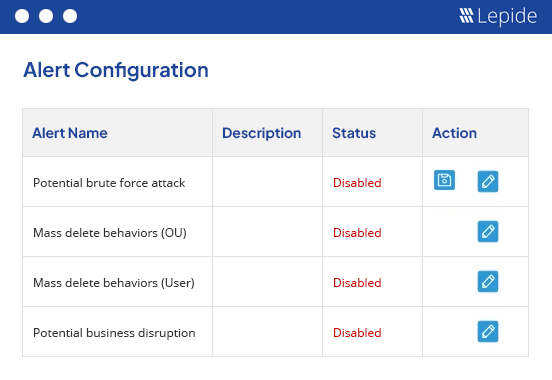
Detect and prevent insider threats.
Protect your organization from malicious, negligent, and compromised insiders through proactive auditing, user behavior analysis, and automated threat response.
Fill in the rest of the form to
download the 20-day free trial
download the 20-day free trial
x