Lepide Trust
Permissions Analysis Solution
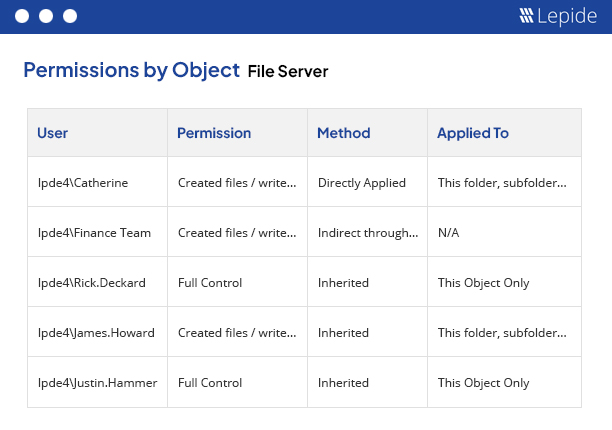
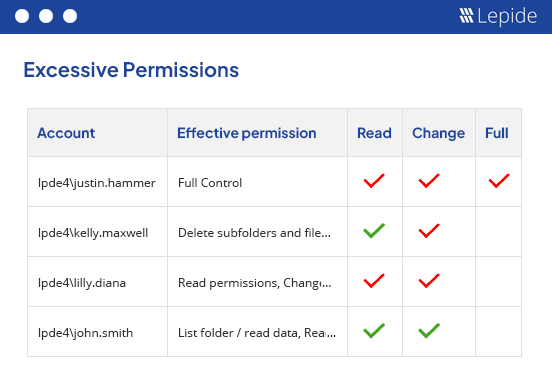
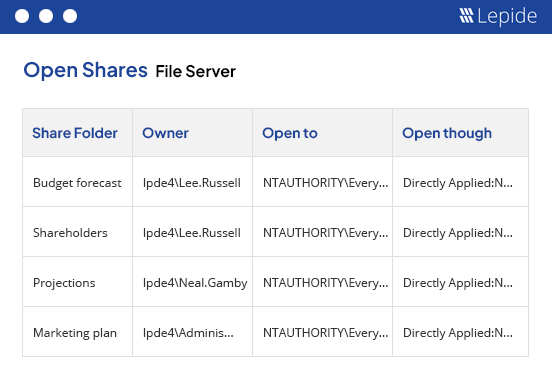
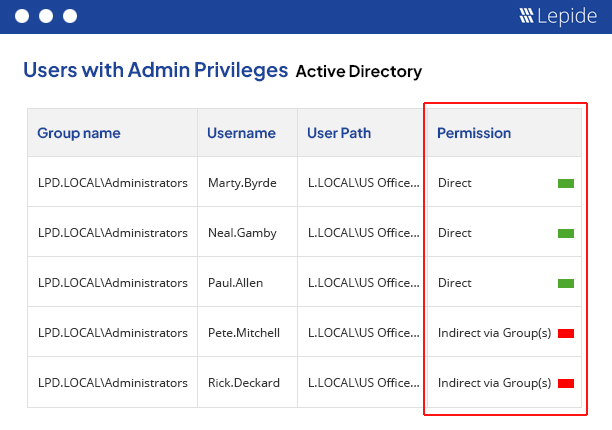
Get instant visibility over the changes being made to permissions and use AI to determine users with excessive permissions and implement zero trust.
Fill in the rest of the form to
download the 20-day free trial
download the 20-day free trial
x