Lepide Change Reporter
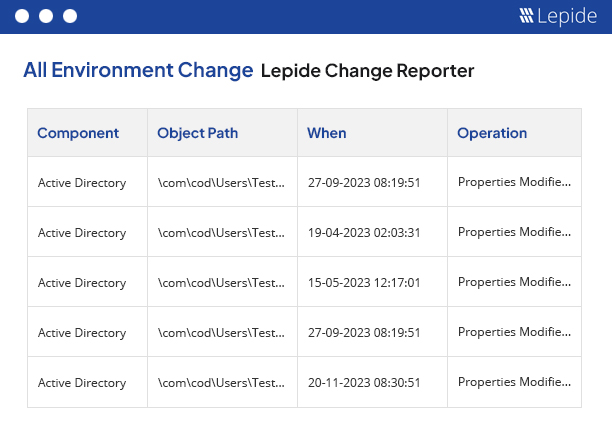
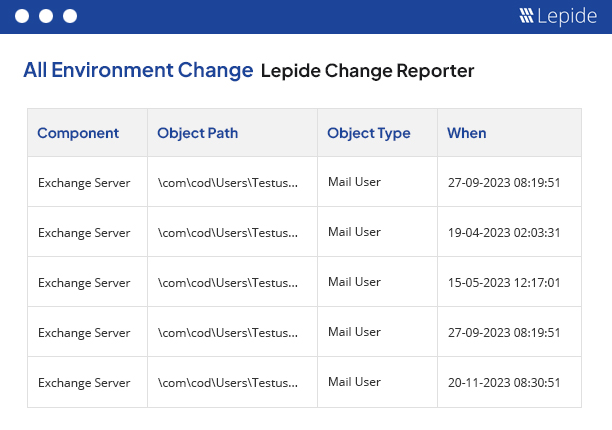
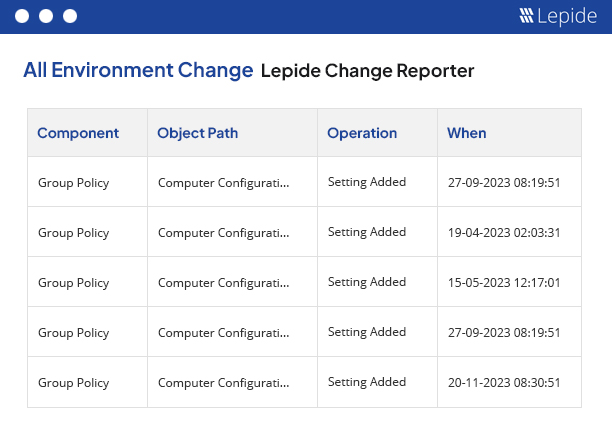
Get visibility over the changes being made to your critical IT infrastructure with the Lepide Change Reporter. Monitor and report on changes to Active Directory, Group Policy and Exchange Server for free.
Thousands of companies use Lepide to simplify their data security.














Download the free tool now!
By downloading you agree to the terms in our privacy policy.