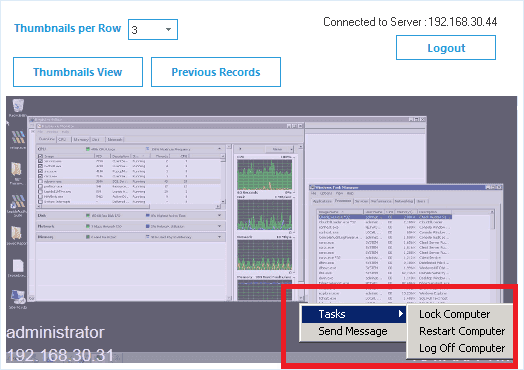
Warn, Shut Down, Or Restart in an Emergency
Send instant messages to users to warn them of unwanted behavior, and, if necessary, turn off, restart or shut down their computer if you notice behavior that may affect your data security.
Easily Delegate Viewing Rights
The tool can be installed on any system (including floating laptops), and admins can delegate viewing rights to any user easily through the tool itself. Rights to view specific monitors can also be delegated.
Dual Screen Monitoring
Unlike some of our competitors, we allow you to monitor and record activities on dual monitors, including on floating devices – providing separate recordings for each monitor.