Sensitive data doesn’t disappear when you migrate to the cloud. It multiplies, spreads across file servers, inboxes, SaaS apps, databases, and endpoints, then quietly waits to be misused.
This list covers 10 data security platforms that help organizations discover sensitive data, understand access risk, and prevent exposure. Each tool solves a different part of the problem. The trick is knowing which one actually fits your environment.
Top 10 Data Security Platforms
Below is a curated list of the top data security platforms that help organizations discover sensitive data, reduce exposure, and protect information across on-premises and cloud environments.
- Lepide Data Security Platform
- Microsoft Purview Information Protection
- Varonis Data Security Platform
- Thales CipherTrust Data Security Platform
- Imperva Data Security
- Velotix
- IBM Guardium
- Forcepoint Data Loss Prevention
- Symantec Data Loss Prevention
- Fortra Digital Guardian
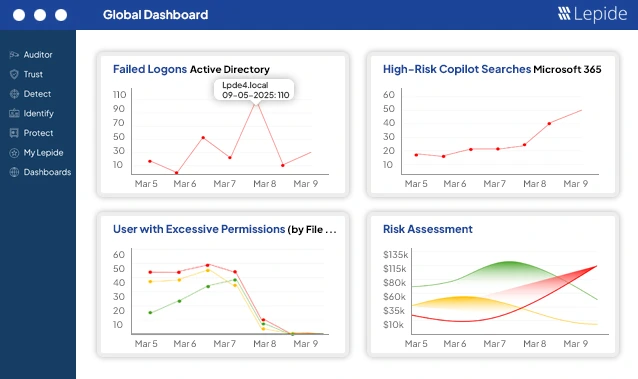
1. Lepide Data Security Platform
Lepide is designed to answer three questions quickly: Where is sensitive data? Who can access it? What risky changes are happening right now? The platform continuously scans file servers, Active Directory, and Microsoft 365 to identify sensitive data and monitor access behavior. Instead of raw logs, it provides clear alerts and timelines that help security teams investigate incidents and prove compliance without manual effort.
What makes Lepide stand out is its focus on clarity and speed over heavy tuning and complex telemetry. Instead of flooding teams with raw data, Lepide delivers pre-configured discovery for file servers, Active Directory, and Microsoft 365, along with context-rich alerts and investigation timelines that quickly show who accessed what and when. This allows security teams to reduce noise, respond faster, and generate audit-ready evidence without the operational overhead common in more complex DSP tools.
Lepide is especially useful in environments where file data and identity sprawl create blind spots. It focuses on clarity and speed, not complex tuning.
Key Features
- Sensitive data discovery and classification across file systems and Microsoft 365
- Continuous monitoring of access, permission changes, and user behavior
- Real-time alerts with full context for investigations
- Built-in reports for audits, compliance, and incident response
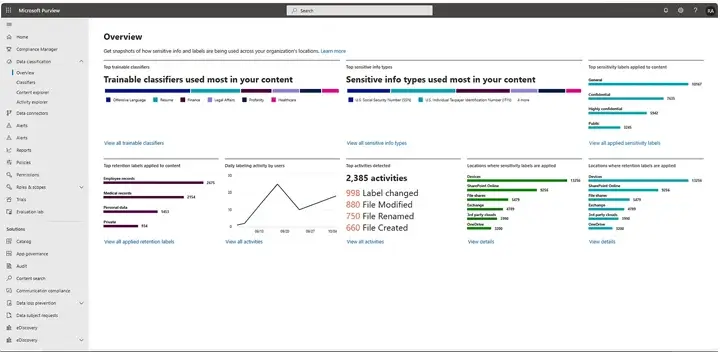
2. Microsoft Purview Information Protection
Microsoft Purview Information Protection is about controlling your data through classification and labelling. When you classify your data and assign a label, security policies are applied to the file, wherever it goes, and enforce Encryption, Access Control Restrictions or Limits to Share. Microsoft Purview is built into Microsoft 365, so users can easily apply Protection while using familiar tools such as Word, Outlook, and SharePoint.
Microsoft Purview is best suited for businesses that primarily use Microsoft 365 for their data storage and need native control as opposed to using third party products.
Key Features
- Persistent labels that remain attached to files and emails
- Automated classification using rules and machine learning
- Built-in encryption and sharing restrictions
- Deep integration with Microsoft 365 services
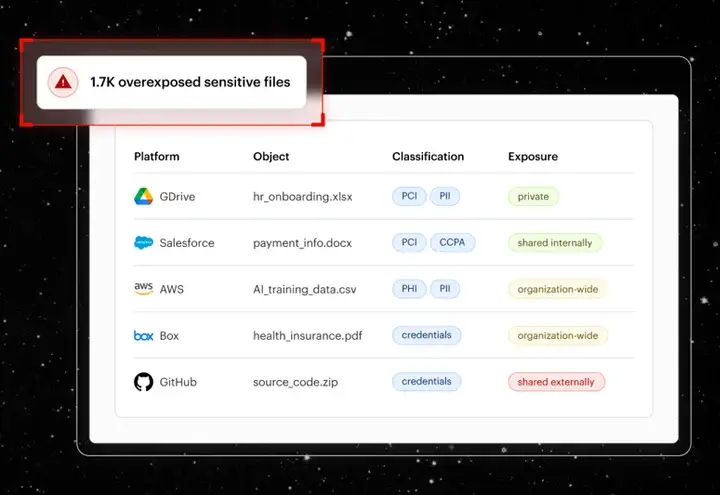
3. Varonis Data Security Platform
Varonis helps companies understand their data exposure and access risk by scanning their environments for any exposed sensitive data, mapping who can access that data, and calculating how much damage a compromised user account could cause to an organization. It also uses user behavioral analytics to identify anomalies of user activity that can point toward insider threats, as well as other potential indicators of ransomware and compromised credentials.
Companies large enough to have accumulated years of file sprawl and who have granted excessive permissions to too many users often choose Varonis.
Key Features
- Automated discovery and classification of sensitive data
- Access mapping and exposure analysis
- User behavior analytics to detect suspicious activity
- Guided remediation to reduce unnecessary access
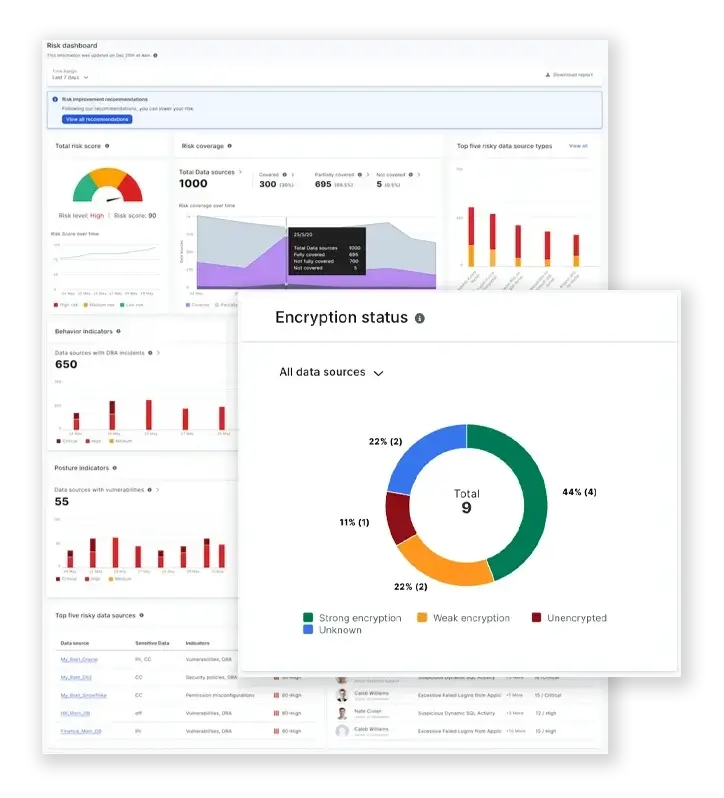
4. Thales CipherTrust Data Security Platform
CipherTrust focuses on using encryption along with the control of cryptographic keys. Organizations can utilize CipherTrust to encrypt data on multiple platforms such as databases, files, containers, and cloud-based services, while at the same time maintain the centralized control over the customer’s cryptographic keys. CipherTrust provides organizations that are mandated by law to provide evidence of data confidentiality to regulators, or to ensure the service providers cannot have access to the protected data through encryption.
CipherTrust does not focus on how to monitor user behaviours; instead it is geared towards creating approximately the same level of security at a crypto-level.
Key Features
- Centralized encryption key and policy management
- Encryption and tokenization for structured and unstructured data
- Support for hybrid and multi-cloud environments
- Detailed audit logs for regulatory compliance
5. Imperva Data Security
Imperva Data Security offers insight and security for database storage and cloud storage platforms, as well as monitoring database activity and providing analytical tools to help identify potential misuse, weak controls, or suspicious access patterns. The system is also used to secure mission-critical databases while ensuring compliance across various hybrid environments.
Imperva is a great match for companies that store and manage high-value or regulated data on their databases.
Key Features
- Discovery and classification across databases and cloud stores
- Activity monitoring with risk-based analytics
- Centralized policy enforcement
- Data masking for non-production environments
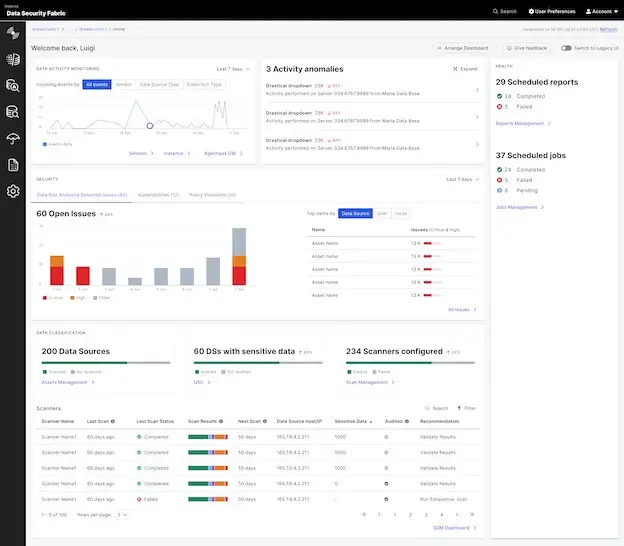
6. Velotix
Velotix focuses on governing access to data rather than locking it down completely. It discovers data across platforms, maps relationships, and automates access approvals so teams can use data safely. The platform is designed for modern analytics-driven organizations where fast access must coexist with security and accountability.
Velotix is particularly relevant for data teams working with cloud warehouses and analytics platforms.
Key Features
- AI-driven discovery and data cataloging
- Visual mapping of data lineage and access paths
- Automated access approvals and enforcement
- Integrations with modern data platforms
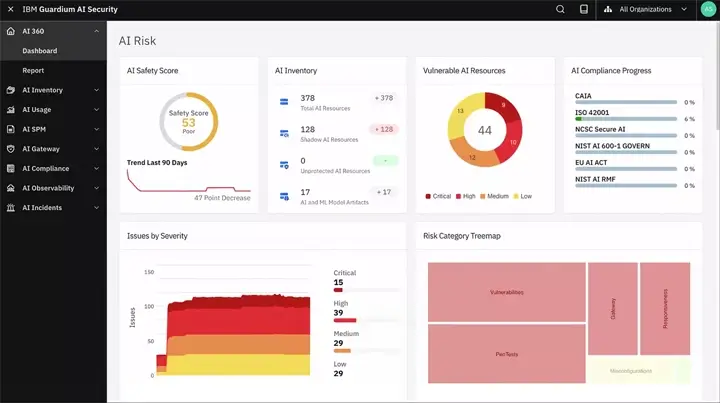
7. IBM Guardium
IBM Guardium is an enterprise-grade data security platform that specializes in monitoring, detecting, and integrating threats and security operations into an organization’s operations. Guardium is used throughout multiple industries, but its primary focus is on regulated industries that need detailed audit reporting and compliance enforcement capabilities.
While Guardium has a lot of features and strengths, it may not provide an organization with enough tools or capabilities to manage security effectively if they have a less mature security team.
Key Features
- Continuous discovery and classification of data
- Real-time monitoring of database activity
- Policy-driven alerts and automated responses
- Integration with SIEM and incident response tools
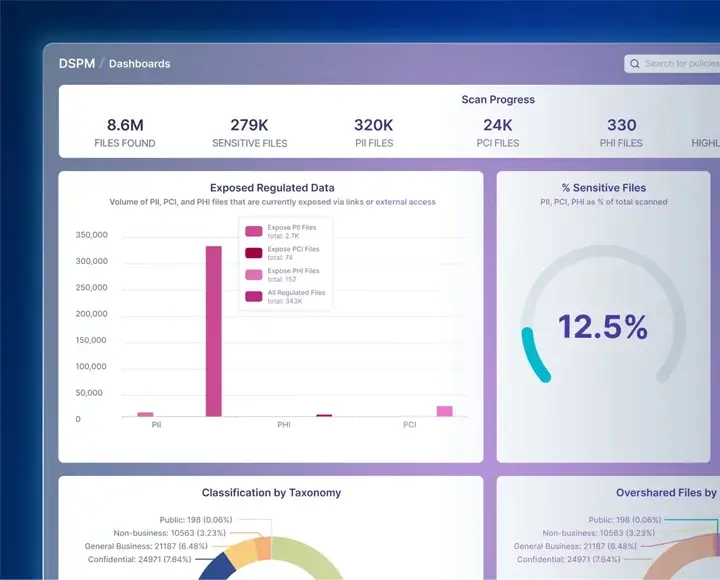
8. Forcepoint Data Loss Prevention
Forcepoint DLP protects sensitive data as it moves across endpoints, networks, and cloud applications. It combines traditional DLP controls with behavior analytics to reduce noise and improve incident prioritization. Organizations can choose between cloud-based or on-prem deployments.
Forcepoint works well for organizations focused on preventing accidental or intentional data leakage.
Key Features
- Endpoint, network, and cloud DLP coverage
- Pre-built classifiers and policy templates
- Risk-based incident prioritization
- Flexible deployment options
9. Symantec Data Loss Prevention
Symantec DLP is one of the leading enterprise DLP solutions. The solution provides monitoring and control over sensitive information across email, endpoints, networks and cloud. The product also has strong scalability and customizable policies to meet the unique requirements of large enterprises that are more complex.
While, like many DLP solutions, Symantec DLP needs to be tuned to achieve maximum effectiveness, it is an effective DLP solution when deployed in a large scale environment.
Key Features
- Multi-channel data discovery and protection
- Centralized policy and incident management
- Scalable architecture for large organizations
- Detailed compliance and investigation reports
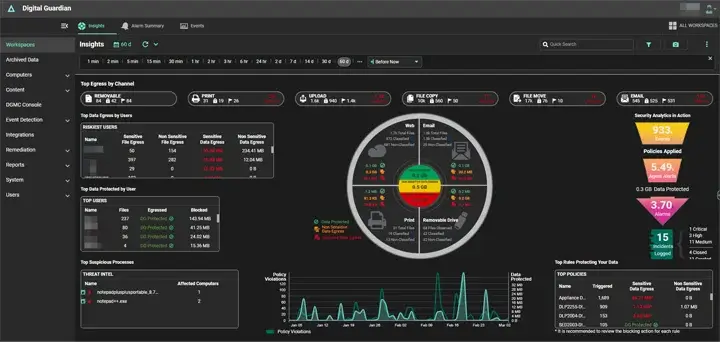
10. Fortra Digital Guardian
Digital Guardian focuses on endpoint visibility and insider risk prevention. Its agents monitor detailed user activity on devices and allow organizations to block, alert, or monitor actions based on risk. This makes it effective for stopping data theft before files ever leave the endpoint.
Digital Guardian is often chosen when insider threats are a primary concern.
Key Features
- Deep endpoint monitoring and control
- Network and cloud DLP integration
- Flexible response actions based on risk
- Managed service options for faster deployment
Conclusion
Data security can be achieved through a combination of solutions that provide different levels of insight, authority, and action. By identifying sensitive information first they can minimize their exposure by making corrections to who has access to that information.
At that point, either DLP (data loss protection) or encryption can be applied where there is sufficient risk to warrant the need for protection. This methodology assists companies from spending money unnecessarily and helps to avoid creating security gaps.
FAQs
Q- What’s the difference between DSPM, DLP, and encryption solutions?
Ans– DSPM (Data Security Posture Management) discovers and maps sensitive data, highlights exposures, and prioritizes fixes. DLP (Data Loss Prevention) enforces rules that block or control data movement (endpoints, network, cloud). Encryption platforms (or KMS solutions) protect data by cryptographically controlling access to content and keys. Many mature programs combine discovery (DSPM), enforcement (DLP) and encryption for layered protection.
Q- Which tool is best for file servers and Microsoft 365 visibility?
Ans– Tools like Lepide emphasise file-server and Microsoft 365 visibility and provide continuous monitoring and audit reporting. Varonis also focuses on file shares and access mapping at scale. Choose based on depth of integration and reporting needs.
Q- How do I evaluate vendor ROI and operational cost?
Ans– Compare license fees plus operational effort: agent footprint, policy tuning time, false-positive handling, and integration effort. Ask vendors for a realistic TCO breakdown and proof points from similar customers.
Q- How do these tools help with audit and compliance?
Ans– Discovery tools create inventories and exposure reports; DLP and encryption solutions log enforcement actions. Together they produce auditable trails showing who accessed data, what actions were taken, and why a control was applied, speeding audit responses and reducing ad-hoc evidence collection.




