NTFS permissions rarely fail loudly. Instead, they degrade quietly over time.
As file servers evolve, access control lists (ACLs) accumulate inherited permissions, security groups sprawl, and exceptions pile on top of exceptions. The result is an environment where access is technically “working,” but no one can confidently answer basic questions like who can access what, why they have access, or whether it’s still appropriate.
This lack of visibility only becomes urgent during an audit, security incident, or ransomware investigation, when teams are forced to untangle years of unmanaged permissions under pressure. At that point, manual reviews and native tools quickly fall apart at scale.
Dedicated NTFS permissions management tools exist to solve exactly this problem. They help administrators understand effective access, identify risky or excessive permissions, track changes over time, and safely remediate issues across large file systems.
In this article, we review 10 of the most effective NTFS permissions management tools in 2026, commonly used by system administrators, auditors, and security teams, to help you compare capabilities, strengths, and ideal use cases.
Top 10 Most Effective NTFS Management Tools
The following tools focus specifically on understanding, auditing, and managing NTFS permissions on Windows file servers. Some are designed for quick, ad-hoc visibility. Others support continuous auditing, historical tracking, or large-scale permission cleanup. Together, they represent the most commonly used NTFS permissions solutions by administrators, auditors, and security teams today.
- NTFS Permissions Reporter (CJWDEV)
- Lepide Data Security Platform
- Netwrix Effective Permissions Reporting Tool
- Varonis DatAdvantage for File Systems
- ManageEngine ADManager Plus (NTFS Permissions Management)
- SolarWinds Access Rights Manager
- NETsec – Permission Reporter (Enterprise Permission Reporter)
- FileAudit by IS Decisions
- Permission Analyzer
- Vyapin NTFS Change Auditor
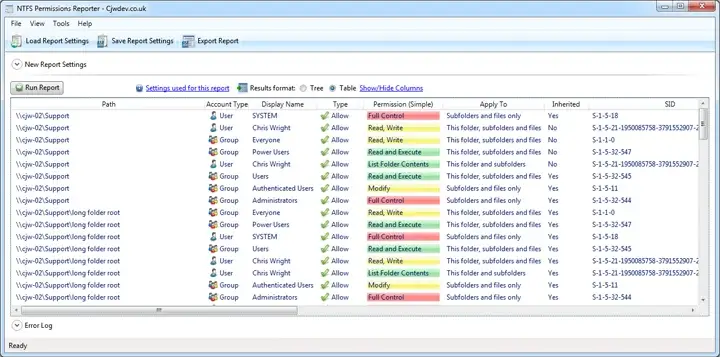
1. NTFS Permissions Reporter (CJWDEV)
The Permissions Reporting Tool from CJWDEV is an easy-to-use, effective method for viewing user permissions with minimal impact on performance. The tool uses a snapshot approach to scan the directory tree and output detailed ACL reporting that can be used for manual remediation planning or for audits.
This tool is often employed by consultants and used in many one-off assessments for both internal and external clients.
Key Features
- Recursive NTFS permission scans
- Effective access calculations
- Excel and CSV exports
2. Lepide Data Security Platform
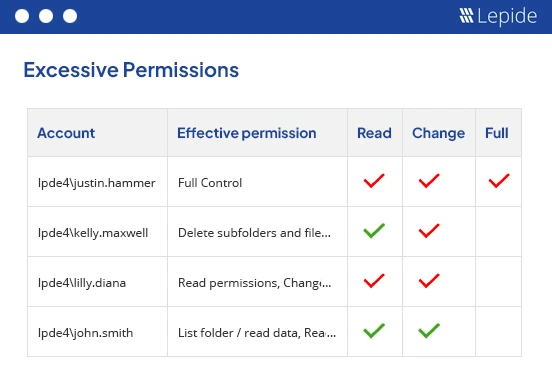
Lepide Data Security Platform approaches NTFS permissions as part of a broader identity and data exposure problem. Instead of treating permissions as static ACL entries, Lepide correlates NTFS permissions with identities, group memberships, and actual access behavior.
In practice, Lepide helps teams answer the uncomfortable questions quickly. Who can access this folder right now? Why do they have access? When did it change? It also highlights excessive, inherited, and orphaned permissions so cleanup efforts can focus on real risk instead of guesswork. This makes Lepide particularly useful for organizations that need both audit-grade visibility and ongoing permission governance without stitching together multiple tools.
Key Features
- Effective NTFS permission and access visibility through Lepide Trust
- Continuous monitoring of permission and access changes/li>
- Identification of excessive, inherited, and orphaned permissions
- Contextual timelines for permission change investigations
- Compliance-ready and executive-friendly reporting
- Centralized platform suitable for hybrid and large environments
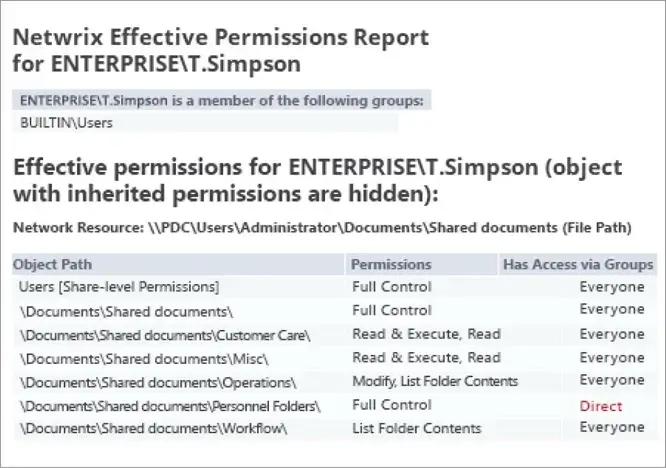
3. Netwrix Effective Permissions Reporting Tool
Netwrix’s Effective Permissions Tool is a focused, free tool to help you quickly see who can access your files. This application combines Active Directory (AD) group memberships and file share access control lists (ACL) to show how a user accesses a file; that is, either through inherited or explicit permission. This application is designed for quick ad-hoc checks of effective permissions and short audits of file shares.
Key Features
- Effective access reports across AD and file shares.
- Shows explicit vs inherited permissions and permission source.
- Fast scans and exportable reports (HTML/CSV).
- Lightweight, free tool for quick remediation planning.
4. Varonis DatAdvantage for File Systems
Varonis approaches NTFS permissions as a data exposure problem rather than a configuration problem. It builds a comprehensive map of folders, permissions, group memberships, and effective access, then applies analytics to determine which permissions actually represent risk. This allows teams to prioritize remediation based on potential impact rather than raw permission counts.
Varonis is best suited for large corporations where the accumulation of permissions likely happened over many years. While it has a more extensive footprint than point tools, it serves as the primary platform for organizations wanting to implement a least-privilege model at scale.
Key Features
- Exposure mapping and effective permission analysis
- Analytics-driven identification of over-privileged access
- Owner discovery and guided remediation
- Long-term historical visibility
- Integration with data classification and security platforms
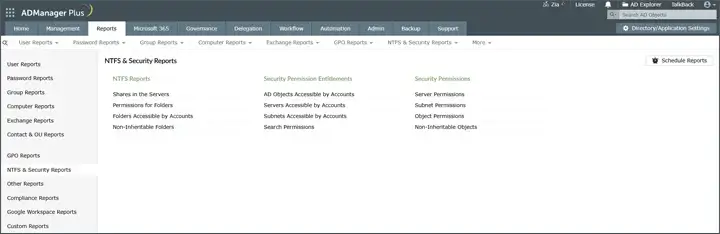
5. ManageEngine ADManager Plus (NTFS Permissions Management)
ADManager Plus expands Active Directory management to include NTFS permission reporting and bulk management functionality. This tool allows users to create multiple permission reports, delegate changes to those permission reports, and automatically make updates to multiple ACLs across file servers through the GUI rather than through a script.
Operational teams that require both analysis capabilities and the ability to take action can use this product. ADManager Plus does not focus on behavioral analytics or continuous monitoring; instead, it supports structured processes for managing permissions that facilitate efficient and consistent permission management.
Key Features
- NTFS and share permission reporting
- Bulk permission management and delegation
- Scheduled and exportable audit reports
- Role-based administration and approvals
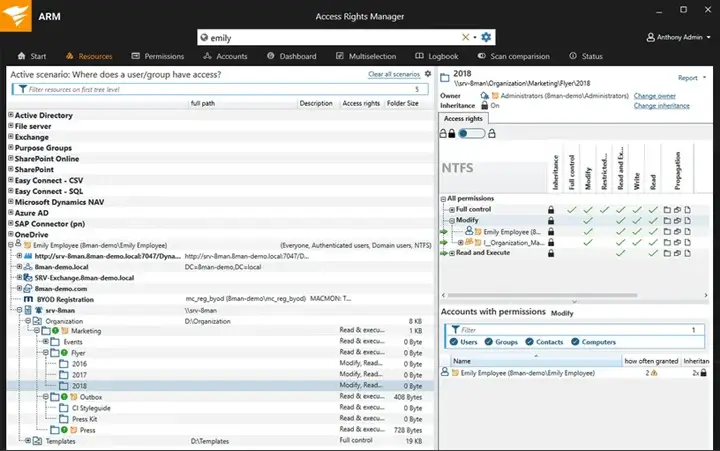
6. SolarWinds Access Rights Manager
The SolarWinds Access Rights Manager allows for centralized visibility into file server and Active Directory (AD) NTFS permissions and provides administrators with insight into the reasoning behind access by supporting the delegation of authority for actively granting or removing any identified NTFS permissions.
The tool has been widely adopted by organizations that operate under conditions where the ownership of file server NTFS permissions is not readily apparent, and therefore the ability to formalize ownership is required. SolarWinds Access Rights Manager allows for approval processes and various types of reporting to be created based on roles, which allows for the continuous governance of NTFS permissions, rather than just an audit for a particular point in time.
Key Features
- Effective permission visualization
- Centralized NTFS and AD access reporting
- Delegated permission management workflows
- Scheduled compliance reports
7. NETsec – Permission Reporter (Enterprise Permission Reporter)
NETsec Permission Reporter (often called Enterprise Permission Reporter) is an NTFS- and share-focused reporting solution that scans file systems, stores results in a SQL DB, and produces repeatable reports showing exactly who/what has which permissions. It’s built for environments that want scheduled, auditable snapshots and historical comparisons without heavy custom engineering.
Designed around permission reporting rather than monitoring noise, you get a database of permissions that you can query, compare over time, and export to PDF/CSV for owners/auditors. Good for organizations that run recurring permission reviews and need evidence of change.
Key Features
- Scheduled, profile-based scans of NTFS and share permissions.
- Stores results in SQL for quick historical comparisons and reporting.
- Multiple report views (file system perspective, security principal perspective).
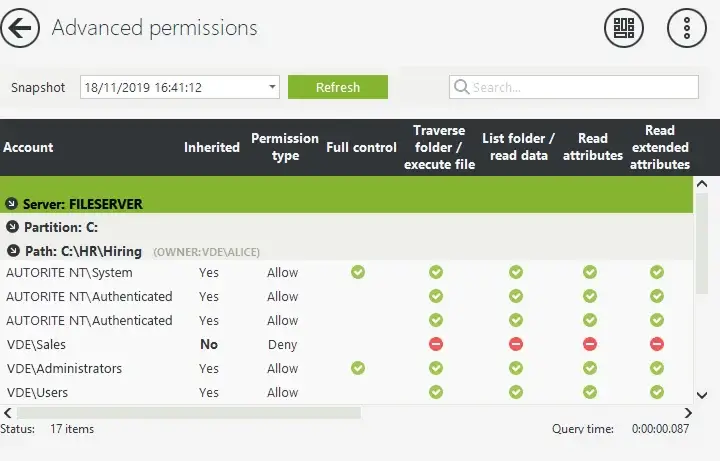
8. FileAudit by IS Decisions
FileAudit is a dedicated tool to track all file activity and modifications of permissions on a file server (Windows OS only). It logs all attempts to access files and operations performed against files and changes made to file ACL permissions, and data is displayed in an easily searchable format.
Typically, this type of solution can be best utilized by small-to-medium businesses and mid-sized organizations that want quick, straightforward answers from their systems, versus the complexities that can come with an Enterprise-level product. This tool can be beneficial for both investigative purposes and for complying with audits through the collection of documentation as evidence.
Key Features
- Real-time monitoring of file access and permission changes
- Custom alerts and searchable audit logs
- Exportable compliance reports
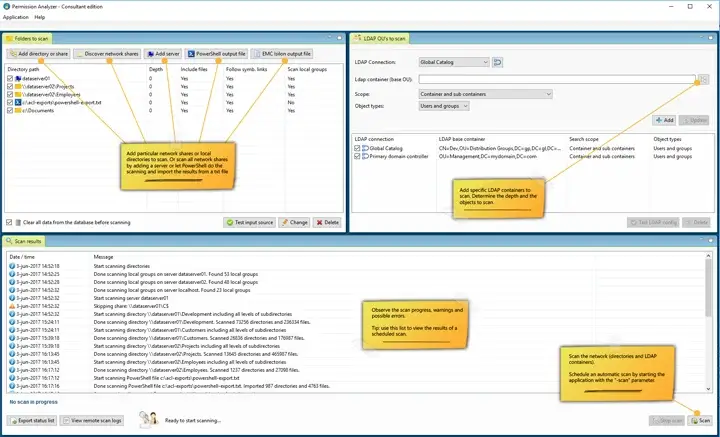
9. Permission Analyzer
Permission Analyzer is a specialist NTFS permissions tool that scans file systems, imports AD principal data, and builds an indexed database so you can run fast “who has access” queries without rescanning. It also supports making changes directly from the tool and scheduling jobs for repeatable audits.
Its indexed approach is perfect when you have large file stores and need repeated effective-permission lookups or owner discovery during incidents, instant query responses instead of waiting for rescans. It also supports scripted or UI-based permission changes.
Key Features
- Indexed scans for fast, effective-permission queries on large file systems.
- Combines NTFS permissions with AD user/group data for accurate trusteeship and owner resolution.
- Job scheduling, reporting and ability to change permissions from the interface.
10. Vyapin NTFS Change Auditor
This component tracks changes in the permissions and access of files. The historical records allow the teams to reconstruct the events associated with audits or investigations. This component provides an additional level of time-based access vs. static reporting to the existing NTFS (Windows NT file system) Security Manager utility.
Key Features
- Tracking of ACL and ownership changes
- Historical archives for audits
- Searchable change records
Conclusion
Although NTFS Permissions work great under most conditions, when they stop working the tools above represent a wide range of utility from lightweight/free tools used for triage through enterprise-level analytics and remediation platforms. The right tools will depend on your specific problem – for instance, using Diagnostic tools for quick checks, Reporting tools for scheduled governance, and Analytics platforms when you have a large estate with a strategic risk associated with Permissions debt. Establish a plan and run a Discovery scan first, then address the high-impact items by correcting/corrective action, and automate your checks so that Permission Drift won’t return!
FAQs
Q- What’s the fastest way to find out who has access to a Windows folder?
Ans- Run an effective-permissions report. For quick, ad-hoc checks use tools like Netwrix Effective Permissions Reporting Tool or CJWDEV’s NTFS Permissions Reporter. For continuous visibility and investigation-ready context, Lepide Data Security Platform provides effective access combined with change tracking and risk indicators.
Q- Do I need an agent to audit NTFS permissions?
Ans- Not always. Some tools work agentless by reading NTFS and Windows security data remotely. Others use agents to capture deeper metadata and real-time changes. Lepide Data Security Platform supports scalable auditing and monitoring using lightweight deployment options, making it suitable for environments that need continuous NTFS visibility without heavy performance impact.
Q- Which tool is best for small teams vs. enterprise environments?
| Company Size | Tool |
|---|---|
| SMB | CJWDEV NTFS Permissions Reporter, FileAudit |
| Mid-Size | Lepide Data Security Platform, ManageEngine ADManager Plus, SolarWinds Access Rights Manager, Vyapin |
| Enterprise | Varonis DatAdvantage, Lepide Data Security Platform, NETsec Permission Reporter for scheduled, database-backed reporting |
Q- What is NTFS permissions management?
Ans- NTFS permission management is the process of controlling, reviewing, and cleaning up who can access files and folders on Windows file systems. It goes beyond setting ACLs. It’s about knowing who really has access and why.
Q- What are the risks of poorly managed NTFS permissions?
Ans- Excess access, inherited permissions no one understands, and sensitive data exposed to the wrong people. Add failed audits, insider risk, and incident investigations that turn into guesswork.
Q- How do NTFS permissions management tools work?
Ans- They scan file systems, resolve group memberships, calculate effective access, and show permissions in a readable way. Better tools also track changes over time and highlight risky or unnecessary access.
Q- What features should an NTFS permissions management tool include?
Ans- Effective access reporting, visibility into inheritance and group paths, change tracking, clear reports, and the ability to clean up permissions at scale without breaking things.
Q- How do NTFS permissions tools help with compliance and audits?
Ans- They provide clear evidence of who has access, how it’s controlled, and when it changed. This turns audits from panic-driven folder digging into repeatable, defensible reports.




