We recently ran a survey with one question; which initiative is your IT/Security team prioritizing for 2026. 61% of respondents answered with Zero Trust and Least Privilege. What does this tell us about the world of cybersecurity, and how does Active Directory play the crucial role? Let’s explore.
What Sparked This Surge in Votes?
Our survey’s overwhelming support for Least Privilege and Zero Trust is consistent with what we’re witnessing throughout the industry. 81% of organizations are currently implementing or planning to implement Zero Trust as a foundational security model in response to increasingly sophisticated cyber threats.
Experts highlight the implementation of the Least Privilege essential since attackers frequently make use of accounts with excessive permissions to increase their access and cause more damage. As a result of generative AI being used to create more believable phishing campaigns, the need for going by the rules of the Least Privilege is getting more and more important to be able to still halt the spreading of such kinds of attacks.
Security professionals regularly put Zero Trust and Least Privilege on the top of their priority lists as the leading cause of big breaches is the theft of credentials most of the times. In fact, hackers use the stolen credentials to spread within the networks horizontally and to get higher privileges. Least Privilege reduces the risk in this way that it limits user access only to the necessary level for their role, whereas Zero Trust keeps on checking identity and context so that it can detect any kind of unauthorized access at the very beginning.
In 2025-26, organizations face intensifying cyber threats and rapid technological shifts; this survey explored their responses, with key findings presented below.
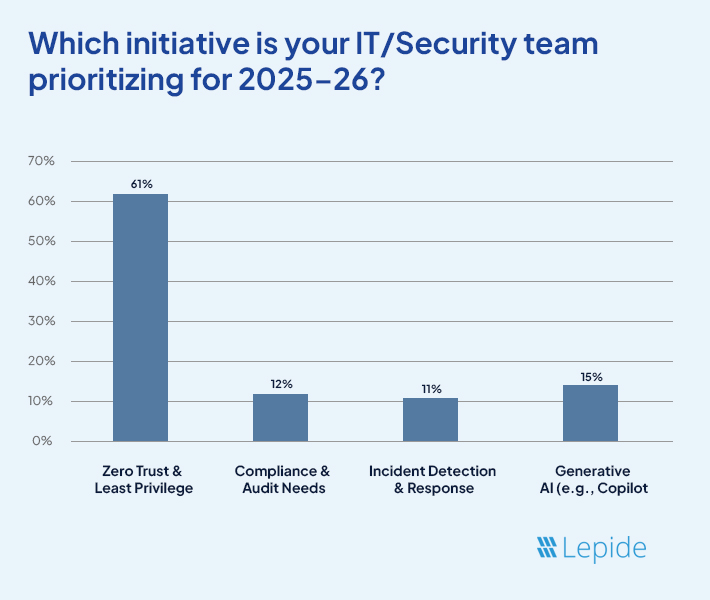
Why Are Teams Prioritizing Zero Trust & Least Privilege?
Teams are prioritizing Zero trust and Least privilege since these two concepts significantly enhance security through reduction of the attack surface and limiting damages from breaches. In its very core, Zero Trust follows the concept of “never trust always verify,” where each and every access request is authenticated and authorized even if it happens to be from the same network to where access has already been given. Least Privilege acts as the “plus one” of the interaction by making sure that users and systems are granted only the minimum rights that are enough to carry out their tasks, thus the possible incidences of escalations in privileges and the lateral movement within networks are kept at the minimum.
When combined, these technologies not only reduce the attack surface or mitigate risk, but they also offer layered barriers that prevent unwanted access and limit potential damage in the event of a breach. This is crucial for protecting hybrid cloud environments and preventing advanced threat scenarios with AI-enhanced malware.
In simpler terms, Least Privilege enforces tightly controlled access boundaries, ensuring each user has only the specific permissions their role requires. These two together act like a mighty weapon which is very helpful to companies that wish to lower the consequences of a security breach, meet the compliance requirements that keep changing and strengthen their security posture not only at the present time but also in the future.
Why Active Directory Security Matters Even More in 2026
Organizations will make securing Active Directory (AD) a key priority in 2026 as cyber threats continue to evolve and target the most identity infrastructure. It is the key element that keeps the IT environment safe.
Since Active Directory is the core of identity and access management, any loopholes can lead the attackers to the network which then can result in ransomware attacks, privilege escalation, and data breaches.
In 2026, companies will invest in this area by implementing stronger authorization protocols, better privileged access controls, and more efficient monitoring to be able to detect suspicious activities at the earliest stage. Organizations who want to protect their sensitive data and keep their cyber security strong, in this ever-changing threat landscape, will find it indispensable to implement proactive security measures in Active Directory.
These measures can include strengthening privileged access management, deploying continuous monitoring and auditing, using zero-trust concepts inside AD settings, investing in powerful threat identification instruments to figure out the most complex attacks on AD.
If organizations implement these steps in 2026, they will be well-positioned to prevent ransomware, insider threats, and lateral movement attacks.
Key Takeaways
- Insider threats can be lowered substantially by the employment of Zero Trust and Least Privilege concepts that also help in the minimization of attack surfaces through the enforcement of access.
- Organizations that put into practice these structures are able to detect and react to security incidents much faster.
- The increasing market volume and adoption rates are indicative of the strong trust that is placed in Zero Trust as a viable solution for the security of contemporary IT environments.
- Instead of only focusing on the deployment of Zero Trust principles, security teams need to consider the additional benefits that can be derived from this by integrating their efforts with AI-driven tools and automation to build up their resilience further.
- Moreover, training and upskilling in identity access management as well as knowledge of Zero Trust principles will be necessary to ensure the continuation of these initiatives .
Why Zero Trust and Least Privilege starts with Active Directory
Zero Trust and Least Privilege security strategies essentially evolve around Active Directory(AD) at their core as AD is the main infrastructure for identity and access management in most organizations. As Active Directory deals with user identities, group memberships, permissions throughout the networks, it is the main control point where trust boundaries and access rights are established and enforced.
To implement a Zero Trust model entails always authenticating the identity of every user and device before allowing access to resources, whereas Least Privilege guarantees that users are given only the minimum permissions necessary for their job. By using Active Directory as their starting point, companies can rigorously control, track, and log these access rights in a central location which is a great way to lessen the danger of lateral movement, insider threats, and ransomware attacks. Simply put, if Active Directory is not secured and strict privilege management enforced there, it is impossible to implement a real Zero Trust effectively.
How does Lepide Helps
Lepide Protect, that detects instances with excessive permissions, automatically removes the extra privileges, and offers real-time visibility to Active Directory and data access is, indeed, facilitating the rapid implementation of Zero Trust and Least Privilege concepts. Through the use of AI-driven automated processes, which can be done entirely within the Lepide Data Security Platform, permissions can be revoked, and inactive users removed without having to personally intervene by creating and invoking permission policies. Security teams find it easier to make the policy-to-practice transition when they have actionable insights to identify the most harmful changes, handle sensitive data, and enforce granular controls.