Health Monitoring
The simplest way to monitor the health of your Active Directory, Exchange Servers and SQL Servers.
Fill in the rest of the form to
download the 20-day free trial
download the 20-day free trial
x














It is always a good idea to ensure you have a way to continuously monitor the health of your critical IT systems. Doing this will help you prevent system downtime and mitigate the damages associated with workplace server disruptions. Lepide Data Security Platform offers you a way to get real time alerts on the health of your Active Directory, Exchange Server and SQL Server, all from one integrated console.
The Active Directory Health Check is an integrated feature of Lepide Data Security Platform. It provides a simple and powerful means of keeping track of important elements of your Active Directory to ensure continuity and health of the environment. It provides continuous monitoring and real time alerts for NT Directory services, DNS Servers, Disk space, CPU, Memory along with service and replication activity. Sounds like something of interest? Learn more about our Active Directory health monitoring
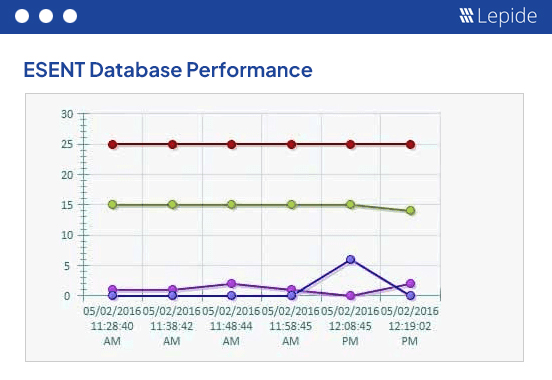
The Exchange Server Health Check is an integrated component of our Lepide Data Security Platform. It’s a simple yet powerful means of keeping track of the health status of your Exchange Environment. It enables you to keep track and alert based on predefined criteria pertaining to EDB file size, mailbox size, disk space, CPU utilization and much more.
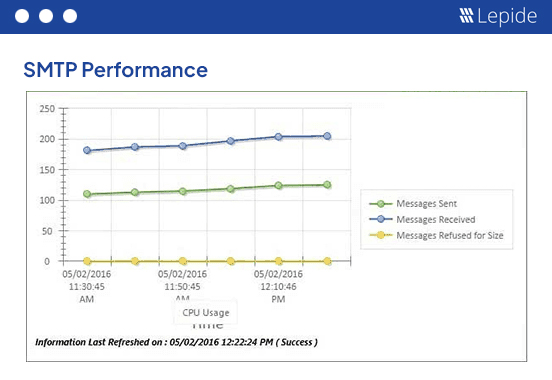
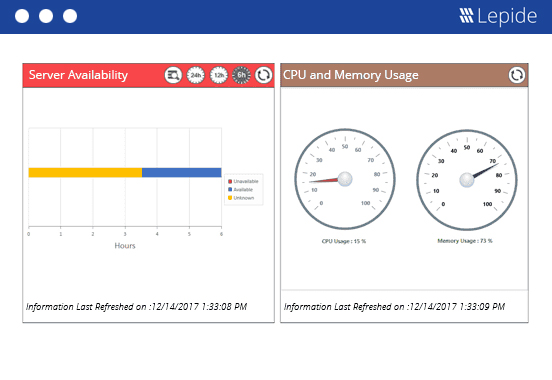
The SQL Server Health Check is an integrated feature of our Lepide Data Security Platform. It enables organizations to keep track and alert on server availability monitoring and alerting. It keeps tabs on things such as CPU & Memory, Service Activity, error rates, deadlock and user activity.
By following the guidelines outlined in this paper, your organization can establish a robust data access governance program that supports its business objectives and protects your valuable data assets.
Get the free guide now!