Group Policy Auditing Software
A simple, yet granular means of auditing Group Policy changes to maintain security and integrity.














Given the risks associated with Group Policy changes, we think it’s important that organizations have a structured and proactive approach to Group Policy auditing. We’ve made it easy to instantly see who, what, where and when changes are made, and even allow you to roll back the entire Group Policy Object to its previous ideal state. It comes with more than 40 predefined Group Policy audit reports and real-time alerts that make light work of what would otherwise be a very manual process.
Get detailed information on the changes taking place to Group Policy Objects with who, what, when and where values.
Report on the current state of Group Policy Objects and their settings to quickly spot deviations from the norm.
Respond to Group Policy changes as they happen with either real time or threshold based alerts.
Pre-defined reports for common security and compliance concerns, including PCI, HIPAA, GDPR, CCPA, SOX and more.
Overcome the limitations of native auditing and get the information you need quickly and easily.
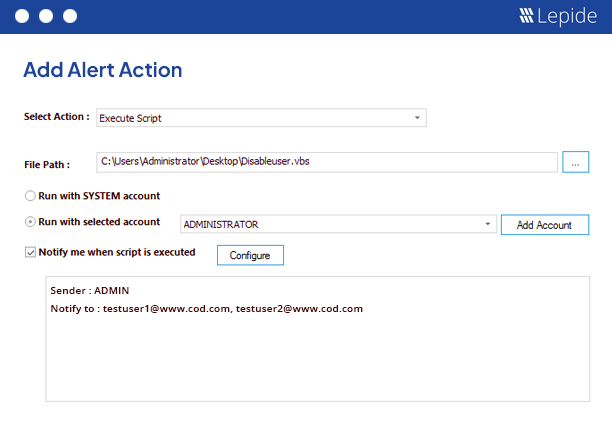
Automate the execution of custom scripts to take action when a specific alert is generated.
Our Group Policy auditing solution can help you monitor every change made to your Group Policy objects in real time. You can easily track any changes made to security setting policies, password policies, software restriction policies and much more with their before and after values.
Overcome the limitations of native auditing by getting increased visibility into the most important changes taking place to your Active Directory permissions and configurations. Get who, what, when and where information for all changes made. use this information, and the information from our real time alerts and pre-defined reports, to inform your response and react quickly to any potential insider threat.
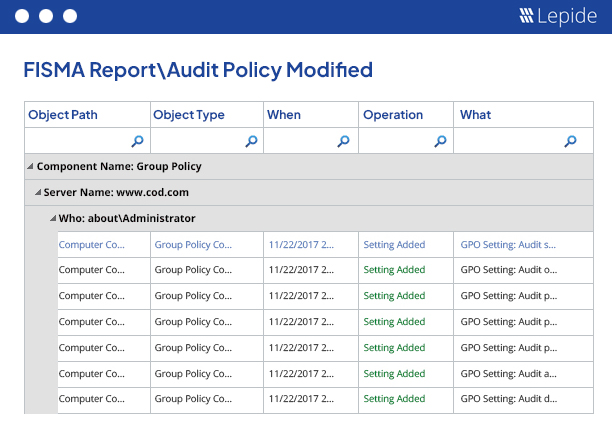
Concerned about meeting compliance mandates? Our auditing solution offers numerous inbuilt reports dedicated to helping you satisfy multiple compliance mandates, including HIPAA, PCI, FISMA, GLBA, SOX, GDPR and more. Specific predefined reports for Group Policies are also included in the solution to enable you to satisfy these difficult mandates quickly and easily. Read more...
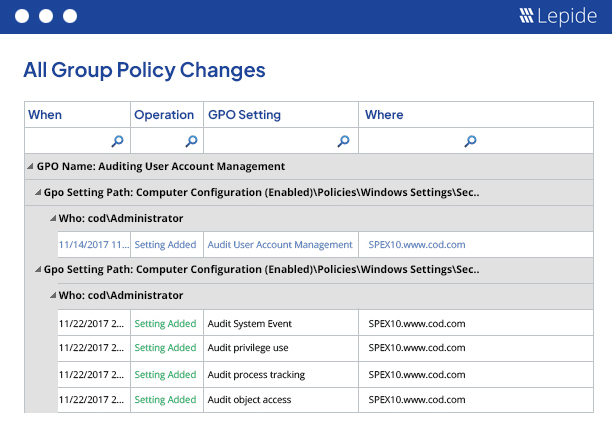
We keep track of all Group Policy changes as they happen, showing you all changes made to specific policies, links, states and more. We offer a single log for a single change displaying simply who, what, where and when the changes were made. We then provide this data through over 40 Group Policy audit reports to help you address all manner of security, IT operations and compliance challenges. All of our reports are easy to search, filter, customize and save as needed. You can customize any of the modification reports to focus only on specific policies or operations. These reports can be saved on the disk and delivered at scheduled intervals through email or by saving at a shared location in CSV, PDF or MHT formats. You can also delegate access to selected reports and users through a secured Web Console. Read more...
It’s inevitable that at some point a change will occur within your Group Policy that you did not intend for or want. Using our solution, we enable you to instantly restore an entire Group Policy Object to a previous ideal state whilst leaving all other Group Policy Objects intact. This feature lets you maintain the security of your IT environment. Read more...
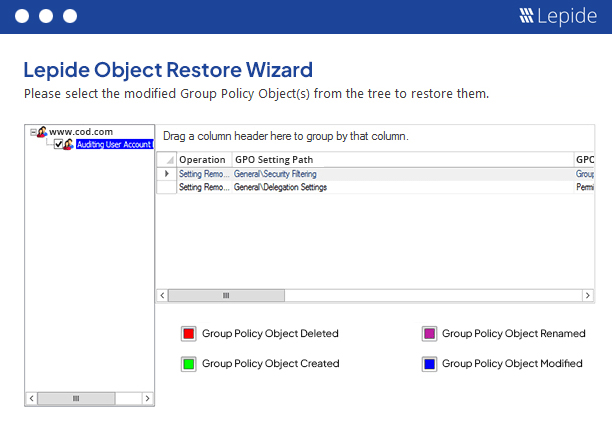
At Lepide, we know the cost of an unwanted change made in the Group Policies. Such changes have to be detected and reversed before it is too late. The inbuilt alerting mechanism lets you execute your own custom script to perform any automated action. For example, if a software restriction policy has been changed, you can execute a script to re-enable it or you can disable the user who has changed it. The inbuilt Object Restoration feature lets you restore the entire Group Policy Object to a previous ideal state.
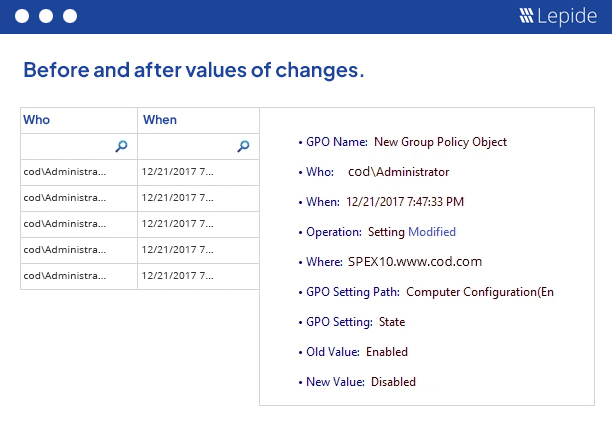
Naturally, you need to know whether a Group Policy has changed, but the real value comes from the context. Our solution shows you the before and after values for every change to improve the level of detail in every report. This will help enable IT teams to make quicker decisions and resolve IT issues faster through improved systems management.
By following the guidelines outlined in this paper, your organization can establish a robust data access governance program that supports its business objectives and protects your valuable data assets.
Get the free guide now!