Active Directory reporting can be frustrating without the proper tools. When AD reporting is challenging, maintaining the security of sensitive data becomes equally difficult. In this blog, we’ll explore the causes of AD reporting difficulties and how to overcome them.
Why Is Active Directory Reporting So Difficult?
Let’s identify the common challenges in Active Directory reporting:
- Much noise, no meaning: Windows event logs are noisy and not especially coherent. Rebuilding context across domain controllers is inefficient and prone to errors.
- Manual work increases risk: Searching through Event Viewer, exporting to CSV, and manually filtering won’t scale, and auditors require repeatable results
- Complex structures: Groups inside groups, delegated permissions at the OU-level, GPOs flowing through the environments, make it difficult to see the whole picture.
- Compliance demands: GDPR, SOX, HIPAA, and ISO 27001 all demand proof of behavior, not guesswork and screenshots.
- Multi-domain complexity: Multiple forests and different standards contribute to complexity in reporting.
The bottom line is, Active Directory reporting is complicated because AD is complicated. The challenge is turning the raw log into simple, repeatable, related reports that Administrators and Auditors can rely on.
What ‘Easy’ AD Reporting Should Look Like
Before we go into details, let us consider the criteria that an “easy” reporting has to abide by
- Ready-to-use reports: Common queries, for example, Who altered a group? Who signed in after hours? What rights were altered?
- Single context: All questions around “who, what, when, where” are answered in one place without hopping tools.
- Scheduled automation: Reports are delivered directly into inboxes without needing any actions from a person.
- Real-time alerts: High-risk changes, such as adding a user to Domain Admins, take place with real-time alerting.
- Tamper-resistant records: Logs that are stored in an auditable way.
- Controlled reporting access: Reporting access can be given to teams without the need for domain admin access.
- Easy exporting: Auditors get PDFs, analysts get CSVs, and investigations get an interactive view.
The Core Active Directory Reports (and How Lepide Simplifies Them)
Here are the reports most organizations need regularly, tied to real-world challenges
1. User Activity Reporting: Visibility into Accounts.
It’s important to have visibility into who your users are, the account history of changes, and what is unusual. Dormant accounts, accounts that have been recently enabled, or accounts requiring frequent password resets are signs of trouble.
Lepide enables you to:
- Monitor account creations, deletions, enables/disables, password changes and resets.
- Identify dormant accounts or stale accounts (long-inactive accounts) posing increased risk.
- Monitor unexpected activity, e.g., lockout storms, logon time.
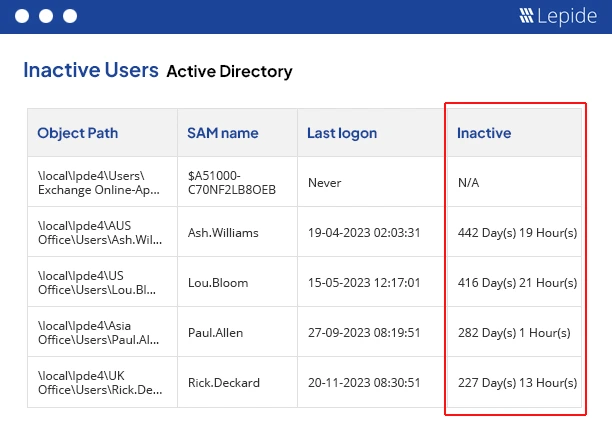
Maintaining identity hygiene remains consistent while mitigating noise to security teams. Schedule weekly Dormant Users and Recently Enabled Accounts reports to always establish that baseline
2. Permission Change Reporting: Prevent Privilege Creep.
Permissions change consistently– often without tracking where they fell off the table. There may just be an excessive number of privileges, and no adversaries are even connected.
Lepide enables you to:
- Report on ACL and permission changes across users, groups, and OUs (Organizational Units).
- Identify who was delegated access and when they did it.
- Maintain an audit history of privilege changes.
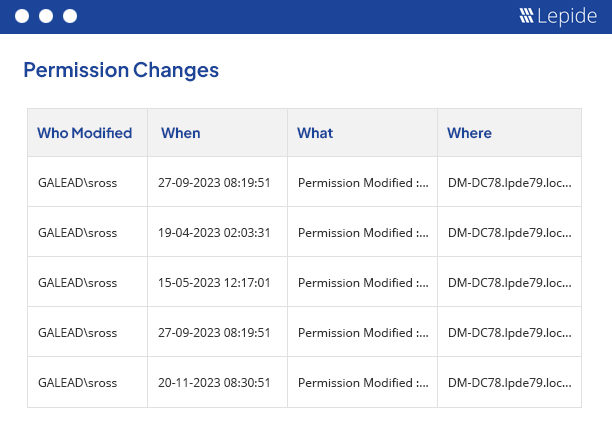
Permission Reporting documentation prevents escalation pathways for adversaries to exploit. Collaborate and pair with a monthly least-privilege review and use the Lepide report as the
3. Reporting on Group Membership: Deconstructing Nested Groups
Managing large groups can make it difficult to understand the true nature of access, particularly with privileged groups such as Domain Admins or Enterprise Admins.
Lepide allows you to:
- Report on the historical and current membership of any group that is a critical factor.
- Report on the history of adds/removes with context
- Identify the additions/changes to nested groups that are hidden.
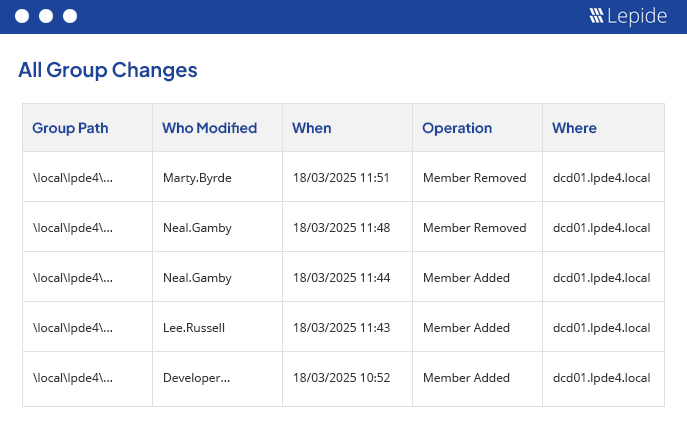
Most of the “how did they get admin rights?” situations can be traced back to nested group changes that were not visible. Set up live alerts for any changes to privileged groups and send a daily report to leadership as an ongoing series of changes.
4. GPO Change Reporting: Policy in Action
Group Policy is where the control over the environment exists… changing just one thing could secure whatever it is and change it to expose it.
Lepide can:
- Report on GPO creates/deletes/changes/and links.
- See who changed, what changed, and where it applied.
- Track GPO changes for audit history, and your retention period will depend on your organization’s policy.
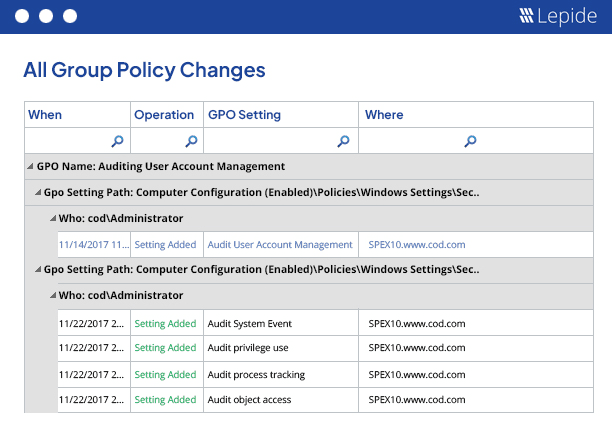
Adding this feature to your reporting will let you prove to supervisors that controls are in place and allow you to act quickly to any incidents. It may be beneficial to share a weekly delta GPO report with your change advisory board (CAB).
5. Logon/Logoff Reporting: Discover Anomalies
Logon events occur frequently and are a repository of useful signals. It is easy to miss logons occurring after hours, brute-force attempts, or lateral movement without filtering.
Lepide can help with:
- Reports of successful logons / failed logons, logoffs, interactive vs. network logons, etc
- Alert you to post business hours activity or excessive failures.
- Integrate with SOC systems for real-time alerts.
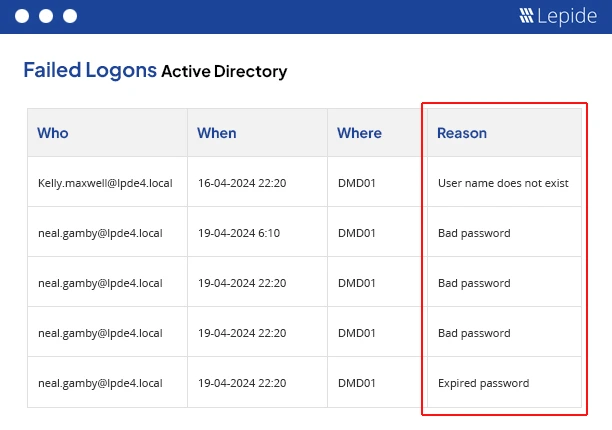
It only takes one early detection of misuse in an account to stop a larger breach from occurring. You should subscribe your SOC to the failed admin logons digest and set configurations for it.
How Lepide Makes AD Reporting Simple
Lepide Active Directory Auditing and Reporting comes equipped with predesigned reports that cover the basics right away, user action, permissions, group membership changes, GPO changes, and login/logoff patterns. Each report adds correlated context that displays who made the change, the value of what was changed, when the change was made, and in what location the change was made, thus making it much easier to move from detection to investigation without having to sift through raw event logs.
The reports may also reduce manual reports through scheduled reports and subscriptions that will deliver weekly or monthly evidence packs for audits. For incidents that cannot wait, real-time alerts are created in case a high-risk change occurs, while role-based access ensures that teams only see what they need to see, without requiring AD administrator access rights.
When it comes time to share, the reports are exportable in PDF or CSV formats that match what you see in the console. Lepide’s platform also extends across multiple domains/forests, so enterprises can ensure continued reporting and performance across the most complex environments.
5 Quick Steps for Getting Started
- Start with the essentials: Don’t think that you will audit everything on day one. Look only at the critical reports providing visibility and value, in order of user activity, permissions, group memberships, changes to GPOs, and logon/logoff events. These reports will likely include most of the sorts of things auditors ask about at the beginning and will point to security issues
- Assign ownership: Reports only matter if someone is responsible for following up. Will it be a team or an individual who responds to different reports and alerts? For example, decide who owns real-time alerts vs. who owns the weekly and monthly aggregated reports. Assigning ownership will assure that urgent issues are acted upon quickly and that longer-term trends become part of a strategy.
- Set baselines: What does “normal” look like in your environment? Set baselines for the different privileged groups you expect to have, what would be an unusual login outside business hours, what thresholds you count as cause for concern, etc. With this baseline information, you’ll be able to cut through the noise to improve the chances of only seeing events that matter
- Automate reports: Don’t make audits or multi-week checks or monthly reports a manual task. Use scheduling and subscriptions to send out the reports automatically and only print them for the appropriate group or individual. Reducing the amount of time your security or admin teams spend doing calls will allow staff to always have them printed and ready to go for team or client requests for audits
- Refine over time: Reporting isn’t a one-time task. As you gain insights, use them to adjust thresholds, implement tighter controls, and remove unnecessary alerts. Over time, as you develop the reporting process, reports become more reflective, actionable, cleaner and produce better security results.
Eventually, reporting becomes a part of your security and compliance, rather than an added task.
Conclusion
Reporting on Active Directory doesn’t have to be stressful. By transitioning from manual log reviews to automated, contextual reporting, you can improve security, make compliance easier, and provide time back to admins. Ready to simplify reporting? Find out how Lepide makes Active Directory reporting faster, clearer, and ready for audit by scheduling a demo with one of our engineers today or download the free trial today.



