Zombie Accounts in Active Directory (AD) mainly refer to any accounts (including user, service, or computer accounts) that have been left behind and become inactive. These accounts can be ex-employees, contractors whose contracts have expired, or accounts created for temporary projects which have neither been disabled nor deleted. They provide significant risks that could result in illegal access and security breaches because they are difficult to locate even though they are still operational.
Real-world examples can be quite helpful in explaining the risk clearly. Often during breaches, attackers will take advantage of old contractor accounts that were never disabled after the end of the project in order to deploy ransomware. In a few cases, the attackers took over the control of essential structures in this way, by using inactive admin accounts with old passwords, thus gaining the access they needed. These accounts are very often undiscoverable because they are inactive but still valid, and usually, they do not have the latest security measures like multi-factor authentication.
How Zombie Accounts Form in Modern AD Environments
The existence of zombie accounts is usually the result of a failure in the management of the account lifecycle that has been overlooked in operational activities. As part of the process, IT and HR teams are expected to deactivate or remove the Active Directory accounts of the employees who have left or changed their roles promptly. It is often the case that accounts are left active due to manual errors, communication gaps between departments, or lack of automated workflows even though access is no longer needed.
Zombie accounts gather in AD setups through the following foremost ways:
- Mergers and Acquisitions: Due to migratory processes during mergers, the accounts of the old directories get carried over but are seldom cleaned out properly.
- Contractors and Vendors: : External temporary accounts continue because there is a lack of proper offboarding coordination between HR and IT.
- Shadow IT: The accounts that are made out for the use of the non-approved tools are cloud resources that are not managed, hence the credentials get abandoned.
- Poor-Joiner -Mover- Leaver Workflows: There is an overlap of accounts and the existence of disabled ones as a result of manually operated or irregular JML techniques, which can cause delays or misses in disabling accounts for individuals who have left the organization or have changed roles.
Why Zombie Accounts Are a Serious Business Risk
Here are the five most serious risks that arise when zombie accounts remain unmanaged in AD.
- Privilege Escalation: Zombie accounts often have valid credentials for a long time after the respective owners have already left the organization or the original purpose has expired. Most of such accounts still have old passwords or are not equipped with contemporary security features like MFA. In such accounts, attackers use stolen credentials from previous breaches or brute-force attacks to get undetected access to sensitive systems. In the case of zombie accounts, since they are separated from real users, an abnormal action such as logging in from an unusual location — can hardly be detected. The ability to be unnoticed is what makes them so attractive to attackers, who use them as a base for escalating privileges and moving laterally further into the network.
- Breach Likelihood: In an automated credential stuffing attack, an attacker carries out many tests of username-password combinations to find weak points. In such an attack, zombie accounts are the most achievable targets since the passwords to these accounts might be weak, reused, or simply not changed for a long time. The risk with inactive service or administrative accounts is even greater as these accounts often have elevated privileges but are not even considered in the day-to-day monitoring. If attacked, these forgotten credentials will be able to act as secret backdoors bridging the attackers to the critical systems and providing a way for them to stay undetected for months.
- Compliance Penalties: Besides weakening security, zombie accounts are also contributors of compliance liabilities. For example, the regulatory frameworks like GDPR, HIPAA, SOX, and PCI DSS stipulate the need for strict access control as well as regular reviews of the account activities. Inactive or forgotten accounts are breaching these requirements since they permit the unauthorized identities to remain in the most sensitive parts of the systems. At the time of an audit, the organizations will be imposed with penalties and suffer from loss in their reputations if they fail to provide the necessary justification as to the reason for the existence of zombie accounts or prove that they are not a security issue. Besides, a data breach triggered by one of these accounts is likely to set off disclosure requirements, lawsuits, and scrutiny from partners and regulators.
- Reputational Fallout: The fact that zombie accounts can be repeatedly exploited for resources and access without the victim’s knowledge is one of the main reasons they are harmful. Most of the time, security teams and automated monitoring programs ignore inactive accounts that are left open but unused, making them the preferred access points for hackers. These accounts typically have high privileges and inadequate security, making it possible for attackers to get illegal access for a considerable amount of time without being discovered. Because of this continuous access, attackers can take advantage of resources in a number of ways, including by scheduling malicious tasks, obtaining sensitive data, or even paying for costly services like cloud resources. As a result, the organization is put in danger for a long time, loses money, and violates regulations. If such an incident occurs because of a zombie account, it can damage your company’s reputation.
- Orphaned Privileges Fuel Insider Threats: Sometimes when the contractors subsequently leave the enterprise, the employees depart, or the projects come to an end, their accounts that are linked with them remain in AD as still active. These orphaned zombie accounts can still have the ability to access business-critical data, financial platforms, or even domain admin rights. On the one hand, malicious insiders who exploit these accounts; on the other hand, external actors who happen to find them, thus, the accounts are at risk of being abused. The absence of defined ownership or responsibility for these accounts makes them particularly risky as they allow abuse of privileges without being held accountable. Besides that, regular inspections that also look into “lastLogonTimestamp,” “lastLogonDate,” and “pwdLastSet” are vital for spotting and eliminating those which are still around.
- Insurance Implications: Cyber insurance providers are demanding stringent identity governance as a means of lowering cyber risks, and the presence of unmanaged zombie accounts can threaten the coverage or raise the premiums. Inactive accounts are often devoid of recent security features such as multi-factor authentication and may still have privileged access, thus making them highly attractive for hackers. These neglected accounts can wreak havoc on an organization’s breaches, compliance, and finances. Companies that have implemented proactive identity governance are considered less risky and are given better insurance conditions, hence the management of zombie accounts is vital not only for security but also for financial protection.
Proactive measures such as effective management, deletion of inactive accounts, and proper access control policies are some of the ways through which these risks can be lessened, and digital security can be maintained.
How to Identify Zombie Accounts Quickly
To thoroughly identify zombie accounts in Active Directory, adhere to these important points:
- Examine Inactive Accounts: Inactive Accounts is one of the best places to look for methods. By using the “lastLogonTimestamp” or “lastLogonDate” properties, one can repeat Active Directory queries to find user accounts that have not been logged in for a long time, usually 90 to 180 days. Additionally, examining the “pwdLastSet” feature might help identify instances when a password hasn’t been updated in a long time, which may indicate neglect or abandonment. These accounts are the most likely sources of zombie accounts, which are essentially outdated credentials that can be used by attackers if the security of such accounts is not guaranteed, due to their prolonged inactivity and lack of update.
- Monitoring Login activities: Watch for login and authentication activities on accounts that have not been used for a long time, are accessed in an unusual way, or show some other kind of strange behavior. These could be dormant or hacked accounts.
- Audit Permissions and Roles: Through frequent audits of user privileges and group memberships, you will be able to find those accounts whose rights are outdated, overly elevated, do not correspond with the current role, and which have not been used for a long time.
- Cross-Relation HR Records: Contact HR to determine whether the accounts belong to employees, contractors, or ex-employees. The accounts of former employees and contractors should be immediately disabled or removed so that there is no risk of liability arising from their continued access.
- Conduct Regular Account Reviews: Create a system to account for certification and review so that non-active accounts are brought to the surface and business owners verify the need for the account before granting access.
- Revoke Access Right Away: As soon as zombie accounts are discovered, switch them off or delete them to minimize the ongoing risk. Make sure that in the event that contractors or workers depart the company, there are stringent procedures and guidelines for their immediate departure.
By identifying and addressing those accounts in a methodical manner before a criminal can, a company can safeguard itself against the harm caused by zombies.
What Good Looks Like: Governance and Prevention
Top-tier organizations view preventing zombie accounts as an essential component of their identity governance architecture rather than a temporary fix. A healthy status consists of:
- Clearly defined and integrated procedures for Join, Move, and Leave (JML) operations involving HR, IT, and security.
- Automation for deprovisioning or disabling accounts when employees go or contracts end.
- Applying the least privilege principle, which states that no user should have greater access than is required.
- Regular access audits, in which management verifies who still requires system access.
After incorporating these measures into their standard operations, organizations no longer have to deal with reactive cleanup but rather have continuous assurance.
How Lepide Helps Remove and Prevent Zombie Accounts
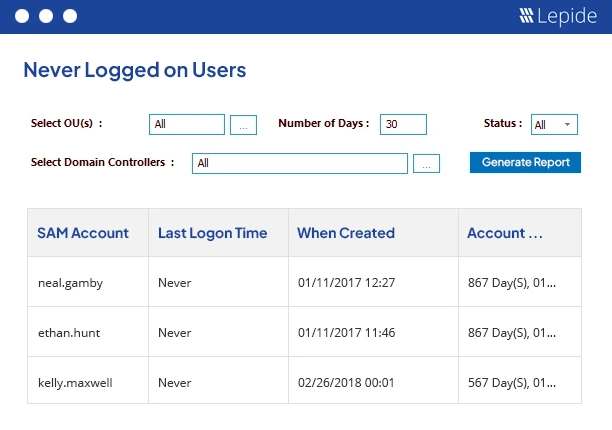
Lepide platform empowers IT and security teams by automating discovery and management of zombie accounts in Active Directory and beyond. With a primary focus on identifying and mitigating the risk of zombie accounts, Lepide offers complete solutions that fulfill all of your needs for active directory administration and security. Moreover, the Organization can take advantage of Lepide Free Inactive User Report Tool which facilitates the identification of orphaned or inactive accounts and makes the process of cleaning up quicker. These tools routinely checks and verifies the directory to find any user accounts that have been neglected or left unattended. It also identifies any accounts that could pose a threat to network security.
Lepide provides a number of dashboards and statistics that also integrates with identity governance frameworks to maintain healthy joiner-mover-leaver processes, enforce least privilege, and deliver real-time insights.
Additionally, the platform performs manual activities like disabling an account, changing a password, transferring an inactive account to a target organizational unit, or deleting it when the time interval has expired. If organizations adopt such a rigorous strategy, they will be able to reduce their attack surfaces, maintain a clean Active Directory environment, and comply with regulations more quickly and easily.
Conclusion: Zombie Accounts Are a Business Problem, Not an IT Cleanup Task
Not only do zombie accounts add to the technological chaos, but they also represent the trust ties that have been forgotten, which puts the company at risk. To deal with them, the leadership team must be involved, policies must be coordinated, and intelligent automation must be used.
By exposing and eliminating outdated accounts that have been dormant in the shadows rather than waiting for the attackers to accomplish it, Lepide gives businesses a means of regaining control. Lepide simplifies the process since it provides visibility, ongoing monitoring, and automated problem-solving, all of which lower risk. Managing zombie accounts effectively is a cost-effective strategy, a powerful tool for cyber defense, and a way to facilitate compliance.
Schedule a demo or get a free trial to gain control over your Active Directory security with Lepide’s powerful management tools and stop zombie accounts from turning into a weakness.