When insiders misuse their access rights, either by mistake or on purpose, the damage spreads quietly and quickly. These tools help you see who is doing what, when, and whether the activity looks normal or needs a response.
Some platforms focus on behavior analytics and detection. Others focus on evidence, case workflows, and preventing risky actions in real time. The best fit depends on what you need to catch and what you need to prove.
What Features Should an Ideal Insider Threat Protection Tool Include?
A good insider threat tool does two jobs well. It finds risky behavior early, and it gives you enough context and evidence to act without guessing. The features below are the ones that matter in real incidents.
- Behavior baselining and anomaly detection (UEBA): A solid tool should learn what “normal” is for the user, and indicate important differences when they occur. That is how you will find slow, subtle abuse that does not trigger any of the basic rules. UEBA has been designed specifically for analyzing insider threats and compromised accounts, since it focuses on actions rather than just signatures.
- Case management and investigation workflow: Insider risk is rarely a single alert. You need a centralized location to consolidate all the alerts you have received, collect evidence, track the reviews you have performed, and finalize your work. Microsoft Purview Insider Risk Management and similar tools were designed around policies that trigger alerts and cases; the cases generated by these tools represent the primary method of investigation.
- Identity and authentication signal coverage: The tool should ingest sign-in and access activity across your identity stack and detect misuse patterns like suspicious logins, repeated failures, risky sessions, and sudden privilege changes.
- User activity monitoring and audit trails you can trust: At minimum, the platform should maintain strong audit trails of user and system activity and support procedures for log review, protection, and retention. This is not just for security teams. It also matters for compliance, investigations, and proving what happened.
- Data misuse and data movement detection: Insider incidents often involve data theft, leakage, or policy violations. Consequently, you should look for these types of behaviour that could be potentially harmful. The best way to perform this task effectively is to use Microsoft Purview. Insider risk, as presented by this application, is defined as a means of identifying and responding to both malicious and unintentional behaviours associated with data loss or intellectual property theft.
20 Most Effective Insider Threat Prevention and Monitoring Tools
- Lepide Data Security Platform
- Microsoft Purview Insider Risk Management
- Microsoft Sentinel (UEBA)
- CrowdStrike Falcon Identity Protection
- Splunk UEBA / Splunk Enterprise Security
- IBM QRadar UEBA
- Exabeam UEBA
- Securonix Insider Threat
- Proofpoint Insider Threat Management
- DTEX Systems
- Forcepoint Insider Threat
- Gurucul Insider Risk Management
- Rapid7 InsightIDR
- Veriato Insider Risk Management
- Teramind Insider Threat Detection
- Code42 Incydr (Mimecast)
- Syteca (formerly Ekran System)
- Quest ITDR / Security Guardian
- Varonis Insider Risk Management
- Netwrix Insider Threat Detection
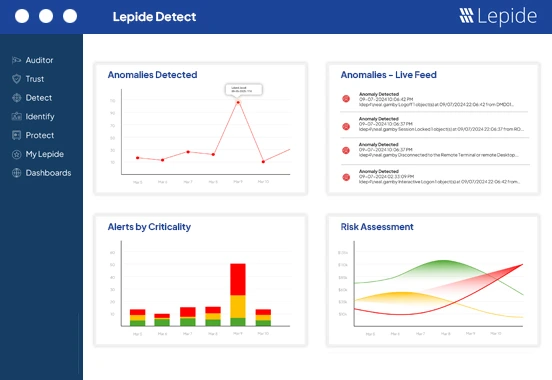
1. Lepide Data Security Platform
Lepide Data Security Platform pairs real-time activity monitoring with behavior analytics and prebuilt insider threat models so you can spot unusual user activity before it becomes an incident.
It ingests file, identity, and system events across on-prem and cloud sources, applies targeted threat models (for mass deletes, data copy, privilege escalation, etc.), and surfaces anomalies tied to the specific user and object involved. That makes it easy to move from a noisy alert to a focused investigation with the right context.
The platform also supports automated response workflows (disable account, revoke access) and compliance dashboards so you can produce an evidence package quickly during investigations or audits.
Key Features
- Detects risky insider activity using prebuilt behavior and threat models such as mass data access, unusual file copying, and privilege misuse
- Correlates Active Directory, file, and system activity to a specific user and object for fast, context-driven investigations
- Supports automated response actions and audit-ready reports to speed up incident response and compliance reviews
2. Microsoft Purview Insider Risk Management
Microsoft Purview collects signals from applications, email, and identity systems associated with Microsoft 365. Using Purview, you can detect not only data exfiltration but also violations of policy, as well as other high-risk behaviours (e.g., risky email and web activity). You can also use Purview to manage investigations in a way that enables compliance with the GDPR and other compliance regulations.
M365 and Entra ID are part of the Microsoft stack; therefore, the most efficient way to utilize Microsoft Purview is if your organization already has both. Microsoft Purview may be the best solution for your application/business if you are looking for an all-in-one system for signalling, collecting, and managing investigations according to the policies and procedures of your organization.
Key Features
- Built-in policy templates for insider risk.
- Case management and review workflows.
- Integration with Microsoft identity and content signals.
3. Microsoft Sentinel (UEBA)
Sentinel’s UEBA capability provides baselines for users and entities, indicating deviations from those baselines and linking signals from Entra ID and Active Directory (AD) with additional telemetry to allow for greater visibility into identity anomalies within the broader context of all events that occur in an organization.
When using Sentinel in larger-scale environments, it is best to centralize logs in Azure to fully utilize its capabilities. Sentinel is designed for flexible threat hunting, built on a strong foundation of user activity analytics.
Key Features
- UEBA models and user risk scoring.
- Cross-signal correlation across identity, network, and endpoints.
- Notebook and hunt capabilities for analysts.
4. CrowdStrike Falcon Identity Protection
By correlating endpoint telemetric data with identity signals, CrowdStrike can identify credential theft and lateral movement. Its model reduces the occurrence of false positives by combining device and user context, enabling timely containment of an incident.
This solution will be particularly beneficial when you require identity analytics that consider the functional state of both the endpoint and how it behaves, rather than just the presence of login anomalies. Falcon supports both cloud and on-premise technology systems.
Key Features
- Identity risk scoring and detection.
- Endpoint-context correlation for alerts.
- Cloud and on-prem support.
5. Splunk UEBA / Splunk Enterprise Security
By indexing the Active Directory and Authentication logs, Splunk employs User Entity Behavior Analytics (UEBA) to detect behavior outside the norm. Analysts use Splunk Enterprise Security (ES) for searching, building timelines, and correlating across multiple data sources.
Splunk ES provides hunters and report creators with effective and efficient analytic capabilities through a calculated build-out of custom searches and extensive correlation; however, it must be developed carefully to limit event volume to a manageable number.
Key Features
- ML-based anomaly detection.
- Custom correlation searches and dashboards.
- Case and incident workflows in Splunk ES.
6. IBM QRadar UEBA
Incorporating user and entity profiles into SIEM event streams and surface identity-related occurrences as offences.
Large organizations typically select QRadar for its ability to provide detection capabilities within an organization’s overall security operation by enabling the identification of potentially harmful behaviour associated with user identity through behavioural analytics.
Key Features
- User risk profiles and baselining.
- Integration with QRadar offence workflow.
- Scalability for large log volumes.
7. Exabeam UEBA
By providing timeframes associated with user and entity activity rather than simply displaying events that happen independently, Exabeam enables analysts to identify instances of credential misuse more quickly and connect smaller indicators to create an overall picture pertaining to the incident.
Exabeam also has capabilities designed to help analysts group together similar types of incidents as they perform triaging and investigating, all while providing a readable description of the incident.
Key Features
- User timelines and incident grouping.
- Behaviour-based detection and scoring.
- Automated story creation for analysts.
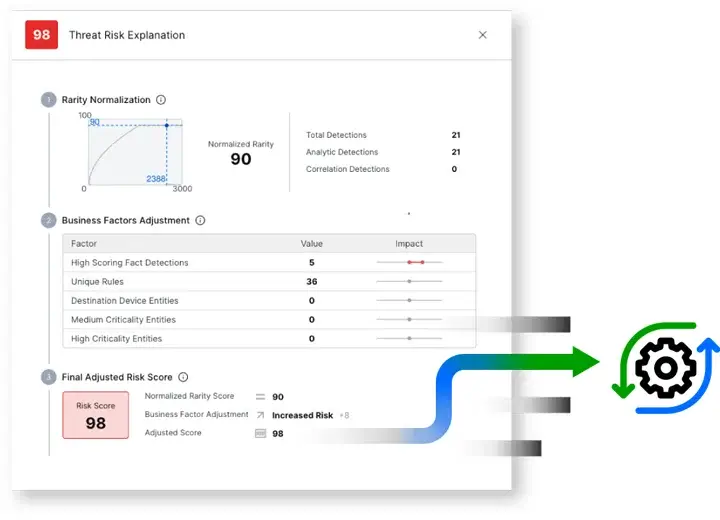
8. Securonix Insider Threat
Securonix employs Behavioral Analytics and High Volume Data Set Analysis for detecting high-risk insider activities while reducing the number of false alerts. Securonix has case management and threat modelling tools specifically developed for Insider Threats.
Organizations that experience extremely high volumes of events should consider using Securonix because of its ability to produce and implement tailored predictive models for Privileged Abuse and Data Theft. Securonix fits extremely well into complex Enterprise Environments.
Key Features
- Advanced UEBA at scale.
- Threat modelling for insider risk.
- Case management and investigation tools.
9. Proofpoint Insider Threat Management
Proofpoint’s insider risk product captures endpoint activity and pairs it with analytics to find risky behavior, data theft, or policy violations. It records evidence that is easy to review if HR or legal needs proof.
This tool is strong when you need concrete endpoint records tied to AD accounts, such as session playback and file transfer logs.
Key Features
- Endpoint activity capture and session search.
- Policy-based detection and case building.
- Evidence export for investigations.
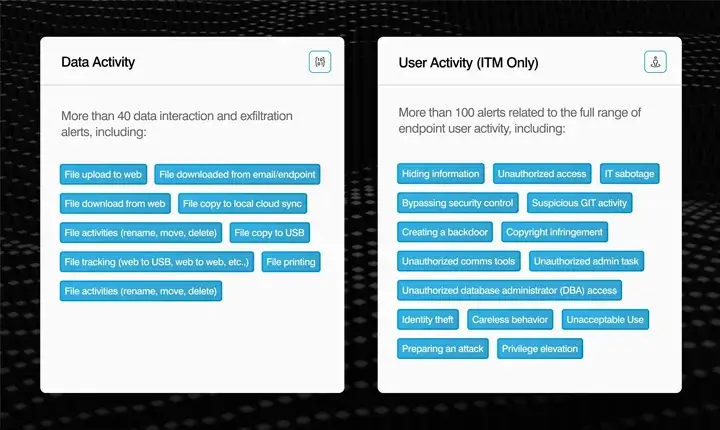
10. DTEX Systems
DTEX uses endpoint telemetry and user behaviour to assess risk through continuous monitoring of risk-based activity on all endpoints, which enables DTEX to alert on anomalous workflows prior to causing significant damage, but is also useful when tracking unexpected data flow across endpoints or sudden user changes in activity.
Key Features
- Continuous endpoint telemetry.
- Behavior baselining and exfil detection.
- Dashboards for rapid triage.
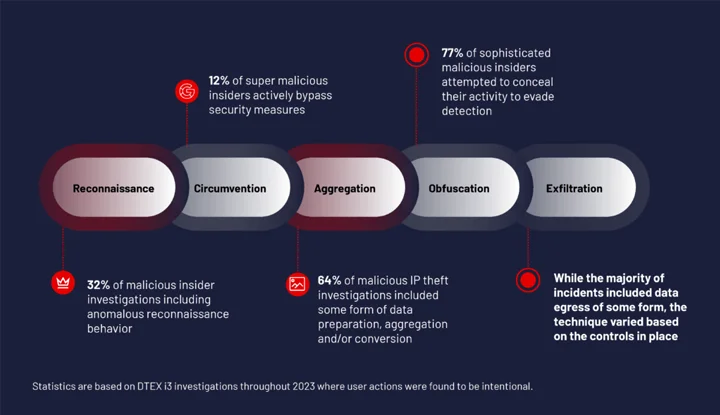
11. Forcepoint Insider Threat
Forcepoint uses policies and user behaviour analysis to help organizations eliminate risky user behaviour through the blockage of data transfer when necessary; this process includes linking content policies with user signals so that they can be clearly enforced.
When combining policy and behaviour detection, Forcepoint is a preferred choice for organizations as it provides the business workflow to eliminate risks.
Key Features
- DLP integration with behavior analytics.
- Policy-triggered actions and blocking.
- Incident review and reporting.
12. Gurucul Insider Risk Management
Gurucul uses machine learning to create risk scores from identity and behavior signals. It highlights high-risk users and supports investigations with flexible analytics.
This tool is suited for teams that want ML-based prioritization of insider risk and flexible deployment choices.
Key Features
- ML-driven risk scoring.
- UEBA and identity analytics.
- Case workflow support.
13. Rapid7 InsightIDR
The InsightIDR solution gathers and analyzes user and entity behavior analytics (UEBA) from logs, endpoint telemetry, and security events for the detection of account compromise and risky behavior. InsightIDR allows you to quickly achieve value from your deployment, even with out-of-the-box detections.
In addition, InsightIDR was designed to be an integrated product with assistance for the investigation process through detection guidance and Active Directory logging support; therefore, it will make it easy to conduct an investigation efficiently.
Key Features
- Built-in AD detections and UEBA.
- Endpoint telemetry and log collection.
- Guided investigations and playbooks
14. Veriato Insider Risk Management
Veriato records the actions of users and utilizes behaviour analytics to detect potentially inappropriate or harmful behaviour and data exfiltration. Veriato produces granular timelines of user activity and will assist with investigations by providing detailed evidence and timelines of activity for each user.
Veriato is used when it is necessary for investigators to have evidence that is both easily reproduced/replayed and meaningful for HR and/or legal reviews.
Key Features
- User activity recording and playback.
- Behavior scoring and alerts.
- Timeline reports for investigations.
15. Teramind Insider Threat Detection
Teramind records the user’s screen, keyboard strokes and file activity, then analyses the records for use in identifying suspicious behaviour. It provides session playback and rule-based detection capabilities to allow for rapid evidence collection.
Due to its combination of high-quality session-level visibility with various forms of automation, many companies choose Teramind in order to be able to identify, prevent, and respond effectively to the potential for risky behaviour in real time.
Key Features
- Session recording and playback.
- Rule-based and behavior detection.
- Real-time blocking and alerts.
16. Code42 Incydr (Mimecast)
The Incydr product addresses data transfer and file-based risk. It allows users to monitor risky file activities across their endpoints and cloud-based files and ties those activities back to the end-user’s identity for investigation purposes.
If your company’s primary goal is to safeguard company-library files (i.e., IP) while being aware of how sensitive files are accessed/copied, select Incydr.
Key Features
- File activity monitoring and exfil detection.
- User context and incident prioritization.
- Cloud and endpoint coverage.
17. Syteca (formerly Ekran System)
Syteca provides session recording and privileged user monitoring with on-prem or hybrid deployment. It captures exact user actions during privileged sessions for later review.
This is a solid option when regulated environments require local control and detailed privileged session evidence.
Key Features
- Privileged session recording.
- Alerting on risky commands or actions.
- Playback and audit export.
18. Quest ITDR / Security Guardian
Quest’s ITDR offerings monitor identity signals and help trace identity attack chains in AD and hybrid estates. They focus on detecting identity misuse and guiding containment steps.
This fits AD-heavy environments where identity-focused detection and remediation guidance are needed.
Key Features
- Identity attack detection and playbooks.
- AD posture checks and risk alerts.
- Guidance for containment and remediation.
19. Varonis Insider Risk Management
Varonis associates Active Directory permissions with user activity on both files and mailboxes and, through behaviour analysis, identifies risky actions being taken by users. With this, it allows you to see not only who has access (could access) sensitive data, but also who actually accessed it (did access).
If your insider risk programme uses mapping data exposure and/or investigating file system usage/behaviour analytics, then Varonis is a good product for your solution.
Key Features
- Data access analytics and exposure mapping.
- Behavior-based alerts on risky file use.
- Permission cleanup recommendations.
20. Netwrix Insider Threat Detection
Netwrix Insider Threat Detection helps organizations identify malicious or negligent insider behavior by monitoring user activity across identity and data-centric systems.
Key Features
- User behavior monitoring: Detects abnormal access patterns and risky actions across Active Directory and file servers
- Change and access auditing: Tracks who accessed or modified sensitive data and system configurations
- Real-time alerts & reporting: Provides instant alerts and detailed reports to support quick investigation and compliance
Conclusion
Pick tools based on the signals you can collect and the proof you need. If your environment is AD-centric, prioritize products that ingest Windows security events and link them to user context. If data theft is your top concern, choose data-centric monitoring. If privileged misuse is the issue, look for session capture and privileged controls.
FAQs
Q- Which signals matter most for AD-focused insider detection?
Ans- Start with these in order. Authentication and logon events. Privileged group membership changes. File access on sensitive shares. Endpoint process and network connections. Add session recording for high-risk admins. If you collect those signals and link them to the same user identity, you get real, actionable context.
Q- How do user behavior monitoring tools work with Active Directory?
Ans- These tools ingest AD logs, Windows security events, authentication data, and sometimes endpoint activity. They build a baseline of normal user behavior and then flag deviations, such as off-hours access, sudden privilege escalation, or mass file activity. The goal is context, not just alerts.
Q- What is the difference between UEBA and insider threat tools?
Ans- UEBA tools focus on identifying anomalies by modeling normal behavior across users and systems. Insider threat tools go a step further by adding investigation workflows, evidence collection, policy enforcement, and sometimes session recording. Many modern platforms combine both approaches.
Q- Do I need endpoint monitoring for effective insider threat detection?
Ans- Endpoint monitoring is not always required, but it adds strong context. AD logs show what permissions exist and when access happens. Endpoint telemetry shows what the user actually did. For high-risk users or sensitive data, combining both gives much stronger evidence.



