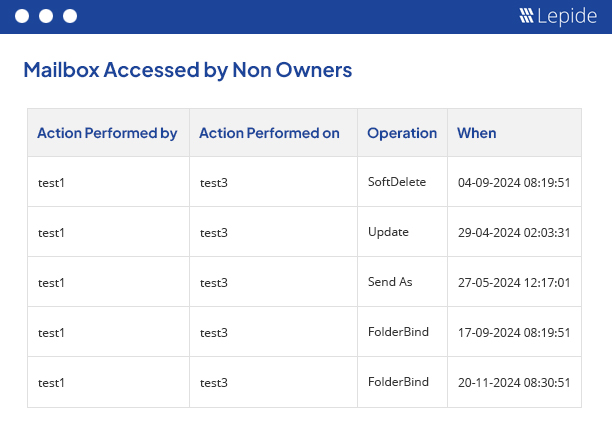
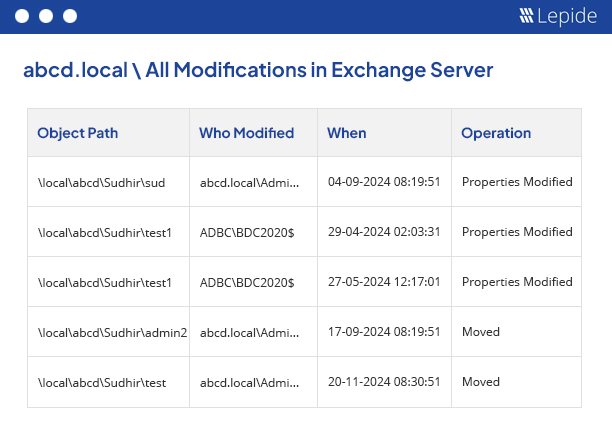
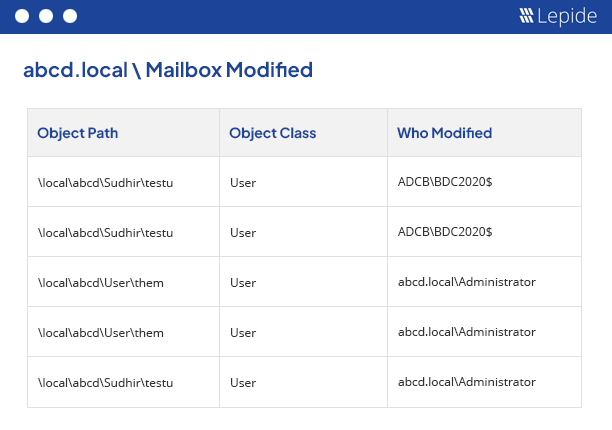
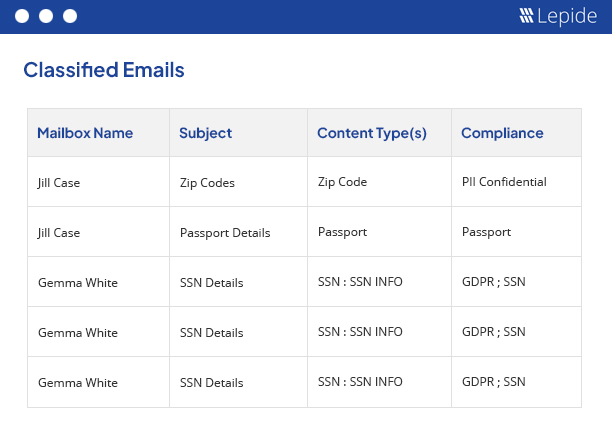
Exchange Auditing Software
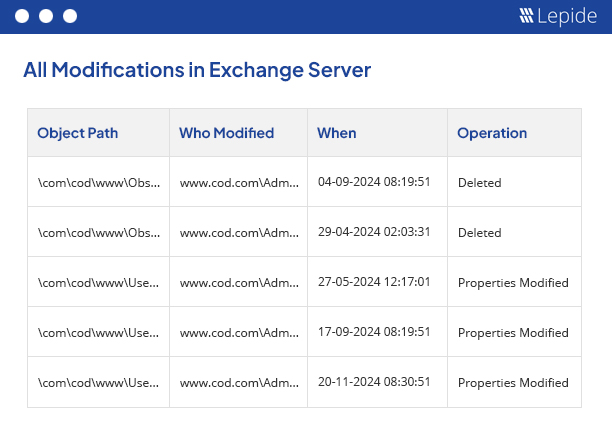
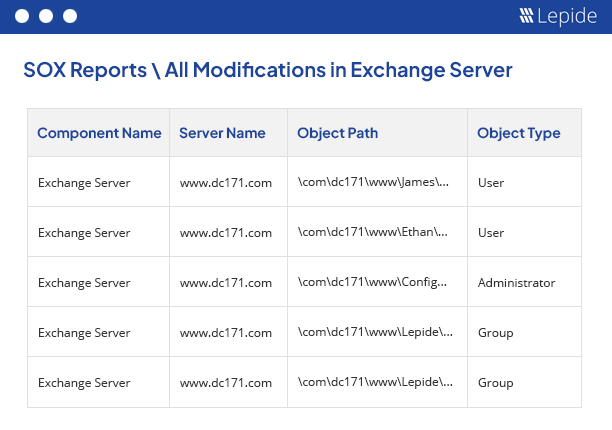
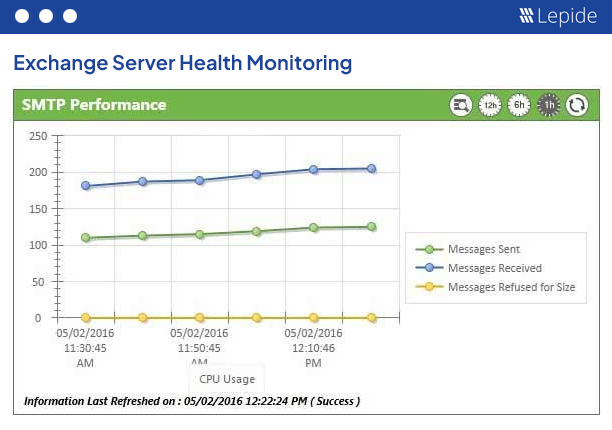
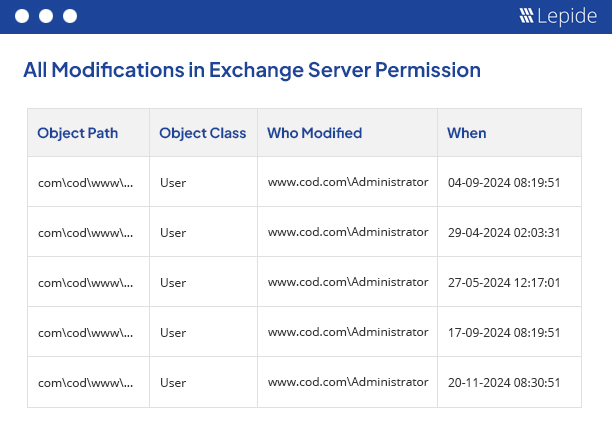
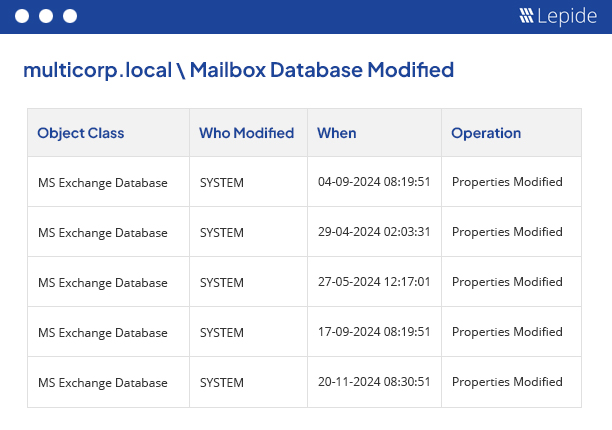
Our powerful Exchange auditing tool (for on-premises and online) gives you valuable insights into mailbox access, permissions changes, configuration changes and more. It helps maintain the integrity of your Exchange infrastructure.