You can often tell when an Active Directory environment is carrying more risk than it should. The clues aren’t usually the headline issues, they’re the subtle ones you only notice after seeing enough incidents. An admin signing in from a laptop that shouldn’t touch privileged credentials. A service account with permissions that don’t match its actual function. A legacy project group that somehow still has write access to critical OUs. These small inconsistencies point to an environment running on drift rather than intent. Implementing least privilege is how you take that control back.
Least privilege is about ensuring that one mistake in the directory doesn’t result in catastrophic failure of your enterprise. This guide provides a complete picture of how to implement least privilege in your Active Directory, concretely, without shortcuts.
10 Actionable Steps to Implement Least Privilege in Active Directory
For least privilege to work in Active Directory, you need a framework that impacts every aspect of how accounts, rights, and systems operate. The following steps create that framework, each of which addresses a different area of weakness in AD, and together, you’ll have a model you can operate, monitor, and defend without guessing or relying on outdated assumptions.
- Start With an Inventory That Reflects the Environment You Actually Have
- Use a Tiered Model to Control Where Privileged Credentials Can Appear
- Bring Service Accounts Under Control With a Careful, Repeatable Process
- Substitute Permanent Administrative Access for Expiration
- Delegate Real Task vs. Job Titles
- Track Privilege Age and Privilege Velocity to Monitor Drift
- Secure Endpoints to Prevent Privileged Credential Leakage
- Automation of Privileged Drift Detection
- Build Safe Rollback Procedures to Avoid Permissions Hoarding
- Build Governance That Keeps Least Privilege Alive After Cleanup
1. Start With an Inventory That Reflects the Environment You Actually Have
You must review permissions on accounts, groups, and delegated rights across domains and OUs. For that, you will need to:
- Export every privileged account group membership (Domain Admins, Enterprise Admins, and Schema Admins), and list every user and service account in each of these groups.
- Export ACLs on critical AD objects, Computer objects, OU permissions, GPO permissions, etc. Search for non-standard ACEs that grant Write, Reset Password, or Modify Owner.
- Search for service accounts that have SPNs, or accounts that are permitted to logon as a service; those are high-value targets for Kerberoast and other credential theft.
Use scripts and tools to look at privileges across the environment, but don’t believe a single report. Cross-reference group membership with ACLs and logon auditing to determine who actually accessed the account.
2. Use a Tiered Model to Control Where Privileged Credentials Can Appear
Attackers rarely take over a domain in a single move. Attackers move through machines over time. A tiered model stops or limits that movement by explicitly stating where different types of privileged accounts may sign on.
Define Tiers Explicitly: There needs to be a separation between normal users and admins. You should create three functional tiers.
- Tier 0: Domain controllers/forest systems
- Tier 1: Application/server administration.
- Tier 2: User/endpoint administration.
Enforce Logon Restriction to Tier: Tier 0 accounts should not sign on to Tier 1 or Tier 2 systems. Tier 1 accounts should not be signing on to Tier 0. Privileged work should only take place on secure admin workstations. When a privileged session appears on a normal workstation, that workstation becomes an easy target. Enforcing tier boundaries will prevent an attacker from jumping through accounts into the most privileged credentials and moving through the organization.
3. Bring Service Accounts Under Control With a Careful, Repeatable Process
Service accounts pose more risk than user accounts, as they have broad rights and receive little review on a regular basis. Cleaning service accounts requires greater planning because you want to avoid breaking applications.
- Document Purpose, Scope, and Behaviors: A service account is often generic and used in systems you are not familiar with. It is important to figure out what application or service is using the account, what servers are running the application, what objects it communicates with, if it uses SPNs, and if it supports modern Kerberos encryption. This provides you an understanding of what rights are important, that you will not accidentally remove or leave behind old permissions you do not want.
- Remove Rights Account Does Not Need: Service accounts tend to have very wide permissions. Generally that is because someone needed a fix at the time it was deployed and created service accounts with more rights than necessary. If you have a service account and it needs permissions to access an OU, then only grant it permission at that OU node, or if it only runs on 3 servers, then provide authentication to those machines only. Removing unnecessary rights will greatly reduce the impact of a compromise.
- Limit Logon Locations to Known Servers: Utilize the “Log On To” feature in ADUC to limit the account to authenticating only on approved hosts. This action prohibits an assailant with service account credentials from using the service account elsewhere across the network
- Transition to gMSA Where Applicable: Group Managed Service Accounts automatically manage service password rotation, taking the responsibility for password management away from the user. If the application can be configured to support gMSA, it will provide a higher level of security without introducing any operational overhead.
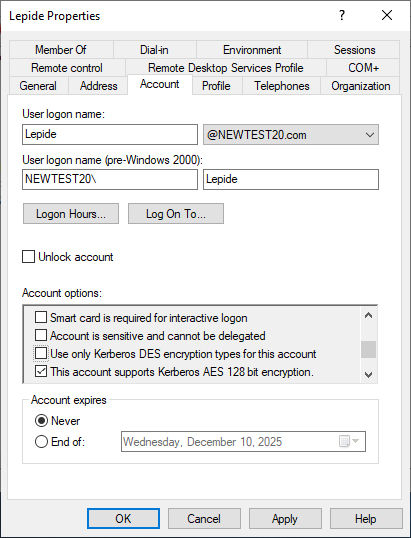
- Enable AES Encryption: Properly enable AES using the following method:
-
- Open Active Directory Users and Computers (ADUC).
- Open the Properties of the account.
- Select the account tab
- Scroll down to the Account options.
- Check the box for ‘This account supports Kerberos AES 128 bit encryption.’
- Be sure ‘Use only Kerberos DES encryption types for this account’ is deselected.
- Apply the change.
If enabling AES causes issues, the application may rely on older encryption. Plan an update or isolate the system until it can be modernized.
-
- Review on a Regular Basis Service Accounts: Set a timetable reviewing service accounts at least once every year. Service accounts tend to automatically collect unnecessary rights unless reviewed.
4. Substitute Permanent Administrative Access for Expiration
Ongoing administrative access is one of the most common sources of privilege risk; if an attacker steals a permanent privilege credential, that account can directly gain access to domain control. By substituting temporary elevation access, the exposure window is reduced. Each elevation should be directly connected to a ticket with a legitimate business purpose.
Approvals are temporary and rights should be set to expire. Activities done within the elevation time frame should be logged. You do not require an extensive tool for your first iteration; even going as far as removing group membership in a script after a scheduled time reduces risk in the immediate.
5. Delegate Real Task vs. Job Titles
Most users do not need Domain Admin to do their jobs. Delegate access within specific things, password resets, workgroup management, workstation join, at the OU level.
Here’s how to do it properly:
- Use the Delegation of Control Wizard in Active Directory User and Computers (ADUC).
- Limit the permissions to the least required scope for them to function.
- Document who requested the access, who approved it, and the time period allowable
If you cannot defend an account with escalated rights, schedule the user to have the escalated rights removed.
6. Track Privilege Age and Privilege Velocity to Monitor Drift
You require a single metric that demonstrates progress – Privilege Age, i.e., the number of days since an account was last either assigned any admin permission or utilized an assigned admin permission. Accounts with old privileges that haven’t been used are ‘hidden’ risks. The Privilege Age is what converts a cleanup into a measurable outcome. If your environment generates privileges faster than you remove or review them, you are losing ground. Monitoring this metric gives you agency over the pace of change.
You can leverage a simple Privilege Age tracker. Download the ready-to-use Privilege Age Tracker Template. You can use or modify this format in your environment.
Create a review cycle. Any account is flagged that has not engaged in an admin action for at least 90 days. Report the average privilege age in the review every quarter. If your management reads numbers, give them one. This one reduces the risk.
7. Secure Endpoints to Prevent Privileged Credential Leakage
The concept of least privilege can only exist when privileged credentials are secure. When an attacker can access endpoints resulting in the privileged account login, it is easy to extract privileged credentials.
Remove local administrator rights from all users. Require privileged access for administrative tasks, only from administrative workstations. Enable Credential Guard. Disable any Kerberos Encryption Type that is not secure after testing. Limit RDP connections to a predetermined set of systems. Prevent administrators from running administrative tools on user-based Endpoint devices. These steps will achieve security in locations where privileged credentials are at risk.
8. Automation of Privileged Drift Detection
Privileges change on a daily basis. Reviewing four times a year, while is required, will not be timely enough to detect privileged drift.
Setup automated alerts to identify:
- New members of Domain or Enterprise Admins.
- Changes to permissions on GPOs or OUs.
- New Service Accounts with SPNs.
- Changes to Encryption Types on existing service accounts.
Alerts should be configured to create tickets. Someone should own each ticket, validate the ticket, and document the resolution. Automation is necessary to uphold the integrity of your least privilege model.
9. Build Safe Rollback Procedures to Avoid Permissions Hoarding
People hold onto the same permissions as a process of not breaking anything. When rollback is simple, cleanup becomes the expected process.
Create a rollback principle that works:
- Snapshot the AD state (group memberships and ACLs) before making any large changes.
- Pilot OUs and test your changes there first.
- Have a rolling removal process and check for failures in each wave.
- Keep a script to restore old settings in 5 minutes and document the steps on how to restore.
When rollback is simple, teams are less likely to keep the permissions in place ‘just in case.’
10. Build Governance That Keeps Least Privilege Alive After Cleanup
Governance is what assures sustainability of your work once you get past the initial cleanup. Without it AD will drift back into an unsafe space.
Quick Checklist to Build Governance
- Every privilege request connects to a ticket and a reason and an expiry.
- All privileges are re-certified quarterly on all memberships.
- Privileged Age check on a monthly basis with charts visible to the leadership when appropriate.
- Clear Ownership as to Who approves, who implements, who reviews.
- Training for every new admin on how to first request a temporary elevation.
How Lepide Helps
With Lepide Auditor for Active Directory, you get clear visibility into the changes that matter; group membership updates, permission shifts on OUs and GPOs, service account modifications, and unusual privileged logons. You see the important activity without digging through event logs.
You also need a way to show progress and confirm that access stays under control. Lepide’s state-in-time reporting lets you compare the environment before and after cleanup, track if old rights start creeping back, and support reviews without relying on manual checks. It gives you a consistent view of how privilege moves across the directory so the improvements you make don’t slowly erode.
You will know least privilege is in motion when:
- Only a small handful of accounts are in Domain Admins;
- Service accounts are utilizing AES, and gMSA by default;
- All admin logon occurs on approved workstations;
- Privilege-age numbers are declining quarter after quarter;
- Alerts of unauthorized changes are received in minutes, not weeks.
Conclusion
Least privilege only works when it becomes part of how you think about your directory, not just in how you set it. The real win is when access goes from an afterthought to a consideration of your team with the same seriousness as uptime. At that point, you stop chasing issues and start preventing them. The journey is long, but the reward is peace, an AD where surprises are few, fixes are predictable, and each right in the system has a reason to exist. That is the directory attackers are dreading to walk into, and it is the one your future team will thank you for eventually building.
If you want to see how these controls look in a real environment, you can try Lepide for free by downloading the free trial or schedule a demo with the team. It will show you exactly where privileges are drifting, how access is changing, and what needs attention before it becomes a problem.