What is a Service Account?
A Service Account is a non-human privileged account through which an operating system executes one or more Windows-based applications or services. Applications or services can utilize a service account for connecting with the operating system as well as with other network resources. A service account offers means to assign identity and permissions to a computer program that executes a specialized function. In Windows roles, for instance, service accounts are employed in running Exchange, SharePoint, SQL Server, and Internet Information Services (IIS). A service account defines the security context of the service and provides the resources to which the service has access at the network or local levels and what it can do with them.
What are the different types of Service Accounts?
There are various categories of service accounts based on their functionality and intended use. Below are examples of the most common service accounts.
- Local Service Accounts: The term “local service accounts,” also known as “built-in local user accounts,” describes the kind of service account that is automatically associated with services or processes that are only executed on a particular system or device. Service processes are utilized to run services or processes that are local to the machine and created and controlled on the system locally. Local service accounts are associated with system services on the machine; they are not shared between multiple devices or systems. LocalService, NetworkService, or LocalSystem are three predefined service accounts that could be utilized to run a program locally on a computer. The predefined service accounts utilize local information for the purpose of accessing a network resource, where required credentials may or may not be needed.
- Domain Service Accounts: Domain service accounts are those single user accounts under Active Directory that are created solely for executing services and programs on servers. Used extensively, these AD accounts are best suited for those services that need to access common resources like file servers or databases. To enable services or apps to access network resources with ease, these service accounts are established in Active Directory. These can be in the form of one account per service, or a single account that is shared by multiple services.
- Managed Service Accounts(MSAs): It’s known as sMSAs, or standalone managed service accounts.In Windows Server 2008 R2 or Windows 7, Microsoft introduced more contemporary account types known as Windows Managed Service Accounts.The service accounts were created with enhanced administration and security in mind, and they were made to handle password management automatically. In the accounts domain, managed service accounts are mapped to a machine or service and are readily accessible from any of the services operating on the systems. By removing the need for the administrator to manually update each service account’s credentials, this was added to Active Directory with Windows Server 2008 R2, adding a layer of protection. A complicated password that is created and changed is required for managed service accounts, or sMSAs.
- Group Managed Service Accounts (gMSAs): The Group Managed Service account is an alternative for the MSAs. The Group Managed Service account has the same functionality of an MSA because it can schedule tasks and be shared on multiple servers. GMSAs can be utilized in domains that may have DCs that may be running older operating systems. However, the installation and management of a GMSA can only happen on Windows Server 2012. There are no functional requirements for forest and field levels. The PowerShell cmdlet New-ADServiceAccount can be used to create a gMSA. The gMSA will be created and stored in the Managed Service Accounts container. It will be installed on the host machine using the cmdlet Install-ADServiceAccount.
What are the Key Differences between User Accounts and Service Accounts?
Below are some key differences between user and service accounts:
- Purpose: The user accounts are provided to the people who need access to the systems for working purposes. It may range from installing servers to coding, maintaining files, emailing, or utilizing a CRM. Non-human users are addressed by a service account. The capability to access resources and execute operations such as data processing, transferring files, or calling APIs without a human having to log in every time is facilitated through automated tools, scripts, managed virtual machines, automated jobs, or applications.
- Ownership: The user account belongs to a particular person, e.g., an IT administrator, project manager, or software developer. The feature that will connect each activity created by the user account to the individual will enforce accountability and traceability. The service account, however, will connect to a program or service, such as a monitoring tool or CI/CD pipeline. It is bound to the function or process it serves but not to any individual. The security interfaces between human users and automated systems are maintained partially by this segregation.
- Permission Considerations: The permissions are generally based on the user’s role within the company. A regular employee might have restricted access, while an administrator would have full access. Unless managed correctly, this might lead to accounts with overprivileged permissions. But the “principle of least privilege” must be applied to the service accounts, which must have only the barest minimum of rights needed to perform their work. For instance, a backup script needs no permission to modify or delete actual files.
- Enhancing Security: It is simpler for data breaches to take place because user accounts have a larger level of access than they really need. But since user accounts are connected to individual accounts, the IT staff can establish who is authorized to access certain data and applications. The service account, in contrast, lets them access resources and automate operations without the involvement of humans. For applications that need to run continuously or run tasks such as data processing, reporting, and monitoring, this is helpful. This helps in enhancing security.
- Auditability: Each action performed using a user account can be mapped directly to the individual who established it because every user account is associated with an authorized person. It makes it easy to perform audits and monitoring, assist with compliance reporting or inquiries, and more. Yet it is harder to map actions back to a unique individual because they are linked with people rather than service accounts. Employing clean naming conventions, organizing accounts based on purpose, and ensuring that logs record enough information to be able to prove what the service account is accomplishing and when are all needed to preserve auditability.
Why are Service Accounts Important?
Below are reasons why service accounts are important:
- Improved Performance and Reliability: The reliability and performance of the system are boosted by service accounts. The automation capabilities of service accounts allow them to execute tasks quickly and reliably, reducing manual intervention and the associated delays. Organizations can enhance the overall reliability of their systems, speed up reaction time, and reduce downtime by automating IT operations. Service accounts also facilitate resource optimization and load balancing, further enhancing system performance.
- Enhance Security: By providing applications and services with a distinct identity, the service account enhances security. Organizations can minimize the possibility of unauthorized access, impose the principle of least privilege, and manage access limits in an efficient manner using distinct identities and credentials. By providing organizations with the ability to track and audit the actions performed by applications, the service account also enhances accountability by facilitating incident investigations and compliance programs.
- Streamlined Administration Tasks: Businesses can simplify administrative tasks through centralized management of service accounts. Simplifying the task of providing, changing, and terminating service accounts as and when required lessens the administrative burden of dealing with individual user accounts. Organizations can also ensure reliable and efficient management of service accounts across their IT infrastructure by standardizing and automating processes.
- Serve as a Proxy: Service accounts can serve as proxies for human users to perform tasks that your business might consider sensitive or that require greater permission levels. To secure the network, this is necessary. Because only authorized services and applications can perform certain tasks, your business can protect its network from security-related mishaps by taking the human factor out of such tasks.
What are the Challenges in Service Account Management?
Below are some challenges associated with service account management:
- Handling Process is cumbersome: This is one of the significant challenges for service account management in which the manual process of changing the password for service accounts at a frequent interval is extremely time-consuming and expensive for the organization. In addition, keeping the usage of these accounts active is a challenge for organizations.
- Identification of Owners: The second hurdle is also considered to be the biggest one that companies have when implementing service account management procedures. Most companies have trouble or do not know who is supposed to be the owner of each service account. Locating the owner of the accounts is an extremely challenging task since there are thousands of service accounts on multiple accounts in a company. Due to the nature of these accounts, employees are always reluctant to assume ownership of them. It is very important to recognize and assign service account ownership so that they can be properly managed.
- Searching Authoritative Source Data: Most organizations do not have a source for all their non-human service accounts. Locating all the service accounts and their usage points was the initial problem that most companies encountered in planning service account management. The service accounts are widely spread across various servers and platforms within large companies. Each of the thousands of such servers contains a number of service accounts. Therefore, it is challenging for companies to track them all
- Lack of Auditing: Because of the ignorance regarding the importance of service accounts, the utilization of service accounts is not properly audited in most organizations. Consequently, when cybercriminals hold a service account to obtain sensitive data no traces were left behind to trace the malicious activity. With mounting government compliance requirements, the burden to secure data and meet regulatory requirements is a must. The penalty for failing to comply with the standards (e.g. PCI, SOX, HIPPA, etc.) is harsh. Not only the organization imposes heavy fines on a failure of the audit, but it may lead to the total failure of the business in worst-case scenarios. Therefore, the effective setup of service account auditing becomes challenging for the companies.
- Not Classifying Service Accounts: One of the challenges is that certain companies do not include service accounts in their information security policies, rather focusing on classifying human account types like employee, contractor, vendor, partner, etc. This major difference leads to the service accounts being neglected in terms of the overall security goals of the organization.
What Are the Best Practices for Preventing the Misuse of Service Accounts?
Below are the tips for service accounts security and management:
- Eliminate unnecessary privilege access
- Create service accounts from scratch
- Avoid putting service accounts in built-in privileged groups
- Deny access permissions to service accounts through ACL (DACL)
- Take away redundant user rights
- Use the “Log On To” option
- Service accounts should be restricted to log on at prescribed times
- Secure service accounts by doing password configurations
- Audit service accounts
1. Eliminate unnecessary privilege access
When creating a service account, always keep in mind that it should only have the minimum privilege required to complete the task at hand. For example, a few additional privileges that you can shed are remote access functionality, terminal service logons, internet and email access and remote control rights.
All these settings can be configured easily. The following image shows denying access to network access permissions that is available on “Dial-in” tab.
You have to open “Active Directory Users and Computers”, access “Users” container, and right-click a user account and access its properties. Switch to “Dial-in tab”.
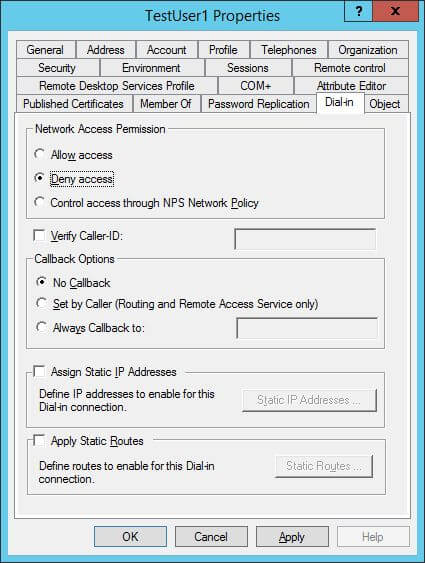
Figure 1: Denying unnecessary privileges
2. Create service accounts from scratch
In some of the past cases of service account misuse, it was found that the accounts had extra privileges because they were created by copying old accounts with high privileges. When you create a new service account by copying, you run the risk to inadvertently assigning excessive privileges, because the old account’s role may differ from the new one. Copying lightens the administrative burden, but it comes with a risk!
3. Avoid putting service accounts in built-in privileged groups
Assigning service accounts in built-in privileged groups, such as the local Administrators or Domain Admins group, can be risky. Everybody in the group will know the service account’s credentials and those credentials can be misused. Additionally, tracking the offender will be difficult as several administrators in that group will know the credentials.
If, for some reason, you have to assign a service account to a privileged group, then create a custom group and add the service account to that instead. Then, explicitly deny access to other accounts for that group. Such measures will eliminate the possibilities of service account misuse.
4. Deny access permissions to service accounts through ACL (DACL)
To secure important objects, like files, folders, shared folders and registry objects, from service account misuse, you can use the ACL (Access Control List)/ DACL (Discretionary Access Control List).
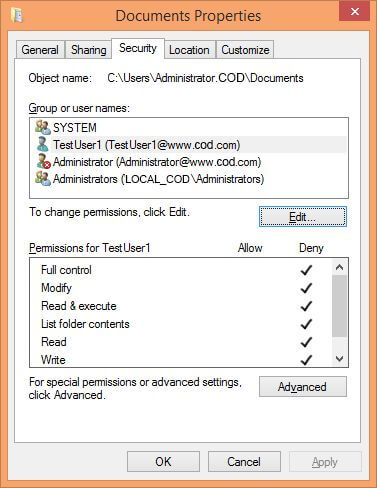
You can use the deny checkbox in the object’s properties sheet to disallow permissions to the service account. For example, perform the following steps to deny access to a folder named “Documents”:
- Right-click “Documents” folder and click “Properties”.
- In folder properties, switch to “Security” tab.
- Here, click “Advanced” button to access the Advanced Security Settings.
- In “Permissions” tab of “Advanced Security Settings”, click “Add” button. “Permission Entry” window appears on the screen.
- Click “Select a Principal” link to access the “Select Users….” dialog box.
- Type the name of Service Account and click “Check Names”. After verifying the name, it formats it as a URL.
- Click “OK” to come back to “Permission Entry” window.
- Here, select “Deny” in “Type” drop-down menu.
- Click “Full Control” to deny all permissions.
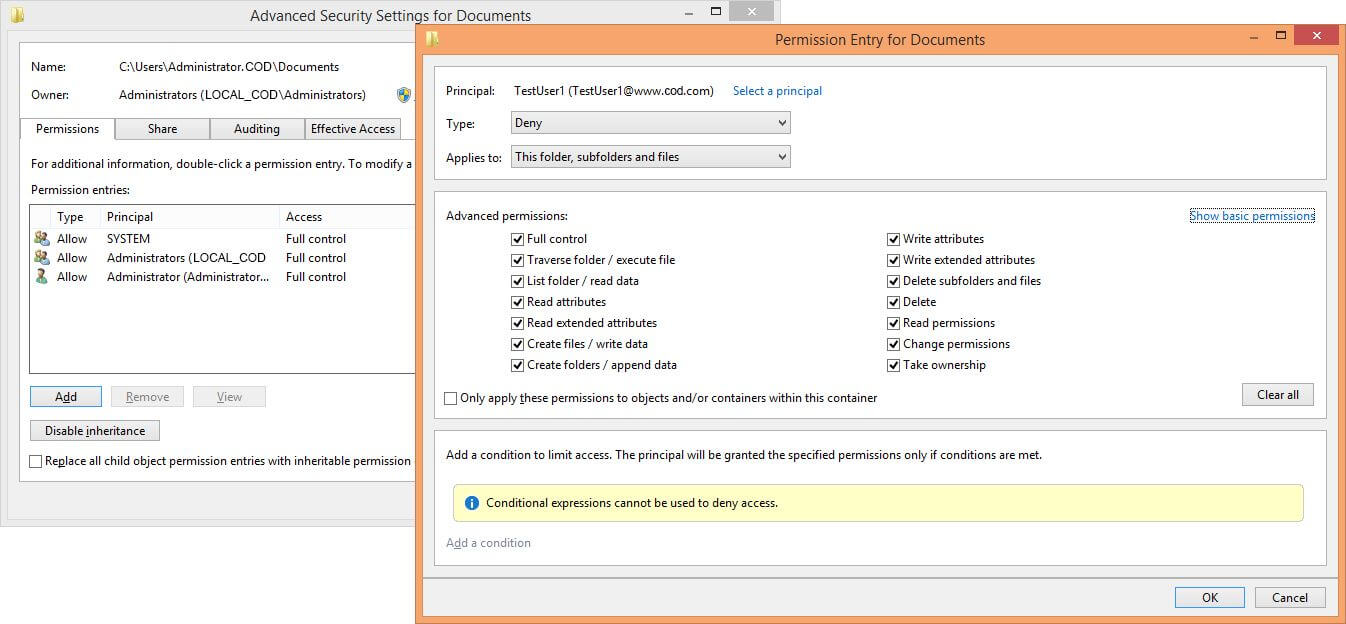
- Click “OK” to finalize your selection. It takes you back to “Advanced Security Settings”.
- Click “Apply” and “OK”
After performing the above steps, permissions inherited from the parent are overridden. This way, even if the service account is compromised, vital resources will not be accessible to hackers.
In the following image, the “Documents” folder’s ACL has been shown (available under the “Security” tab of the folder properties):
Figure 3: ACL of “Documents” folder
5. Take away redundant user rights
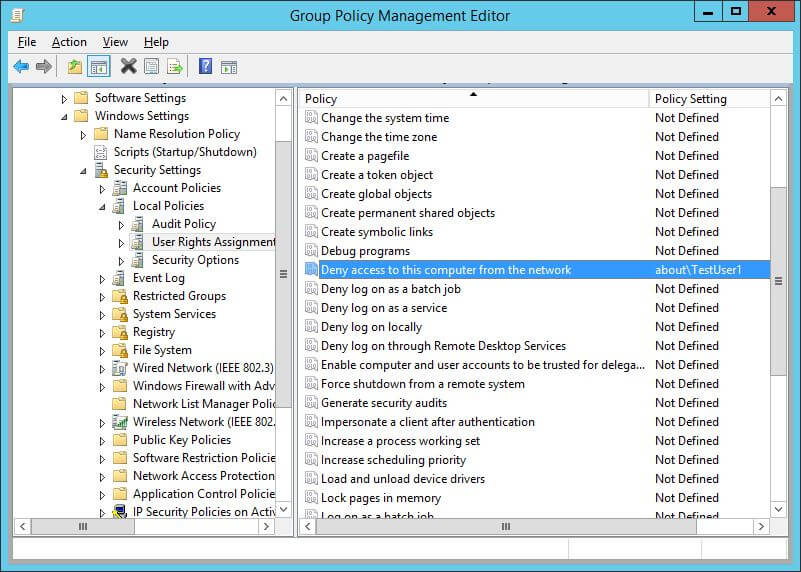
Review and eliminate unnecessary user rights. Some of the common user rights that can be explicitly denied are “Deny access to this computer from the network” and “Deny logon as a batch job”.
To implement this, create a custom Group Policy Object (GPO) at domain level that denies a service account the right to log on through the network or as a batch job. Go to “Control Panel” “Group Policy Management Console”. Select a policy and edit it in “Group Policy Management Editor”. In the GPO Editor, you have to go to “Computer Configuration” “Policies” “Windows Settings” “Security Settings” “Local Policies” “User Rights Assignment”.
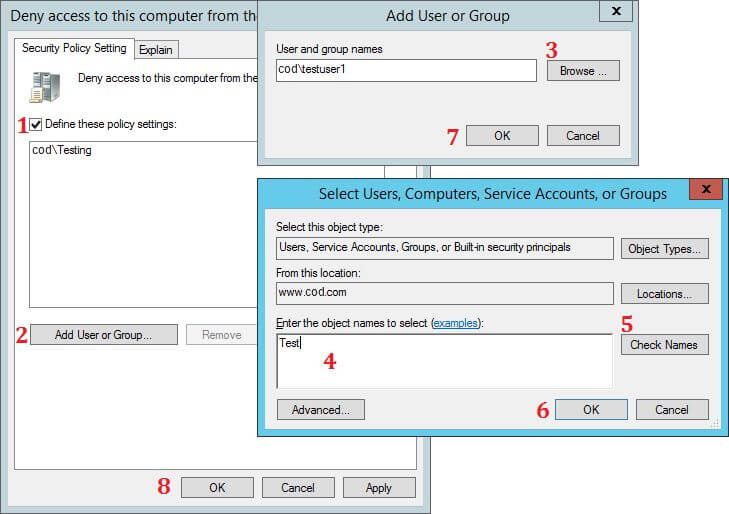
Figure 4: Path of “Deny access to this computer…” policyHere, select and modify “Deny access to this computer from the network” policy. The steps are shown in the following image:
Figure 5: Configure “Deny access to this computer…” policy
6. Use the “Log On To” option
You can limit the number of computers to which a service account can log on by using the “Log On To” option. This way, service accounts will not be able to access file servers with sensitive data.
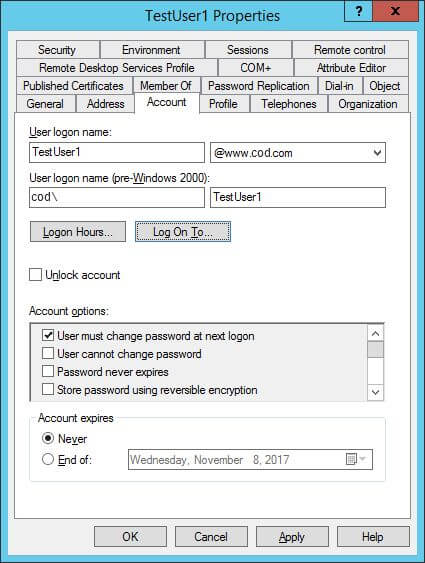
To do this, open “Active Directory Users and Computers”, go to the container (or organizational unit) where the service account is located, right-click the service account and click “Properties”. Switch to “Account” tab.
Figure 6: Account Tab of User PropertiesClick “Logon To” button to access the following window.
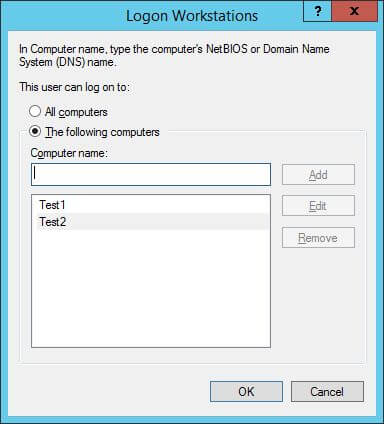
Figure 7: Add WorkstationsSelect the option “The Following Computers”. Then type the computer name and click “Add”. Here you can add the name of those computers, on which any user with the selected Service Account can login. This service account will not work on other computers that are not listed here.
7. Service accounts should be restricted to log on at prescribed times
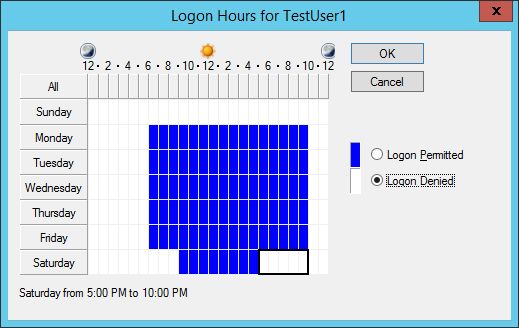
Service accounts should be configured to log on only during a specified time of the day. You can implement this plan by using the “Log on Hours” option that imposes time and day restrictions. To apply that setting, click “Logon Hours” in “Account” tab of User Properties, as shown earlier.
Figure 8: Configure Logon Hours
8. Secure service accounts by doing password configurations
You can use two password options to secure a service account, “User cannot change password” and “Account is sensitive and cannot be delegated”. The first option ensures that nobody but only administrators control password, the second option ensures that nobody delegates the account for misusing its privileges to connect to local or remote machines. Both options are again listed in the same “Account” tab of use properties, as depicted earlier.
9. Audit service accounts
You must enable auditing for all service accounts and other related objects. These audit settings can be configured locally at the system level or through GPO at the network level. After you have enabled the auditing, you must continuously check the logs to protect the service accounts.
How Lepide Helps Enhance Active Directory Security
Lepide Auditor for Active Directory enhances Active Directory security by actively auditing and alerting administrators about important changes. In the context of securing service accounts, the Lepide solution can help with the following aspects:
- Removing unnecessary privileges: By continuously monitoring AD for important changes, our solution can identify and flag unnecessary access privileges granted to service accounts. This ensures that only the required permissions are assigned, reducing the risk of unauthorized access.
- Knowing when accounts are placed in built-in privileged groups: Our solution can provide alerts whenever a service account is added to a built-in privileged group, such as the Domain Admins or Enterprise Admins group.
- Monitoring service account logon times: Our solution can monitor changes to service account logon hours. If any unauthorized changes are detected, it will alert administrators, ensuring that service accounts are restricted to log on only at prescribed times, as defined by the organization’s security policies.
- Managing inactive user accounts: Our solution can automatically identify and notify administrators about inactive or unused accounts. This helps streamline user management processes and ensures that only active and necessary accounts are retained.
- Auditing service accounts: Our solution can provide detailed logs and reports on service account activities, including logons, privilege changes, and group membership modifications. This allows organizations to conduct audits, meet compliance requirements, and identify any misused or compromised service accounts.
If you’d like to see how our Active Directory auditing tool can help to secure your Active Directory service accounts, schedule a demo with one of our engineers or download free trial today.