User Provisioning in Active Directory needs to be easy but too often it’s not. It begins slowly enough, but over time, manual processes accumulate, access requests become inconsistent, and before you know it, you are tracking down accounts, permissions, and cleanup procedures that should have been automated. This blog explains what user provisioning in Active Directory is, how it works in a typical AD setup, where things might go wrong, and how to manage it. It is merely a straightforward, useful way to create user accounts, manage them, and remove them without any hassle.
What is Active Directory User Provisioning?
The process of creating, managing, and deploying user accounts across AD systems is known as Active Directory user provisioning. Active Directory entails having control over users’ lifecycles from an integrated directory service, including creation, granting of permissions, modifications, and suspension. Depending on their roles, the process gives employees the proper rights to use corporate resources. For instance, AD user provisioning assists in configuring an employee’s digital identity at the time of hiring. It puts them in the right groupings.
What is the Importance of User Provisioning in Active Directory?
User provisioning is a crucial part of Active Directory Identity and Access Management (IAM), ensuring that users have appropriate access to organizational resources throughout their lives. Here’s why it is important:
- Enhanced Productivity: Organizational effectiveness is improved by effective user provisioning within Active Directory, which provides new employees with instant access to all systems, tools, and resources that they need when joining an organization. IT personnel and employee productivity are both aided by automated user provisioning. IT professionals can dedicate more time to higher-value work by minimizing the time taken to deal with permission problems. Offering quick access to necessary apps and files becomes difficult without an effective user provisioning solution, leading to delays and lowering worker productivity. Automation reduces disruptions and streamlines work processes by giving employees timely access to resources they require to complete projects.
- Improved User Experience: Effective provisioning is the path to a smooth user experience. Once the users are properly configured in Active Directory, they are able to immediately access the necessary systems and tools. In addition to enabling consistent access across any platform, provisioning enables users to leverage services without requiring constant authentication through integration with Single Sign-On (SSO). This implies less friction and greater user satisfaction. Also, automated provisioning updates users’ rights to access their new jobs in the company, reducing downtime and maintaining business continuity.
- Better Security: Security is the most important aspect of IT administration and is significantly achieved through user provisioning. Undesired access is reduced through role-based and policy-based provisioning of access by Active Directory. De-provisioning is referring to removal of access when employees are leaving the organization or changing job functions, and it is no less vital in avoiding potential data breaches. With central enforcement of password policies, access restrictions, and multi-factor authentication, AD makes sure that sensitive data is shielded from insiders as well as outsiders, and also minimizes the possibility of human mistakes.
- Effective Lifecycle Management: Active Directory user provisioning delivers all stages of the lifecycle, including onboarding, transition, and offboarding. A quality provisioning process allows employees’ accounts and access to be in place as soon as they are hired by the company. Their roles are updated to support their new roles whenever the employees change function or department. Also, whenever an employee departs from the company, access is closed down at once, and their data may be migrated or archived. The lifetime strategy reduces risks, ensures compliance with legislation, and enables streamlined internal processes.
- Centralized Identity Management: One of the biggest advantages of Active Directory is its centralized identity management. Because AD remains the single source of authority for security control and user identity, it is considerably simpler to manage users on multiple platforms and systems. It can mandate uniform authorization models, security policies, and naming conventions because of this kind of centralized model. With technologies like Active Directory Federation Services (ADFS), companies can securely authenticate cloud services and external applications without losing control of user identities. All things being equal, this consistency improves operational efficiency and security.
- Audit and Control: Strong AD auditing capabilities offered by user provisioning solutions enable businesses to maintain tight control over users’ entitlements. With this practice, over-provisioning risk is avoided, and users receive appropriate access to individual tools and permissions. The ability of organizations to monitor and enforce access management with ease makes maintaining security and compliance simpler. Automating the provisioning of users helps organizations maintain an audit and control of the management of user access, accelerate work processes, reduce risk by automated integration, and produce a digital world that is secure and efficient. The initiative enhances overall cybersecurity controls and prevents security breaches such as unauthorized access to sensitive data
What are the Common Challenges in Active Directory User Provisioning?
It is crucial to know the AD provisioning process, but there are obstacles to making it successful. These are some typical challenges you can expect to encounter.
- Manual Errors: Accounts are provisioned manually, but invariably errors crop up. Active Directory provisioning is still manual in occurrence, especially in companies lacking any automation tool. The IT team must configure settings for mailbox manually, group users manually, provision user accounts, and then carry on with permissions. It is laborious, and with it comes a great probability of having errors mostly in the form of typographical and departmental assignments. With increasing expansion of the company, manual provisioning at a particular point in time is a nightmare to maintain, resulting in IT operation bottlenecks.
- Inconsistent Role and Data: Without a centralized model, departments may assign roles, access, and data differently. It is easy for inconsistencies to end up in user accounts if there are no pre-existing templates or mandatory data structures. This inconsistency has the potential of elevating the chances of access misuse and complicates auditing. For instance, an administrator types “IT dept” and another one types “information technology.” These differences affect email distribution lists, dynamic group membership, and reporting tools based on accurate, reliable data.
- Complicated Organizational Structure: Mostly, Active Directory forests or domains are common in large organizations, they are inherited occasionally due to mergers and acquisitions. Administration of user accounts in such complex systems involves a lot of planning and preparation. Hybrid deployments get more complicated when Azure AD is synchronized with on-premises AD. Unique scripts and solutions are often required to fulfil specific business needs from hybrid setups.
- Intrusion Compliance Issues: Rigorous access and accountability controls are the prerequisites of GDPR, HIPAA, and SOX. Failure to conceal or de-provision access rights to sensitive data will lead to penalties at the time of an audit. Thus, it will have been quite a long process to establish compliance, without automatic reporting and monitoring of user provisioning data to make it error-free and swift. In other words poor provisioning procedures may equal fines, non-compliance, or reputational damage.
- Hybrid and Cloud Sync: Due to the fact that cloud directories like Google Workplace or Azure AD do not interfere with in-premises AD IDs, businesses are increasingly considering utilizing cloud infrastructure and SaaS services. Synchronization configuration issues can lead to duplicate accounts, unsuccessful login attempts, and compromised access between computers. Azure AD Connect and other similar technologies are useful for this, but they also need to be properly set up, maintained, and cared for.
What is the Active Directory User Provisioning Process?
After understanding the importance of user provisioning, let’s break down the steps involved.
- Initial Setup: Establishing the Active Directory infrastructure is a requirement for provisioning. Organizational unit (OU) and security group setup would be included in this. By department or function, they help categorize users. The installation would include collecting user information, including the user’s full name, section, employment, job title, etc. You need to have proper and complete data because it will decide how the user account is established and what it can view afterward. This is where you need to establish password difficulty policies, account duration, and role-based access. A well-structured system is based on the installation of a properly installed system.
- Account Creation in Active Directory: Creating a user account is the second step after the initial setup has been accomplished. Creating a new user account in Active Directory from the data that was gathered is the next step. This means creating essential items such as department, title, email address, and manager, and creating a username (according to the naming policy) and initial password. To automate it and reduce errors, IT professionals usually employ automation scripts or provisioning tools. To create an Active Directory user and computer console by hand if it is necessary for a customized set-up of the account. Using scripting tools or third-party systems for provisioning automatically creating user accounts. These automatic processes help for onboarding lots of people and support consistency and productivity.
- Permissions and Access: It is necessary to offer appropriate group memberships and rights when account setup is complete. In addition to guaranteeing that employees have access to the resources they require, this would reduce the likelihood of data breaches. Rights should be updated to reflect a shift in accountability over time in order to provide secure access to data and systems. Automating employee lifecycle updates to AD can also streamline the process. A crucial aspect of provisioning is allocating suitable group memberships. IT managers can effectively provide necessary access rights according to the role and responsibilities of employees by assigning user accounts to pre-assigned security groups.
- Maintenance of Accounts: Active Directory infrastructure can be maintained up-to-date with on-going user account management. Accounts are dynamic for users. Throughout employment, a user can move from one department, project, or position to another, where there is the need to revise access. A definite process will have to exist for the IT employee to automatically update user details and re-allocate rights.Therefore, the process would include information about a user such as work titles, contact information, promotions, and changes in the department.
- Deactivation or Offboarding: When an employee leaves the organization, their Active Directory user account should be properly disabled or, if necessary, closed off. A proper offboarding process ensures that when a user departs the company, their account is quickly disabled or erased. Licenses are recovered, mailboxes are archived, all system access is terminated, and any tangible devices are given back. Before user data is deleted forever, think about archiving it for later use. This not only guarantees that the business complies with requirements but also shields it from persistent access threats. Software that automatically deprovisions also facilitates offboarding. It guarantees that no action is overlooked and that security is maintained.
What are the Best Practices for Active Directory User Provisioning?
Managing Active Directory (AD) user provisioning effectively is essential for preserving security, compliance, and operational efficiency. Planning your provisioning approach can be enhanced by the following best practices:
- Define Specific Plan: Having clear provisioning processes in place for the team to ensure standardization and avoid miscommunication is the initial and most crucial practice of active directory user provisioning. First, define roles and their respective permissions. To ensure nothing is left out, create an onboarding checklist as well, and all should follow it. Then, design an open approval process to maintain responsibility and control. Once these processes have been done, it’s time to review and update this specific provisioning plan in order to make any adjustments for changes in IT infrastructure or business needs.
- Automate User Provisioning and Deprovisioning: Manual provisioning is slow and prone to mistakes. It is imperative to provide automatic user provisioning through third-party solutions, scripts, or APIs. Automating user provisioning (via scripts, workflows, or tools like Microsoft Identity Manager, Azure AD Connect, or Okta) can help you make sure that users have the right access when they join and lose it within a few days when they go. They make it easier to create, modify, and deactivate user accounts. They save a great deal of time for your IT department, freeing them up to work on more crucial projects.
- Process to be Documented: It is mandatory to develop a comprehensive, step-by-step user provisioning guide with account setup, role allocation, and deprovisioning. These documents must be made available for access by the IT team from a single point. All provisioning actions must be recorded and made available for future use and for audits of compliance. Good record-keeping is helpful to show that standard security and access control procedures were adhered to, which is important during audits such as GDPR, HIPAA, or SOX audits. This documentation is also helpful for the team in showing compliance with cybersecurity posture.
- Regular Training: To ensure that your employees remain current on security processes, Active Directory updates, and new equipment, hold regular training sessions. Soft skills, such as working in teams, as well as technical skills, such as working with automation technology, should be addressed in training. An educated team can more efficiently handle provisioning tasks, err less, and tackle challenges confidently.
- Regular Auditing: Scheduling regular AD account audits is a further method of ensuring that users receive only the access they need at any given time. To ensure that all permissions are in order and updated, review and clean up user accounts on a periodic basis. Expired accounts and outdated group memberships must be removed, and elevated accounts (such as Domain Admins) must be tightly controlled and monitored. Periodic audits are necessary for compliance and reducing security threats
- Principle of Least Privilege (PoLP): Following the least privilege principle, employees would only be provided with access to resources they absolutely need in order to accomplish their work and only for a short period. The simplest rationale for this is that if you don’t need it, then you shouldn’t have access to it. As a best practice for user provisioning, the principle of least privilege is a good starting point in defining access controls. Following this methodology, the privileges are limited in an effort to limit the harm caused by compromised accounts and reduce the attack surface.
How Does Lepide Help?
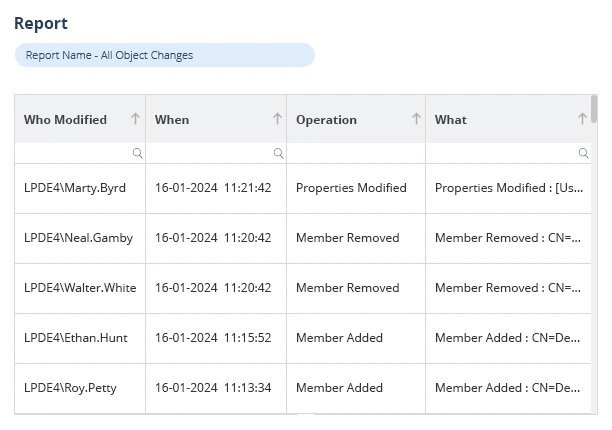
Lepide Auditor for Active Directory provides comprehensive audit trails with the important “who, where, and when” audit information for all events and changes in Active Directory. The user-friendly dashboard saves on the time and effort needed to investigate issues by presenting insights in an actionable, simple style. Lepide monitors a number of critical events for Active Directory security, including the creation, deletion, and modification of user accounts and group membership, as well as monitoring logon activity to help identify unauthorized access.
Organizations can use the tool to keep an eye on, record, and report on any changes made to their AD environment. The solution improves security and compliance efforts by offering a thorough audit record of user activity, group policy changes, and permissions updates. It keeps track of every event and modification and provides users, OUs, Group Policy objects, and AD objects with thorough audit reports
Looking to simplify your Active Directory auditing? Get started by downloading a free trial or scheduling a demo with one of our engineers.