
What do you consider to be the most significant risk to your company’s data security? Would it surprise you to know that the answer is more than likely your own users?
Whilst many organizations spend vast sums of money securing the outer perimeter of their systems, most forget to do the same for their internal IT infrastructure. This can often lead to a scenario where users have the ability to access systems and data that they shouldn’t be able to. These privileged users, although their intentions may be non-malicious, are often the cause of data breaches and general threats to your IT security.
Privilege User Abuse Facts and Figures
Massive cyber breaches, such as the recent incident at Deloitte, serve to highlight the prevalence of insider threats causing security issues. That particular breach involved a compromised administrator account that gave an attacker access to sensitive and valuable information, according to a Krebs on Security report. Another study notes insider threats are the leading cause of the most devastating security breaches, and they are very costly to remediate. The same report suggests that 74% of companies feel that they are vulnerable to insider threats, with 7% reporting an extreme vulnerability (2017 Insider Threat Report).
Why are privileged users dangerous?
Malicious motives
Often, privileged users with elevated access and may abuse the trust placed in them. This often happens when the user in question should never have had the level of privilege in the first place. If a user can see sensitive files and folders that he/she knows are valuable, that user may become, what we like to call, an opportunist threat.
Unintentional misuse
Privileged users, as mentioned already, may indivertibly be granted unauthorized access to critical data systems. Whilst the user in question may be completely trustworthy, there is still the potential that they could accidentally modify or delete an important file or folder, one they should never have been able to acess in the first place.
By attackers
Users with privileged access are always a priority target for cyber attackers. Reason being, if an attacker gets access to one of these accounts, they are able to go anywhere within the system.. In most of these cases, the legitimate user may not even realize they have been hacked until it’s too late.
How to manage your privileged users
1. Determining which users have administrative privileges
First things first, you need to know which of your users have administrative privileges. The easiest way to do this is through automated solutions, like Lepide Active Directory Auditor. It discovers, enumerates and displays the list of all privileged users with administrative rights on any specific date.
2. Audit what your privileged users are doing
Once you’ve determined which users have administrative accounts, you’ll need to actively audit and monitor their activities. However, manually tracking user activities can be a complex and time-consuming task. Lepide Data Security Platform contains over 300 predefined reports and real-time or threshold-based alerts. It enables you to track configuration changes, access to critical data events, suspicious activity and much more.
3. Managing privileged user accounts
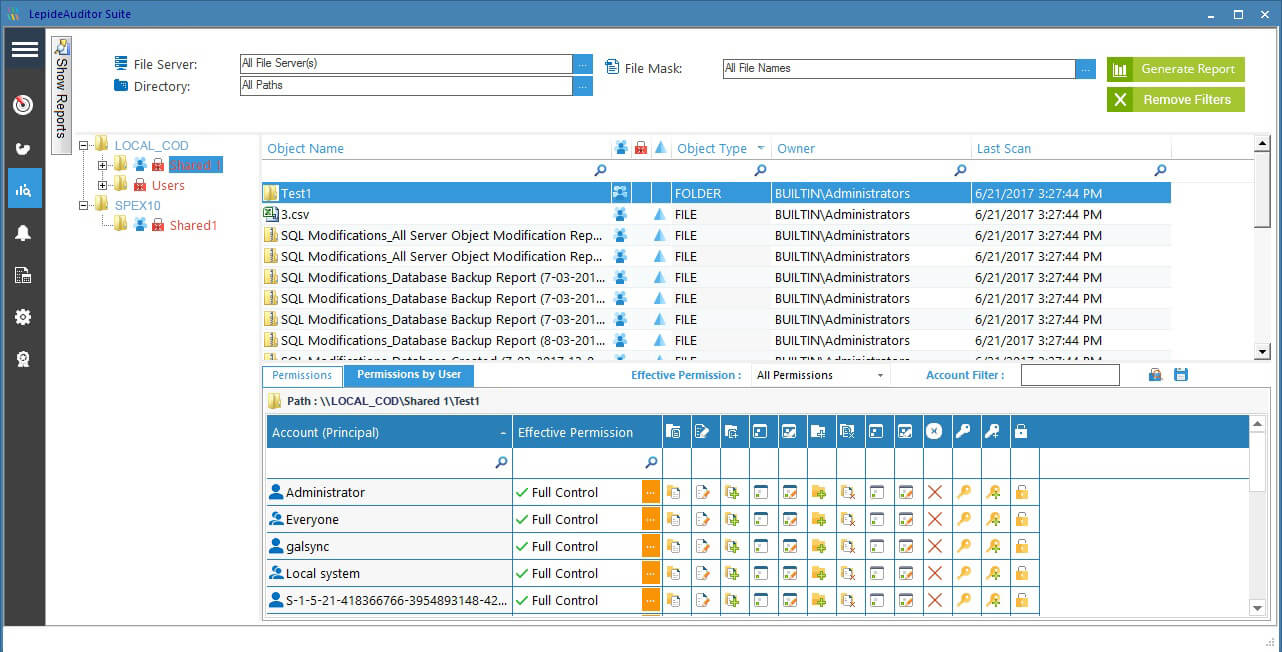
The more users you have with privileged access, the greater the chances of an insider threat leading to a security breach. Managing and monitoring Active Directory accounts and groups with access to critical data should be your number one concern. Employing the Policy of Least Privilege ensures that users have access only to what they need to do their job, and nothing more. The following screenshot of Lepide File Server Auditor illustrates the current effective permissions of Active Directory users, groups and other objects on the selected shared file or folder.
4. Revoke privileged access when not needed
Often, privileged access is granted for longer than necessary. Business roles may change, tasks may be completed, but the privileged access isn’t revoked. In such cases, these users are given an opportunity they shouldn’t have to misuse or abuse sensitive data (either accidentally or maliciously). I always recommend revoking privileged access as soon as the requirement is over. Lepide Data Security Platform helps you do this by analyzing permissions, tracking permission changes and revoking permissions using its inbuilt Object Restoration feature.
5. Audit temporary user accounts
There are multiple scenarios where temporary user accounts are required. You can create a temporary user account in Active Directory. However, you can’t forget to audit the activities of these temporary accounts to make sure that these temporary accounts get disabled or removed automatically after they expire. Lepide Data Security Platform monitors the activities of all such temporary users and notifies you whenever user accounts are disabled, their status is changed, or their account expiration date is changed.
6. Track permission changes
If someone is abusing privileges delegated to Active Directory or File Server components, you need to know. Lepide Data Security Platform helps you detect the signs of privilege abuse for all server components by defining access control rights. It also audits the level of access given to every employee to help prevent tampering with confidential data.
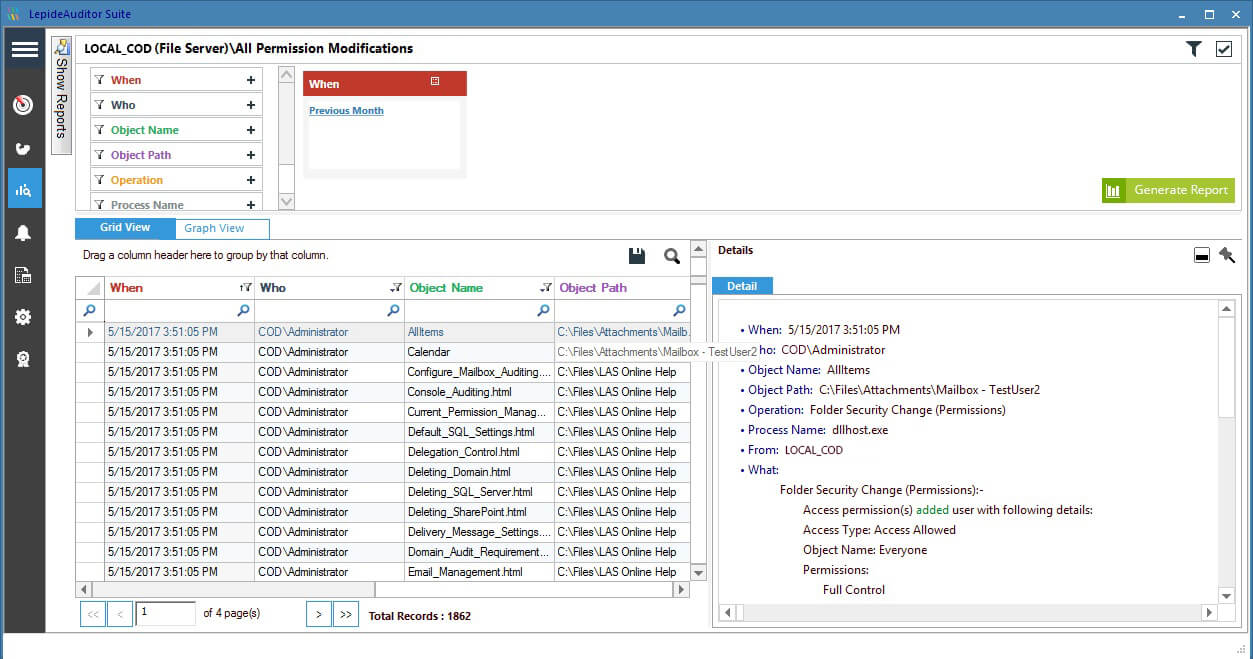
Below is a permission modification report with a description stating ‘who, when, what and where’ the permission is modified in the system.
7. Educate Staff on Password Policies
Local admin accounts can have the same password on just one platform or all of them. In continuation of user types, service account passwords are rarely changed because the change will have to also be made on all independent systems (not an easy task). However, not regularly changing and updating passwords makes the accounts easier to break in to. As a damage mitigation strategy, changing passwords regularly will ensure that anyone who has illegitimate access will not have it for long.
8. Search and clean stale, inactive accounts
A build up of obsolete or inactive user and computer accounts with privileged access is a major security hazard. Attackers often use these accounts to gain access to systems and data. This kind of attack is often very difficult to spot because the account has permission to access that data. Lepide Active Directory Cleaner helps you locate old and dormant accounts in Active Directory and apply automated actions to clean them up.
To learn more about how Lepide Data Security Platform can help you spot privileged user threats, start your free trial today.
 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why the AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why the AD Account Keeps Getting Locked Out Frequently and How to Resolve It
