
Ransomware is a serious threat to the security of any IT environment. However, despite increased awareness of the risk of ransomware, this cybersecurity threat continues to cause turmoil for businesses every day with increasing frequency and rising costs. The start of an attack often occurs at one workstation, known as an endpoint, typically after someone has clicked a link in a malicious email or visited an infected web site. Once embedded, ransomware runs silently in the background, often searching a network looking for other targets to encrypt. These can include file servers, other workstations, and backups. The more files it can encrypt, the more likely someone is to pay the ransom, regardless of the price demanded.
Once the ransomware has encrypted all the files that it can, there will be a demand that a ransom is paid, typically in cryptocurrency, and that it is paid within a certain time frame. If these conditions are not complied with, the files will be permanently locked.
While it is an essential requirement to have protection in place to reduce the risk of an attack, this protection, although highly effective, can never fully guard against every form of attack and so ransomware can still get through.
With this knowledge that attacks can and will happen, it’s crucial to look at what you should do in the event of an attack to contain any damage and ensure that the risk and spread of any malware is mitigated.
10 Steps to Recover from a Ransomware Attack
In the event that one, or several, of your company machines has become infected, what is the best course of immediate action to take? The following checklist walks you through the measures that should be taken once ransomware hits:
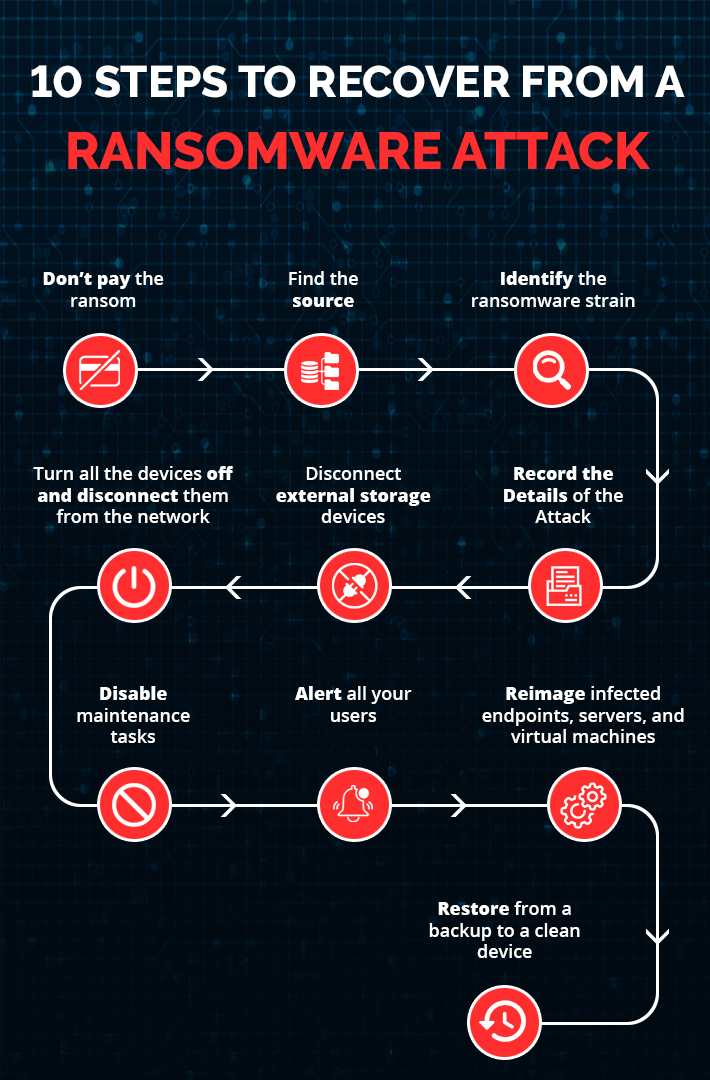
1. Don’t pay the ransom
While paying the ransom may seem to be the quickest way to get your data back and get on with your life, there is no guarantee that the person on the other end will unlock your files once they’re paid off.
2. Find the source
Now that you have taken steps to contain the immediate known damage, examine your IT environment for indications as to the source of the attack. Any system which is out-of-date is easily compromised, and it’s crucial to remember that even SaaS apps like Microsoft 365 are vulnerable. Reach out to all of your users to ascertain who experienced the first signs of the attack and when this occurred. Was it after they clicked on a link in an email? Or was there an unusual prompt coming from a web browser?
3. Identify the ransomware strain
Identifying the strain of ransomware can help to identify the encryption code you need to unlock your device. Decryption websites can provide you with decryption codes, so you can resolve the issue without paying a ransom. Knowing the strain of ransomware is also helpful to have when you go to the authorities to report the breach.
4. Record the Details of the Attack
Photograph the ransom note that appears on your screen which can be simply done using your phone. This will not only contain the details of how you are to pay the ransom, which is NOT recommended, but also can help recovery teams determine what ransomware hit you. This information is also helpful should you need to fill out any reports for police or insurance companies.
5. Disconnect external storage devices
It is crucial to keep backups of your files and these can be stored in the cloud or on external storage devices. The problem with many forms of malware is that it will also try to corrupt your external storage devices, making recovery efforts ineffective. Immediately remove external storage devices in the event of a ransomware attack to ensure they remain clean.
6. Turn all the devices off and disconnect them from the network
Once you’ve identified the devices that are infected, immediately disconnect the network cable, turn off the Wi-Fi, and shut those devices down. Many types of ransomware can spread via a network connection, so the sooner the infected devices are disconnected, the better your chances are of containing the breach.
It’s also essential to take all shared drives offline temporarily until you have determined that all the infected systems have been identified. At this stage, you should continue to monitor systems to see whether new files are becoming encrypted or disappearing.
7. Disable maintenance tasks
Many maintenance tasks on your device will continue to run as scheduled, regardless of a ransomware attack. Tasks like automatically emptying your Recycle Bin, cleaning out conversations, and deleting old files should be put on hold until the ransomware issue is resolved. Something could be deleted that you later need to eliminate the malware or direct authorities toward the source.
8. Alert all your users
Sending an email announcement and posting warnings on a company message board, to alert users of a ransomware attack is a good strategy but this is not sufficient in the event of a ransomware attack. You’ll need to physically go and speak with everyone directly to ensure that they’re all aware of what has happened and what they need to look out for.
9. Reimage infected endpoints, servers, and virtual machines
Once an environment has been infected, the only way to guarantee that the ransomware has been completely removed is to wipe all devices, including virtual machines clean, and start with a new image. In the meantime, your organization can continue to run if you have a cloud disaster recovery plan in place, allowing critical applications and data in virtual machines to be recovered in a virtual private cloud.
10. Restore from a backup to a clean device
After the damage has been contained, ensure that all users are aware of the current threat so that they will not cause further infection. Data can be recovered, without paying the ransom, by restoring it from a backup stored with a reliable cloud service such as AWS. With an enterprise-grade automated backup solution and knowing when and where the attack took place, you can immediately go back to an uninfected, indexed snapshot of each system’s data.
Related Articles:
How Lepide Can Help
Reducing the risk of a ransomware attack occurring in the first place should be a priority for any organization. Managing your threat surface area and focusing on vulnerability management is crucial to identifying current and future risks and the Lepide Data Security Platform can facilitate this. By identifying users with excessive permissions, open shares, inactive users, and more you can significantly lower the risk of a ransomware attack and keep your systems secure.
The focus at Lepide is to provide visibility over what’s happening with your data. Through visibility, you can speed up the detection of potential ransomware and automate your response.
The Lepide Solution uses threshold alerting, combined with script execution, to detect the symptoms of an attack. Once the threshold is met, Lepide can execute a custom script to shut down a user, computer, or server to prevent the spread of ransomware.
If you’d like to see how the Lepide Data Security Platform can help you prevent ransomware attacks, start your free trial today.

 Group Policy Examples and Settings for Effective Administration
Group Policy Examples and Settings for Effective Administration 15 Most Common Types of Cyber Attack and How to Prevent Them
15 Most Common Types of Cyber Attack and How to Prevent Them Why the AD Account Keeps Getting Locked Out Frequently and How to Resolve It
Why the AD Account Keeps Getting Locked Out Frequently and How to Resolve It