Active Directory (AD) functions as the core identity and access management platform for organizations worldwide. Active Directory infrastructure becomes increasingly complex when businesses progress through organic growth along with mergers, acquisitions, and changing operational needs. Complex AD environments cause difficulties in administering and managing them while producing security weak points with functional inefficiency.
The decision to combine Active Directory forests and domains under one entity or keep them independent represents a critical choice for IT administrators. Every step of security control, administrative workload management, user interface functionality, and operational budget decisions depends on this single choice.
This guide details Active Directory forest and domain understanding while examining domain consolidation merits, outlining benefits, and examining separate implementations with best practice recommendations for successful consolidation.
What are AD Forests?
An Active Directory forest functions as the topmost level within the AD hierarchical structure. Active Directory functions as a self-contained entity with three key components: the schema and configuration, plus the global catalog. The forest schema includes definitions of all directory objects and their possible attributes, and a configuration container maintains service and domain controller placement information.
Each forest serves as a security partition because it operates autonomously from other forests while maintaining sparse trust connections. Forests implement built-in isolation mechanisms that make them appropriate for operating security divisions that need complete unit separation.
Key Components of AD Forests
Multiple essential forest components work together to establish a complete identity management framework within the forest structure. All defined object classes and directory attributes exist within the schema, which serves as the directory’s conceptual design. The physical structure of Active Directory is explained through configuration data, which shows sites alongside domain controllers and services. The Global Catalog displays a partial searchable database containing all objects from the forest to support cross-domain searches.
Separate Active Directory environments can authenticate users through trust relationships that also establish resource sharing capabilities between forests. Forest-wide operational management relies on two specialized job roles that oversee operations across the entire domain. Directory Schema FSMO (Flexible Single Master Operation) controls every schema update within the domain, and the Domain Naming Master handles all domain creation and removal operations within the forest.
Forest Trust Relationships
Forests create trust relationships that let organizations verify users and exchange resources across different organizational domains. The setup of trust relationships between domains gives IT administrators multiple authentication connection types to choose from, i.e., one-way, two-way, transitive, and non-transitive.
With one-way trusts, users from Forest A gain access to Forest B resources without Forest B users being able to access Forest A resources. Users from separate forests can utilize resources in each forest through the implementation of two-way trust connections. Transitive trusts enable authentication to pass between several forest domains, but non-transitive trusts only let authentication extend to directly adjacent domains.
Trust relationships permit essential cross-organizational access despite the increased complexity when organizations must function independently of one another.
What are AD Domains?
An Active Directory domain represents a logical arrangement of networked objects where users, computers, and additional resources connect to one common directory database while sharing security policies and trust relationships. A domain functions as an administrative boundary throughout a forest so organizations can control individual resources through delegation without losing the standard directory organization.
A significant number of organizations use domains to separate their business components across different units, geographic areas, and functional areas. Each domain maintains its own autonomous policies and administration teams for decentralized decision-making without losing connectivity to forest-wide operations.
Domain Components and Structure
Active Directory database replication and domain authentication services operate from servers known as Domain Controllers. Through its Organizational Unit (OU) structure, an organization can divide administrative authority and enforce policies. Group Policy Objects (GPOs) function as organizational blocks of user and computer configuration settings.
Each domain maintains specific FSMO roles that control specialized operational functions. Master roles within AD include the PDC Emulator as password changer and time master, while the RID Master fulfills security identifier allocation functions, and the Infrastructure Master performs domain cross-reference updates.
Domain Trust Relationships
The default configuration of any forest grants trust relationships that are transitive between domains. A trust relationship between domains A and B creates an indirect trust connection to domain C so that domain A automatically trusts domain C. The transitive trust mechanism makes authentication simpler throughout organizations, but organizations must plan their security with great care.
The forest-wide default trust relationships between domains stand out as a fundamental distinction between separate forest domains and domains inside a forest. A trust relationship between domains exists automatically whenever domains belong to a single forest, while administrations must explicitly establish forest trust relationships.
Parent-Child Relationships
A forest consists of domains that construct a domain tree through their parent-child relationships. Child domains within a forest automatically create trust connections that function in both directions to their parent domains. The domain structure provides business unit segregation through its logical organization system, yet maintains forest-wide integration.
A domain structure for an organization begins with its root domain “company.com”, while additional child domains include “europe.company.com” and “asia.company.com”. The design structure protects organizational identity through its regional administration capabilities.
When to Consolidate AD Forests and Domains
The majority of organizations operate multiple AD forests and domains because of historical development rather than following strategic design principles. This fragmented approach develops serious challenges as time passes. The following scenarios demonstrate when AD forest consolidation becomes necessary:
Merger and Acquisition Scenarios
The most frequent reason organizations perform AD consolidation is because of corporate mergers and acquisitions (M&A). Companies that merge normally need to deal with distinct Active Directory infrastructure systems. Continuing with separate forests or domains results in persistent organizational silos while also increasing resource access complexity and administration costs.
M&A consolidation drives value during organizational integration because of organizational requirements. They need shared resource access, unified branding implementation, single IT operations, and higher resource efficiency through streamlined infrastructure.
Cost Reduction Imperatives
Operating multiple Active Directory domains leads to higher infrastructure costs, which multiply in several dimensions. Every additional domain controller adds more requirements to the hardware specifications. And the cost for licensing grows when organizations install more Windows domain controllers across their IT infrastructure.
The complexity of an organization’s environmental structure leads to substantial growth in administrative operational expenses. Security tools implement separate installations requiring instances for each forest, which escalates both the licensing expenses and managerial costs for essential security processes. The addition of operational complexities extends both support difficulties and technical requirements for expertise.
The elimination of redundant infrastructure, together with the reduction of complexity-related operational expenses, generates measurable cost reduction through consolidation efforts.
Simplifying Administration and Security
Specialized knowledge combined with unique tools and processes becomes essential for controlling multiple Active Directory environments. Security monitoring becomes more complex as the attack surface grows larger, which happens when organizations add new forests or domains to their network. Network consolidation helps organizations achieve enhanced policy management through decreased policy number maintenance. As well as this, improved access control, simplification and security monitoring ability through consolidated threat detection systems reduce security policy conflicts from different environments.
Improving User Experience and Productivity
Multiple Active Directory environments always present difficulties for users. The need to remember multiple access credentials leads users toward poor password management practices that ultimately create security weaknesses. Complex cross-domain authentication requirements create workflow interruptions, which diminish work productivity. User productivity suffers when inconsistent application and service access occur because it creates support problems and user confusion.
Users experience difficulty finding organizational resources, which are dispersed across distinct operational domains. Business units that fail to collaborate create challenges that impair effective organizational operations. The unification process removes such obstacles to create better user experiences and productive workflows because it eliminates barriers to corporate resources.
Technical Drivers for Consolidation
Multiple technical elements exist that suggest the need for consolidation. The deterioration of infrastructure creates natural circumstances for business consolidation. The ongoing use of legacy domain functional levels locks users out from using the advanced features provided by AD. When domains possess complex structures, there is a need for extensive synchronization which leads to network congestion from increased replication traffic.
Consistent application of schema elements between various environments must exist to support interoperability. Multiple identity management systems increase both technical difficulty and complexity. The technical requirements create a strong case for consolidation, which should be examined during broader infrastructure development initiatives.
Key Benefits of AD Forests and Domains Consolidation
Consolidating AD infrastructure successfully leads organizations to unlock various substantial benefits that span multiple operational areas. Both immediate and prolonged post-investment benefits result from AD Forests and Domains’ consolidation efforts.
Enhanced Security Posture
Security benefits from AD consolidation because it enables single-policy security with clear identity and access monitoring and better audit ability, and specialized expert focus while eliminating redundant security points.
Organizations that consolidate their Active Directory environments build stronger security through management simplification by enabling security teams to monitor and control the entire infrastructure with consistent policies.
Administrative Efficiency
The centralization of management under consolidation reduces overhead costs by bringing administration under one centralized system, which eliminates duplicated work and streamlines troubleshooting procedures while standardizing processes alongside administrator expertise across a single environment.
The efficiency improvements from consolidation result in cost reductions alongside enhanced service delivery because IT teams can serve business demands faster and pursue key initiatives instead of handling repetitive maintenance tasks across various environments.
Cost Savings Analysis
After consolidation, organizations typically achieve multiple types of cost savings. IADC reduces setup costs by using fewer domain controllers while decreasing hardware requirements. The reduction of Windows Server and CAL requirements occurs through licensing optimization. Reductions in administrative time become possible through simplified maintenance processes and reduced operational requirements.
When organizations choose a single environment for their IT staff to use, knowledge requirements become simpler compared to mastering multiple system configurations. Security tool consolidation eliminates duplicate solutions because of its streamlined approach. Research shows organizations can decrease operational expenses linked to AD by 20-40% through proper consolidation programs, but additional cost savings stem from productivity growth along with lower security incidents.
Streamlined User Experience
A united AD infrastructure produces major advancements in user experience. Single sign-on technology allows users to access all corporate resources using a single username and password combination. Organizations guarantee equal application and service access because of consistent user access. Simplified collaboration allows the organization to enable better access, sharing, and permission management throughout all departments.
The elimination of friction simplifies complex access challenges between different domains. New user onboarding becomes more efficient because it ensures swift resource access provisioning. Organizations experience measurable productivity growth and reduced help desk support activities linked to access issues because their users experience less complexity in their daily authentication processes.
Technical Advantages
The technical benefits of consolidation bring multiple beneficial outcomes to organizations. The simplification of replication paths enables better network bandwidth utilization along with decreased data movement delays. A consistent schema structure guarantees that custom attributes and object classes become accessible to all users. Centralized configuration management becomes possible through Group Policy‘s unified framework.
Strategic site arrangement improves the delivery speed of location-based service models. The simplified disaster recovery system allows an easier backup process, together with easier restoration procedures. The technical advantages enhance system operational performance while increasing reliability and simplifying the scope of continuing maintenance and troubleshooting activities.
When to Maintain Separate AD Forests and Domains
The benefits of AD consolidation do not apply tospecific valid cases where different AD environments must remain distinct. Organizations must review all these elements thoroughly before starting any consolidation initiatives.
Regulatory and Compliance Requirements
Several regulatory frameworks explicitly demand system separation or impose this requirement through implied provisions. The government may demand that organizations keep different data compartments separate through different classification levels. Certain government regulations in financial services and healthcare, together with other industrial sectors, establish strong mandatory isolation standards for data.
Specific geographic laws demand that some data stay confined to specific boundary areas. Strict system and data separation become necessary when contractual requirements exist between clients and partners. The security boundary capabilities of forest separation enable organizations to meet these stringent legal and regulatory requirements.
Operational Autonomy Requirements
Certain organizational structures need to operate via different AD infrastructure environments. Synchronized file and container structures become necessary for business units that need operational autonomy or minimal supervision from central management. Different parts of the organization that employ multiple IT governance models face challenges during consolidation efforts.
Certain units need exclusive administrative environments because their specialized requirements cannot be served within a unified system. The implementation of different operational timelines produces conflicts within environments that integrate multiple organizations. Operating independently requires careful weighing against potential organizational benefits, but officials should assess the process impacts of both isolated operation and consolidated structures.
Technical Compatibility Challenges
Technical considerations sometimes necessitate separation. The combination of different application schema requirements that cannot be merged creates obstacles to consolidation efforts. Some legacy application dependencies need exclusive domain configurations that cannot exist within a consolidated system structure.
Certain specialized security profiles for workload require independent configuration settings, which might contradict organizational standards. Multiple conflicting lifecycle management needs can create complexities during consolidation processes. A complete assessment of these technical obstacles needs to take place because numerous barriers can be resolved by suitable planning with technology-based remedies.
Security Isolation Necessities
Security protocols that require forest separation produce genuine advantages. When threat levels escalate against high-value targets, security professionals should isolate these assets. The administrative systems that run privileged access workstations must stay separated from other user workstation domains. Many network domains requiring development/test/production segregation need robust partitioning protocols.
Security benefits from isolated environments when partners or vendors need access. Separation techniques can provide better security benefits that demonstrably surpass consolidation advantages during focused high-risk situations with unique security requirements.
Risk Assessment Framework
The choice between consolidation and separation depends on four key elements that organizations need to evaluate before making decisions. Organizations should evaluate separation potential through threat model examinations for targeted risks while also performing administrative impact assessments to measure operational expenses. The evaluation should include business functionality tests to assess process disruptions and compliance requirement verifications to validate regulatory standards before completing cost-benefit assessments.
Best Practices for AD Forest and Domain Consolidation
A successful consolidation scheme needs strategic planning together with proper execution. A proper set of best practices will lead to successful execution by delivering your anticipated project benefits while minimizing disruption and risk.
Assessment and Planning Phase
An extensive assessment phase alongside planning processes creates the necessary foundations for consolidation to succeed. Start by documenting every domain, trust, application, and dependency in your present environment throughout an inventory process. Technical obstacles emerge when you detect issues between the schema and security models and the application’s needs.
Business organizations should evaluate impacts through assessments of different business units’ responses to consolidation efforts. The development of a migration strategy demands implementation through phases to prevent disruptions. Select success criteria that serve as standard measurements to evaluate the effectiveness of consolidation initiatives. Organizations need 3-6 months for initial preparation when working with complex systems, although this investment results in improved execution quality.
Technical Preparation
Several technical setups are essential before performing the actual consolidation process. The first step includes removing outdated objects and fixing any inconsistencies that exist in the present directories. Consolidation efforts benefit from standardized naming conventions, which receive policy-based unification in the target environment.
Schema extensions need alignment through the integration of modifications that occur between different environments. The forest functional level should receive preparation to enable domains to run at their target operational level. The deployment of necessary utilities alongside forest functional level testing of environments establishes migration tools. The preparations provide organizations with essential groundwork for migration while reducing potential technical problems during implementation
Migration Execution Strategy
Four main execution strategies guide the migration process. You can choose between New Forest Migration, which builds a new forest and moves objects through it, or Forest Restructuring, which consolidates objects into existing forests. As well as this is Domain Consolidation, which minimizes domain numbers within existing forest structures, or Intra-Forest Reorganization, which transfers objects between domains in a single forest.
The selected execution strategy provides unique benefits based on how the system currently operates and where your organization needs to go. Your decision should match the unique requirements of your situation, along with careful examination of application dependencies and user impact, and resource demands.
User and Resource Transition Management
Devoting energy to careful planning of the user experience before moving becomes essential for migration initiatives. The complete communication plan informs end-users about system changes, along with the requirements. The foundation of credential management planning comprises methods used to synchronize or reset passwords across different systems.
Access continuity planning protects critical resources from being disrupted. Organizational training prepares technical support personnel to handle typical migration challenges. Rollback procedures create frameworks to deal with failed migrations. The preparations focused on users creating a smooth transition pathway that reduces operational disruption throughout consolidation.
Post-Consolidation Optimization
Multiple optimization steps need to be implemented after completing technical consolidation work. Security review conducts vulnerability scanning to identify potential weaknesses within the new environment. Performance tuning applies optimization techniques to replication systems along with site topologies, as well as domain controller deployment locations.
Updates to documentation result in creating detailed records for the entire new system environment. The administrative model receives fine adjustments to refine delegation and permission strategies. The consolidated environment receives extensive monitoring through implementation and deployment. The post-implementation activities confirm the consolidated environment achieves the desired benefits while functioning securely and with high efficiency.
How Lepide can help in AD security
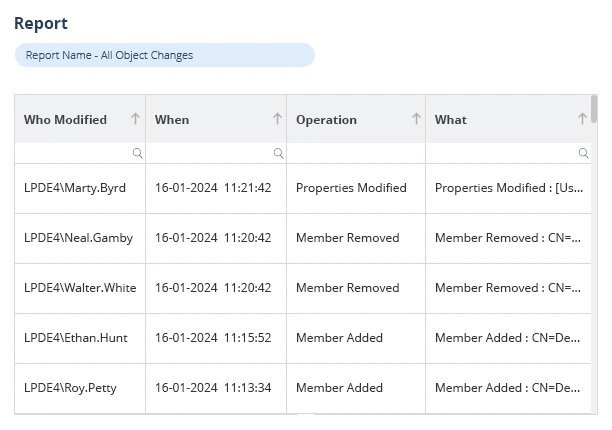
Lepide Active Directory Auditor gives organizations complete real-time monitoring and detailed audit trails for all modifications inside AD. It tracks vital “who, “ “what, “ “when, “ and “where“ information about every event, which includes changes to user accounts as well as group membership updates, policy modification, and permission adjustments. The tool’s high visibility capability enables organizations to discover unauthorized access while simultaneously investigating account lockouts and controlling logon activities for quick threat detection and operational issue mitigation.
Users can generate over 80 detailed audit reports about failed logon attempts, account lockouts, permission modifications, and inactive users through the platform’s flexible reporting system. Through before-and-after value tracking and instant alert, Lepide enables automated workflows and allows users to undo unwanted changes while maintaining HIPAA, PCI, SOX GDPR compliance and improving operational effectiveness.
Conclusion
Organizations should view Active Directory consolidation as a strategic move that delivers security improvements, along with cost reduction and operational efficiency benefits. The advantages of consolidating directory services surpass potential hurdles that modern enterprises encounter.
Organizations should continue to reassess their AD structure because their digital transformation, alongside acquisitions and changing business models, requires this routine evaluation process. AD architecture requires organizations to view it as an adaptable framework that evolves alongside changing business requirements while upholding robust security measures.
In case you want to know more, start your free trail or book a demo with one of our engineers today!