Take the complexity out of compliance management.
Achieve compliance 700x faster with detailed audit reports, permissions remediation, and AI-backed threat detection and response.














Most companies struggle to meet compliance standards due to a lack of visibility over user directories and files/folders. This is where Lepide starts.
Tamper proof audit trails for all events and changes across users, permissions, groups, files, folders and more. Pre-built audit reports mapped to compliance frameworks (GDPR, HIPAA, SOX, PCI DSS, etc.).
Uncover excessive permissions, inactive users, stale data, and more. Implement least privilege by automating permissions remediation and monitoring for abnormal user behavior and permission changes.
Lepide gives you real time alerts and automated threat models / workflows for any compliance-related events, including privilege escalation, suspicious file activity, unauthorized access, and more.
Many compliance standards are intensely rigorous and require in-depth visibility over your regulated data and user activity. Lepide’s simplified approach will have you aligned in no time.
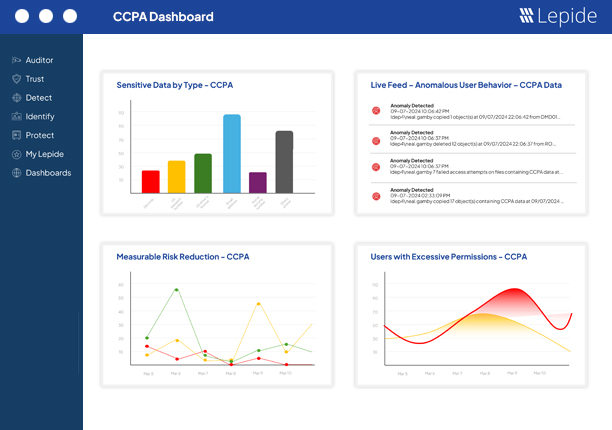
Pre-defined audit reports mapped to known frameworks take the guesswork out of compliance management. Real time, customised visibility and user-friendly dashboards give you control over your data and identities.
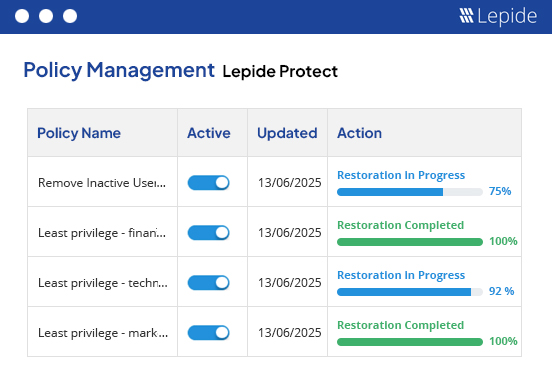
Lepide makes it easy for you to understand who needs access and when permissions become excessive. Apply custom remediation policies to automate least privilege and keep your threat surface small.
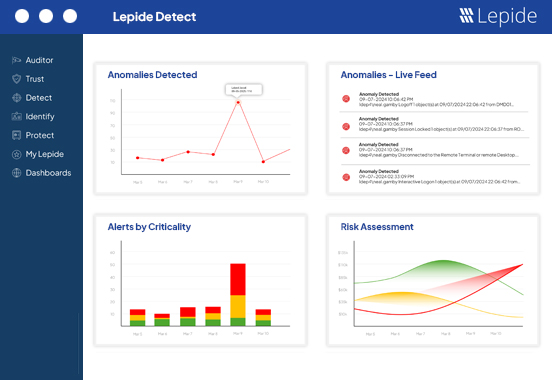
Lepide uses AI-backed anomaly spotting and user behavior analytics to spot any threats to your data and identities. Once threats are detected in real time, Lepide can automate the response to keep you secure.
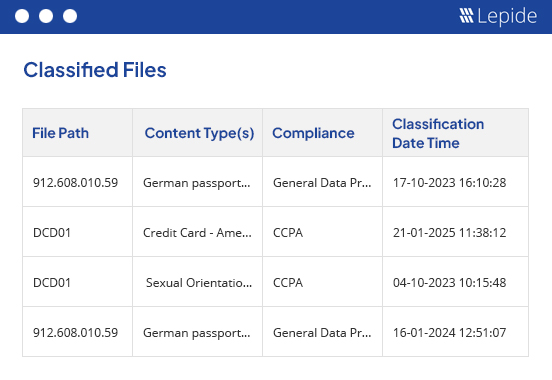
Ongoing data discovery and classification at the point of creation helps you map your sensitive data to compliance frameworks like NIST, HIPAA, SOX, PCI DSS, GDPR, ISO and more.
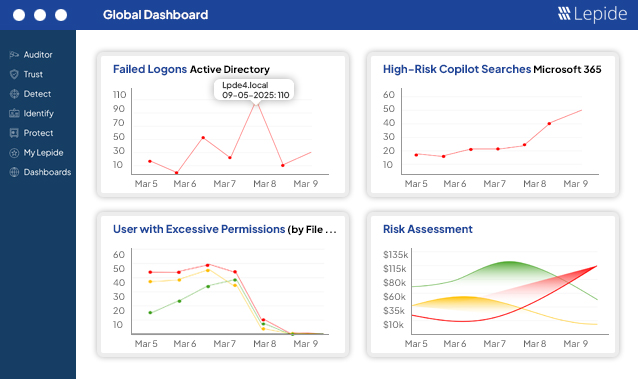
Need to get a quick overview of your compliance posture to share internally or with auditors? Our dedicated compliance dashboards make this possible with real time, customisable awareness.
From CISOs to SecOps teams, find out how the NIST Cybersecurity Framework is evolving and what you should be doing to achieve and maintain a compliant cybersecurity posture.
Get the free guide now!