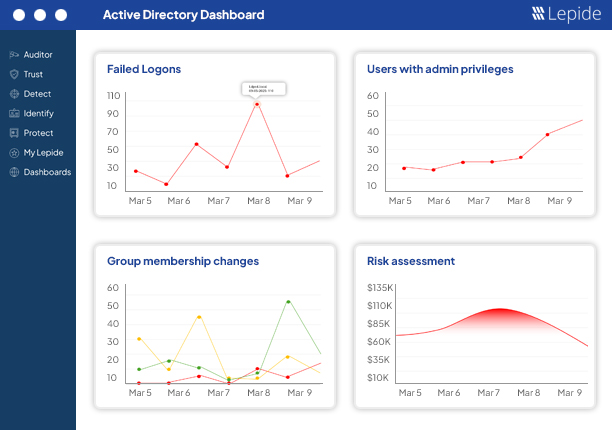
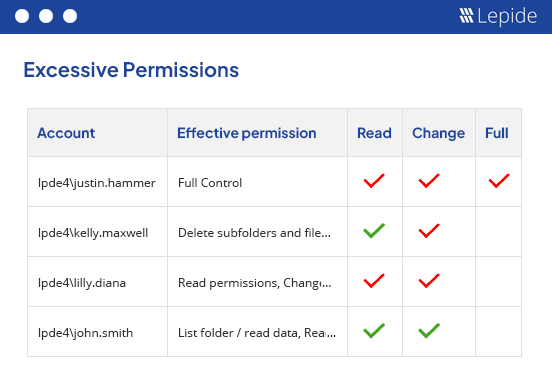
CJIS Compliance Audit Solution
Prepare your organization for a Criminal justice Information Services (CJIS) audit with Lepide. Lepide Data Security Platform is a complete CJIS compliance audit solution, providing numerous pre-defined audit reports to help your organization avoid non-compliance fines.