Lepide Auditor for Active Directory provides a scalable means of auditing changes made to configurations and permissions. Get the security intelligence you need to properly protect Active Directory, including the “who, what, where, and when” of all changes made. Bolster security, speed up investigations, mitigate the risks of privilege abuse and meet compliance requirements.
Take a virtual tour of our auditing software in web-based demo and see how it helps you to reduce your threat surface area, detect insider threats and compromised user accounts, and simplify IT operations and management tasks.
Launch in-browser demo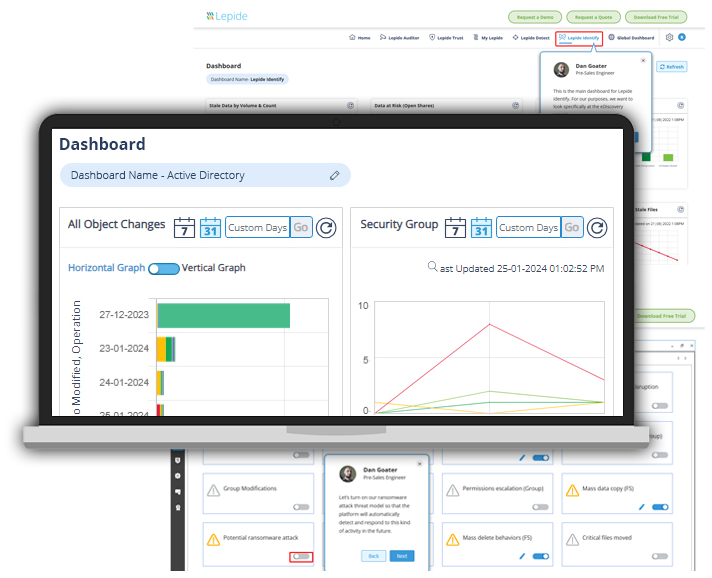
Lepide auditing tool helps identify security risks within your Active Directory by providing reports on admin users, inactive users, non-compliant passwords, and misconfigurations, enhancing visibility and demonstrating a commitment to reducing overall security threats.
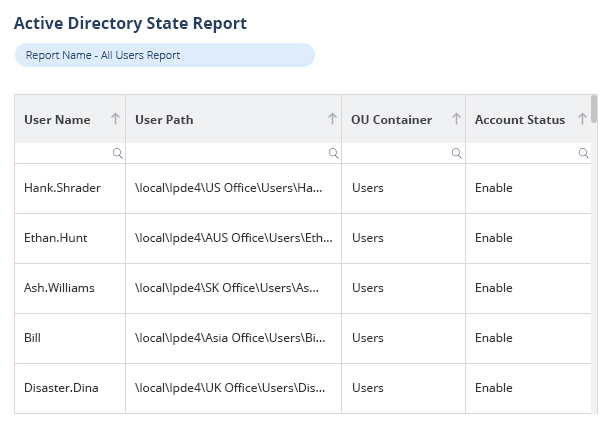
Explore numerous pre-defined Active Directory audit reports to quickly identify critical security risks, including changes to infrastructure, users, and groups, with real-time threat detection, alerts, and automated responses.
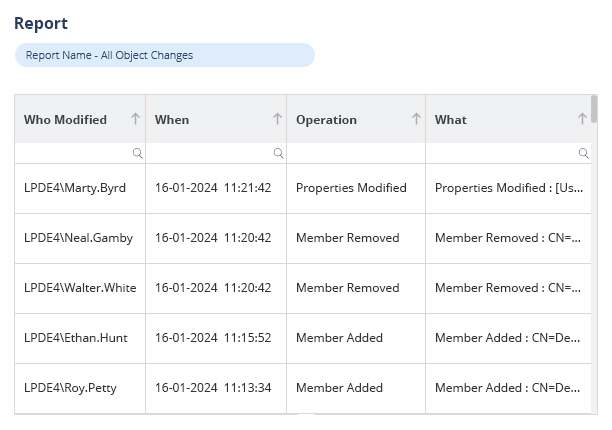
Lepide provides comprehensive auditing and reporting of user activities and changes within your Windows AD/Entra ID environment with detailed audit logs, helping organizations maintain security, detect potential threats, and demonstrate compliance with regulatory requirements.
The restore and rollback features of our tool allow you to quickly reverse erroneous changes or deletions, restoring all aspects such as group memberships, attributes, and permissions with a single click in your Active Directory.
Auditing Active Directory is an essential element of your data security strategy. It holds the keys to your kingdom, and is often the focal point of attacks. Effective Active Directory auditing enables you to detect unauthorized access, track changes that could compromise security and implement more efficient incident response. AD auditing is also essential for meeting legal compliance requirements, providing detailed audit trails that can be used for internal and external audits. It also helps with operational efficiency, allowing you to audit changes that might affect business operations, monitor user behavior to optimize resource allocation and enforce policies.
There are numerous best practices for effective Active Directory auditing, specifically related to critical activities, including logins, changes to user accounts, group memberships and permissions. AD audit logs should be regularly reviewed to identify and respond to suspicious activities in a timely manner. AD auditing should also be focused on the events that matter the most so that the system is not overwhelmed with noisy data. You should use a third-party AD audit tool that can automate much of the real time alerting and event log analysis. Ensure your event logs are stored securely and retained according to whichever compliance requirements you might be subject to. Detailed internal audits should also be regularly undertaken to ensure policies and practices are still effective.
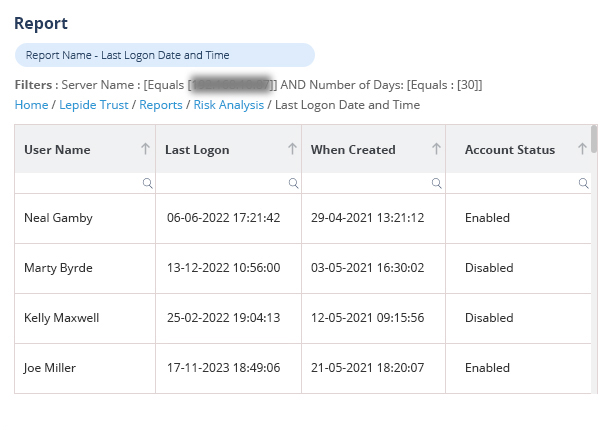
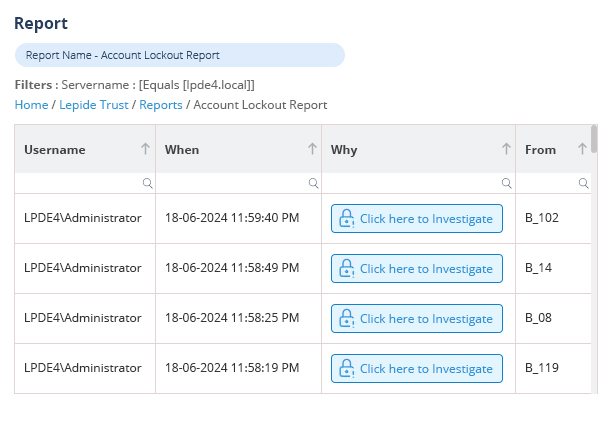
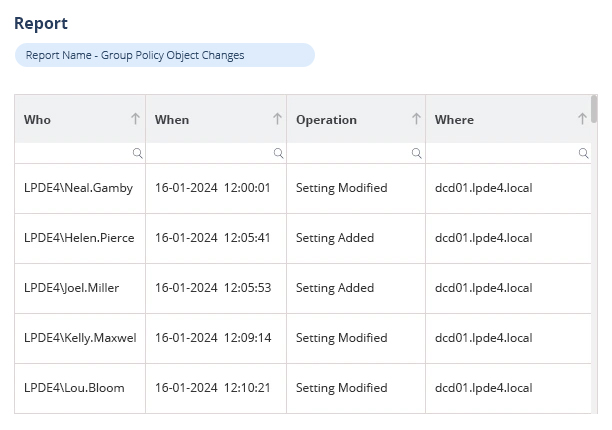
It’s important to focus on events that are critical to the security of your Active Directory, including the creation, deletion, and modification of user accounts and group memberships. Monitoring logon activities can help to detect unauthorized access. Auditing changes to permissions and access rights can help to prevent privilege abuse or permissions sprawl. Auditing changes to AD schema can help you maintain the integrity of your AD. Additionally, it’s important to audit access to critical systems and sensitive data, as well as changes to group policy objects (GPOs) that could affect your security settings.
Companies should look for AD auditing tools that offer comprehensive and real-time monitoring capabilities, allowing them to track changes to user accounts, group memberships, permissions, and policies. The tool should provide detailed and easily searchable logs, customizable alerting mechanisms for critical events, and robust reporting features to meet compliance requirements. It should also offer integration with other security systems and support for long-term log retention with secure storage. User-friendly dashboards and automated analysis features can help in quickly identifying suspicious activities and potential security threats. Additionally, scalability and support for various environments (on-premises, cloud, or hybrid) are crucial to ensure the tool fits the company's current and future needs.
Lepide prevents Active Directory compromise from tools like Mimikatz DCSync by providing advanced threat detection and response capabilities that monitor for unusual activities indicative of such attacks. Specifically, Lepide tracks and alerts on suspicious replication requests and unauthorized access to domain controllers, which are common behaviors associated with DCSync attacks. It leverages machine learning and behavioral analytics to identify anomalies in user and system activities, thereby enabling early detection of potential compromises. Additionally, Lepide ensures that security policies and access controls are properly enforced and provides detailed audit logs and real-time alerts to administrators, allowing for rapid investigation and mitigation of threats before they can cause significant harm.

We use Lepide for the security of our Entra ID and On-prem Active Directory, its real-time alert system is awesome!

Lepide is straightforward to use and effective right off the bat. Plus, the level of patience, attentiveness and technical knowhow is far beyond most support and sales teams I’ve seen before.

Lepide gave as almost instant insight into changes into our AD environment. For auditing Group Policy, its reports were hands down the most intuitive at the time
Lepide is a perfect fit for the security and compliance of our Active Directory. It helps us cut out a lot of wasted time and money and now we know we can be compliant with industry standards.
