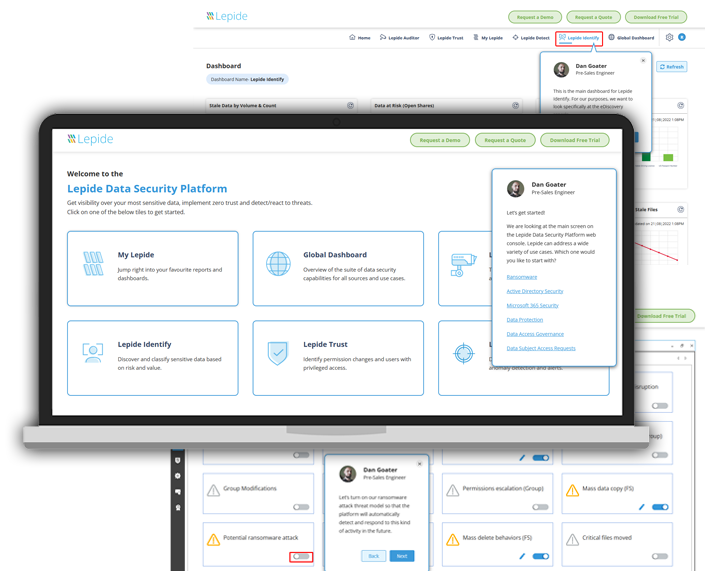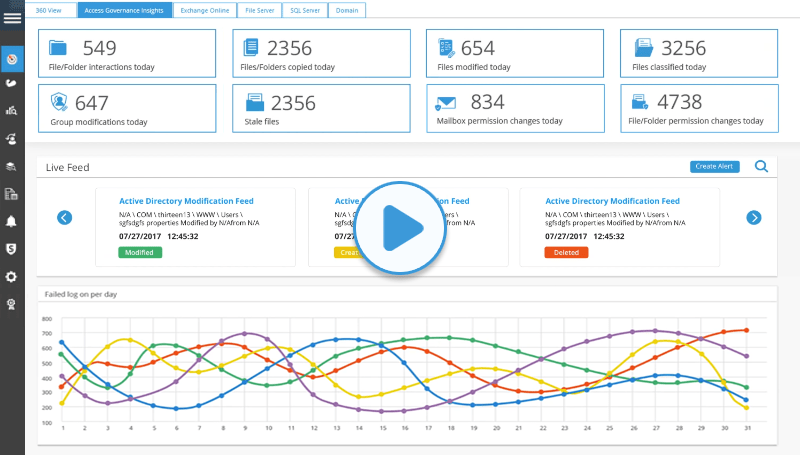
Lepide uses data-centric audit and protection functionality to discover GDPR data, see who has access to it, analyze user behavior and ensure the surrounding environment is secure. With hundreds of pre-set reports related to GDPR specific requirements, you’ll be able to quickly and easily meet those GDPR audits and avoid potentially crippling fines.

Discover, classify, tag and score data based on whether it is applicable under GDPR compliance.

Ensure that the only users able to access GDPR data are those that require access for their job.

Numerous pre-defined reports tailored to meet some of the more stringent auditing aspects of GDPR compliance.
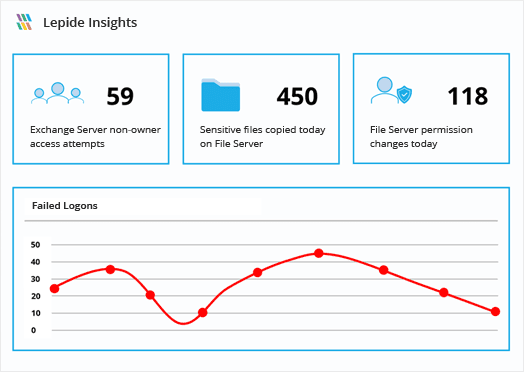
Satisfy GDPR Audit Requirements Lepide will allow you to identify and protect the sensitive data of EU citizens. Ensure you are able to quickly detect and react to potential data security threats through pre-defined reports, real time alerts, anomaly spotting and powerful permissions and change auditing.
Monitor User Behavior With GDPR Data Track and monitor what your users are doing with data that falls under GDPR requirements. Spot anomalies in user behavior and automate your response your unwanted or unauthorized changes.
Article 5
Ensure that all personal data is processed in a way that protects the data against unauthorized access, unlawful processing and accidental deletion through in-depth permissions reporting and access monitoring.
Article 24
Prove that you are processing data as per GDPR requirements by being able to generate pre-defined reports of all interactions with personal data stored in files, folders and mailboxes in your critical IT environment.
Article 25
Analyze user and entity behavior, spot anomalies, track file and folder modifications and spot permission changes to help implement data-protection principles, such as a policy of least privilege.
Article 30
Discover and classify your sensitive data, determine who has access to it and set up detailed auditing so that you have a record of exactly what is happening to the data. Get alerts on suspicious activity/behavior.
Article 33
Use Lepide to detect breaches involving personal data. Generate pre-defined reports and real time alerts that will enable you to react quickly and take the correct information to the supervisory authority.
Article 35
Take a data risk assessment with Lepide to understand where your areas of data security weakness are and get actionable advice on how to strengthen them. Instantly see where GDPR breaches are likely to originate.
Take a virtual tour of the Lepide Data Security Platform in our web-based demo. See how Lepide aligns with your use case, whether it be ransomware, Active Directory security, Microsoft 365 security, data protection, data access governance or more.
Launch in-browser demo