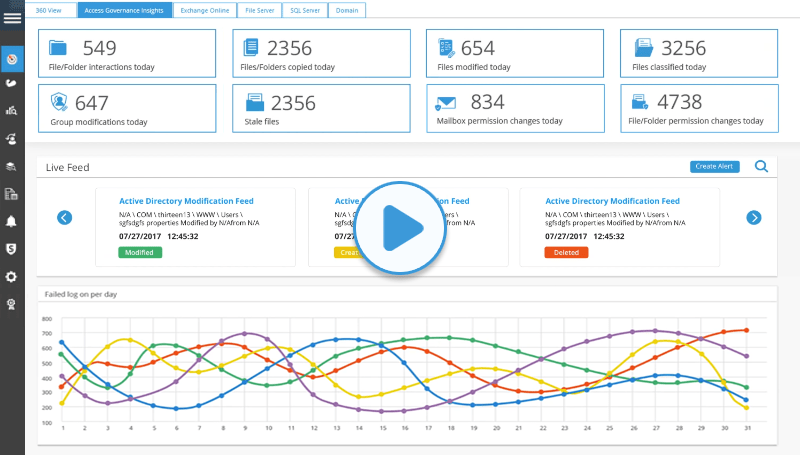
Whilst we can address challenges in almost every vertical, there are a few specific industries we tend to do very well in. Lepide Data Security Platform is an integral part of the IT environment in hundreds of organizations across the below verticals. We’re 100% sure we can meet the specific needs of your organization.
Take a virtual tour of the Lepide Data Security Platform in our web-based demo. See how Lepide aligns with your use case, whether it be ransomware, Active Directory security, Microsoft 365 security, data protection, data access governance or more.
Launch in-browser demo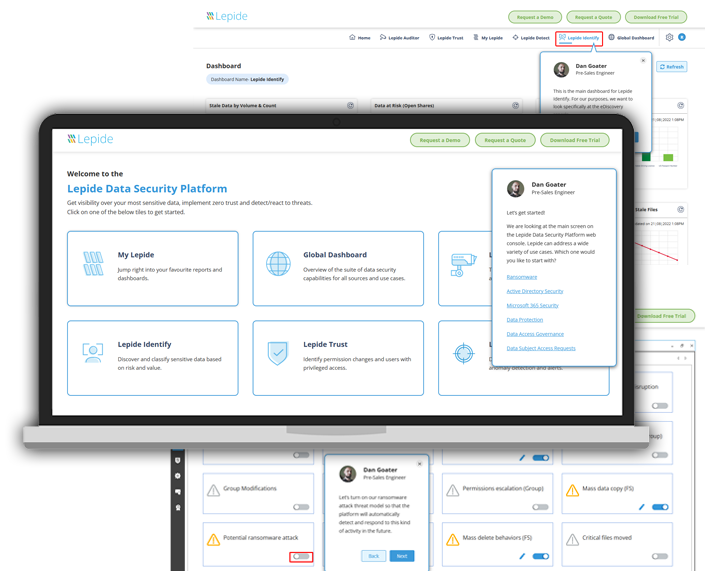
Lepide is straightforward to use and effective right off the bat. Plus, the level of patience, attentiveness and technical knowhow is far beyond most support and sales teams I’ve seen before.

We chose Lepide as they were able to offer us threat detection and response, and a way of separating out reporting duties to a web console – all from one platform.

Lepide is a perfect fit for our IT Security and Compliance requirements. It helps us cut out a lot of wasted time and money and now we know we can be compliant with industry standards.
