
Implement hundreds of pre-defined criteria sets to locate sensitive data across your unstructured data stores and map to compliance mandates.
Other solutions may take days to scan your environment for sensitive data. With Lepide, you can identify sensitive data at the point of creation for instant value.

Identify what content users have access to and what they are doing with your data to better inform access controls and security policies.
Once your most sensitive data has been identified and classified, you can use Lepide to detect threats to it and automate response.by deploying any of our pre-defined threat models.
Proximity scanning eliminates false positives better than any other platform on the market. By giving the discovered pattern more context, we can accurately predict what is real sensitive data and what is a false positive.
By enabling you to see which of your users have access to your most sensitive data, Lepide can help you spot users with excessive permissions, apply appropriate access controls, and even govern access from within the solution.
Having visibility over your most sensitive data enables you to determine when your users are putting you at risk. Get alerts and reports on user behavior as it relates to your most sensitive, regulated data.
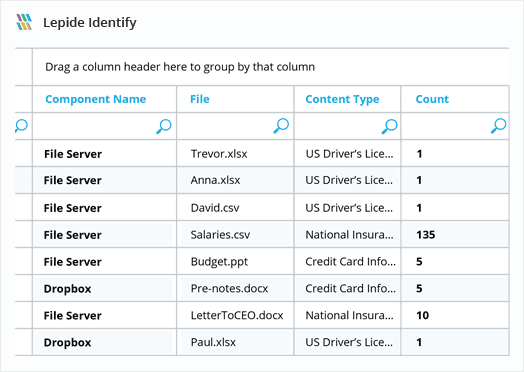
Our Data classification software contains a huge library of pre-defined data sets for all common types of sensitive data and compliance standards (including HIPAA, SOX, PCI, GDPR, CCPA and more). Simplify your compliance reporting with Lepide.
If a GDPR file is copied, you need to know. If a large number of health records are accessed or deleted, you need to know.
With the Lepide Data Classification tool, you will know.

Take a virtual tour of the Lepide Data Security Platform in our web-based demo. See how Lepide aligns with your use case, whether it be ransomware, Active Directory security, Microsoft 365 security, data protection, data access governance or more.
Launch in-browser demo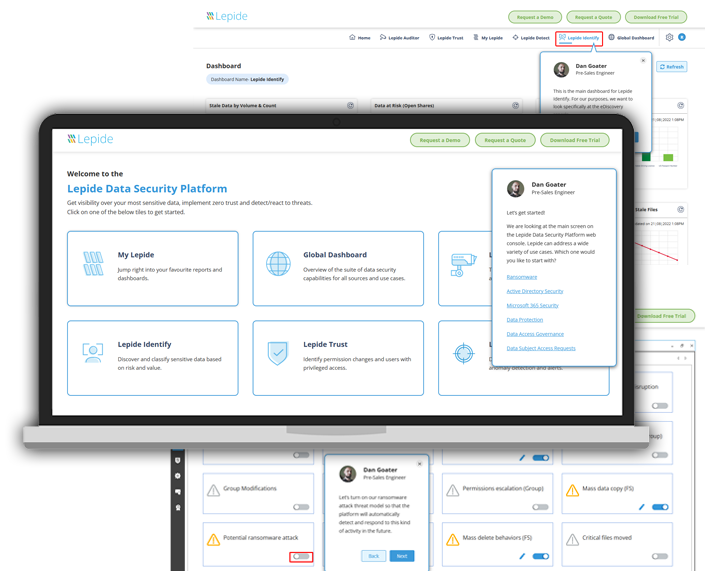
Incremental Scanning After an initial discovery and classification scan, data can be classified at the point of creation/modification incrementally to give you a scalable solution that works quickly and efficiently.
Wide Range of File Types You can scan a wide range of different file types, including word documents, text documents and excel spreadsheets, to find out where your sensitive data resides.
Prioritize Data Based on Risk Categorize and score data based on the risk value of the content so that you can focus your user behavior analytics and permissions strategies on the data that matters most.

We use Lepide for the security of our Azure and On-prem environment, its real time alert system is awesome!

There are many variables that will determine the length of time it would take to successfully complete a scan, including the size of the dataset, the size of the file, the file types and the number of patterns/rules you have configured the solution to search the data for. We benchmark against industry standards and speeds when it comes to data discovery and classification.
We recommend running a full, deep scan across your data on a periodic basis (monthly or quarterly) and enable classification on-the-fly in the interim. Every time a new file is created/modified, Lepide will scan the files in real time to identify if there has been any newly created sensitive data