
Business Email Compromise (BEC), formally known as the “man-in-the-email” scam, is a type of cyber-attack whereby the attackers use fraudulent emails to trick unsuspecting victims into transferring money to their bank account. In some cases, the attacker may seek to obtain sensitive data instead, which they can use for other criminal activities.
The average daily volume of BEC emails in 2019 was significantly higher that it was in 2018 – a 50% increase to be precise. On average, 6,029 organizations were targeted by BEC emails per month between July 2018 and June 2019, which equates to an average of 5 emails per month, per organization. The United States is the most targeted region, accounting 39% of all reported BEC attacks. This is followed by the UK (26%) and Australia (11%).
Anyone could potentially fall victim to a BEC scam, including businesses, non-profit organizations and Government agencies; however, attackers will typically target organizations who conduct wire transfers to overseas suppliers. Attackers will often carry out careful research in order to learn about their targets – a technique referred to as “spear phishing”. They typically look for email accounts that belong to senior executives, or anyone who might be involved in making wire transfer payments.
In some cases, attackers will try to infect the user with malware in an attempt to gain access to the network, with the intention of stealing financial data or PII. Such malware might include Keyloggers or Spyware, which can be used to steal a user’s credentials.
Alternatively, they might use a Trojan to create a backdoor, which they can use to monitor a user’s activity from a distance. Given how profitable BEC can be, attackers will often work as a part of a cyber-crime syndicate, which will include a number of specialized personnel, ranging from hackers to lawyers, linguists and social engineers.
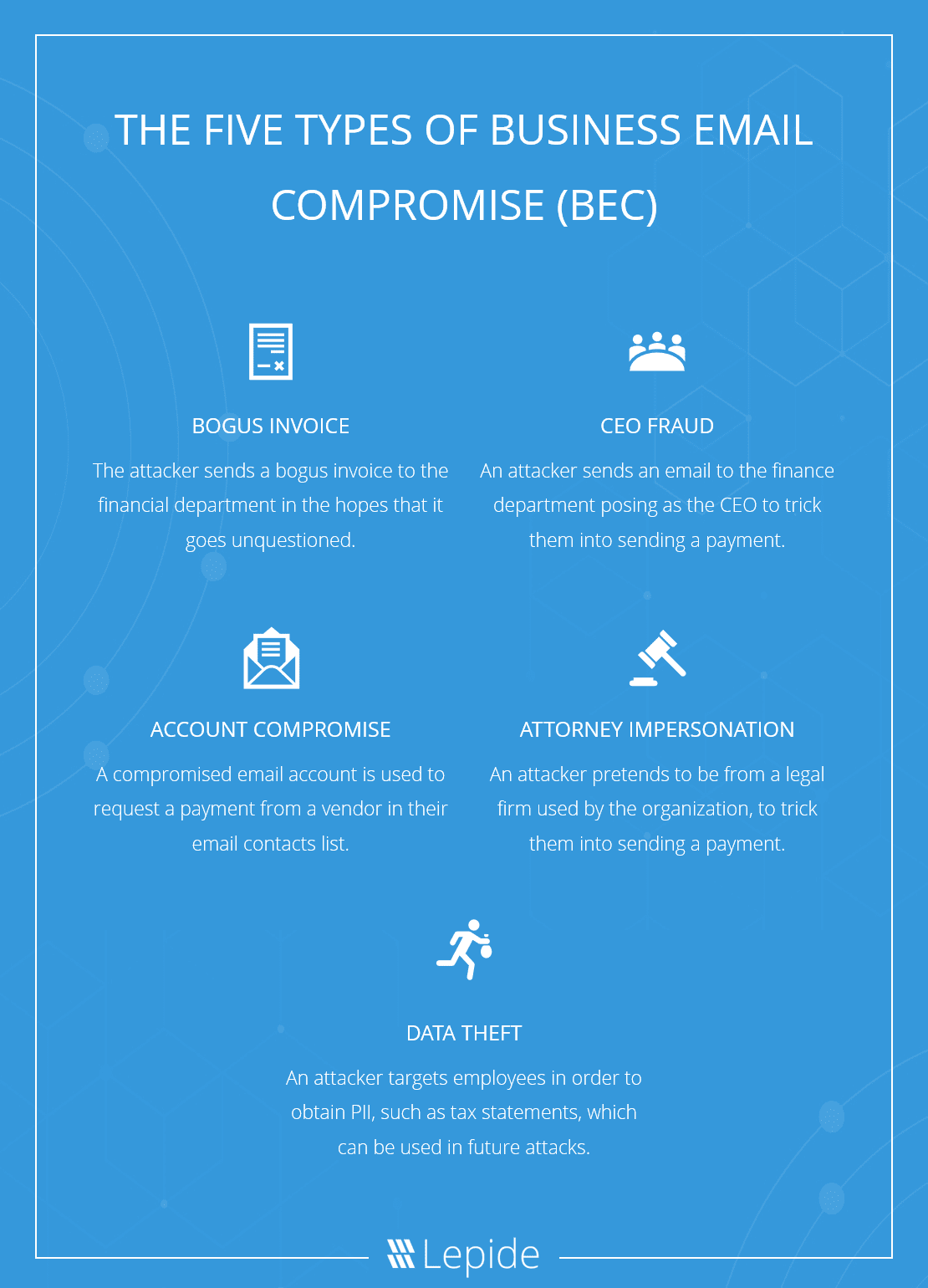 The Five Types of Business Email Compromise (BEC)
The Five Types of Business Email Compromise (BEC)
According to the FBI, there are 5 types of BEC scams, which include The Bogus Invoice Scheme, CEO Fraud, Account Compromise, Attorney Impersonation and Data Theft.
- The Bogus Invoice Scheme is where the attacker sends a bogus invoice to the finance department.
- CEO Fraud is where the attacker sends an email to the finance department posing as a CEO in order to trick them into sending a payment.
- Account Compromise is where a compromised email account is used to request a payment from a vendor in their email contacts list.
- Attorney Impersonation is where the attacker pretends to be from a legal firm used by the organization, in order to trick them into making a payment.
- Data Theft is where the attacker targets employees in order to obtain PII, such as tax statements, which they can use in future attacks.
BEC scams often rely on “cousin” or “look-alike” domains, which, as you might expect, are designed to look like legitimate domains, which may include an additional suffix, or a few characters spelt differently. For example, an attacker might use info@bankname.com, instead of info@banknameinfo.com. However, the majority of emails come from free email service providers such as Gmail, Hotmail, AOL and Yahoo!
Email subject lines will commonly include words like IMPORTANT, YOUR RECEIPT FROM APPLE, CONFIDENTIAL, NOTIFICATION OF PAYMENT RECEIVED, and URGENT.
The Largest BEC Incidents to Date
Google and Facebook
Yes. Both Google and Facebook fell victim to a BEC scam which lead to the transfer of $123 million to an account held by a Lithuanian man. The man sent fake invoices and posed as a representative for a company that provided hardware for their data centers.
Xoom Corporation
In December 2014, Xoom, a money transfer company based in the United States, transferred $30.8 million to fraudulent overseas accounts, sending their shares plummeting by as much as 17%. The attacker impersonated an employee and sent payment requests to the finance department.
Scoular
Scoular, a company that deals with the trade and transportation of grains, oilseeds and other agricultural produce, fell victim to a BEC attack in June 2014, resulting in the loss of approximately $17 million. The fraudsters used “extremely well-targeted emails”, supposedly from the CEO, to trick the finance department into transferring the funds to a bank account in China. The emails were convincing because the organization was planning to expand their operations to China.
Ubiquiti Networks
Ubiquiti Networks fell victim to a BEC scam, which was identified on June 5, 2015. The attacker, who was posing as an employee, sent a payment request to the finance department, which lead to the transfer of $39.1 million to an overseas bank account.
FACC
Fischer Advanced Composite Components AG (FACC), a manufacturer of aircraft components and systems based in Austria, fell victim to a BEC scam costing them approximately $47 million. The attack occurred in January 2015 and involved a spear-phishing email impersonating the CEO, requesting a payment in relation to one of the company’s acquisition projects.
Mattel
Mattel, an American toy manufacturing company, was tricked into sending $3 million to a bank account in China. The email containing the fraudulent payment request was sent to Mattel’s finance department, on April 30, 2015.
Other organizations that have fallen victim to costly BEC attacks include Dublin Zoo, Te Wananga o Aotearoa, The New Zealand Fire Service, Save the Children, and Evaldas Rimasauskas.
The Future Of BEC
BEC scams are becoming increasingly more sophisticated and targeted, with every year that passes. For example, cyber-criminals are starting to experiment with Artificial Intelligence (AI) and Machine Learning (ML) to execute advanced social engineering attacks.
Using AI and ML, hackers are able to impersonate C-Level executives by extracting audio snippets and/or video footage of the executive, perhaps from YouTube or some other source, and then use these snippets to generate audio-visual content that can be sent to the finance department, authorizing a transfer of money to the attackers.
Audio-visual content generated in this way are referred to as “deepfakes”. Deepfake technologies are very new, and so it will be some time until we see this technology becoming widely adopted by cyber-criminals. However, AI is already being used for automated phishing campaigns, and to develop more sophisticated forms of malware.
If you would like to add an extra layer of security to your Exchange Server, schedule a demo with one of our engineers today to learn about how the Lepide Data Security Platform can help you.
 Important Group Policy Settings & Best Practices to Prevent Security Breaches
Important Group Policy Settings & Best Practices to Prevent Security Breaches 15 Most Common Cyber Attack Types and How to Prevent Them
15 Most Common Cyber Attack Types and How to Prevent Them Why Active Directory Account Getting Locked Out Frequently – Causes
Why Active Directory Account Getting Locked Out Frequently – Causes
