
In the intricate landscape of cybersecurity, Event ID 4769 holds a significant place, particularly in environments where Kerberos authentication protocol is employed. A Kerberos service ticket request, denoted by this event ID, represents a pivotal moment in the authentication process within Windows environments. It signifies the initiation of a complex series of cryptographic exchanges aimed at validating a user’s identity and granting access to network resources securely.
Understanding Event ID 4769 is crucial for system administrators, security analysts, and IT professionals tasked with monitoring and safeguarding network infrastructures. This event provides valuable insights into user authentication activities, aiding in the detection of suspicious behavior, unauthorized access attempts, and potential security breaches.
In this article, we delve into the intricacies of Event ID 4769, exploring its significance, the underlying Kerberos authentication mechanism, and its implications for network security. By unraveling the nuances of this event ID, we aim to equip readers with the knowledge and tools necessary to effectively interpret and respond to authentication-related events in their IT environments.
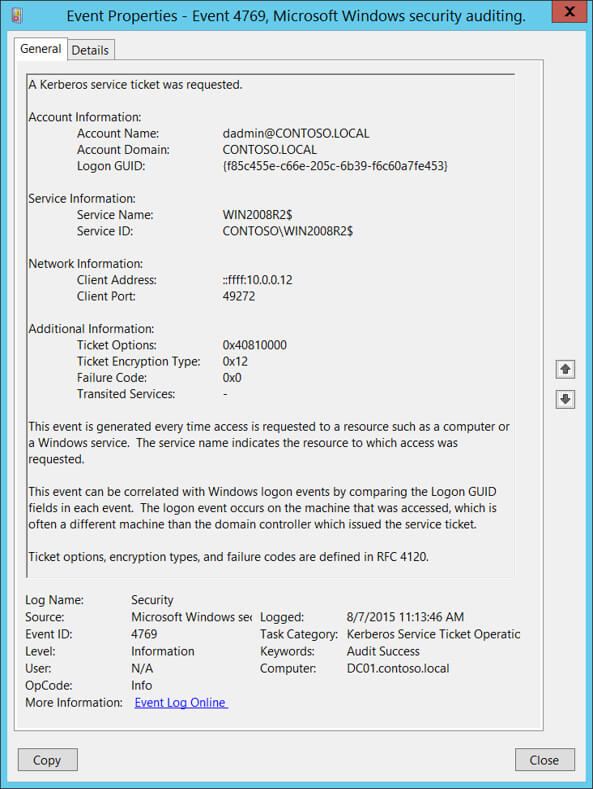
What Log Data is Shown?
Service tickets serve as golden keys, enabling users or services to unlock doors to designated resources. With each ticket request, a trove of information is encapsulated within Event ID 4769 logs:
Account Information
- Account Name: Specifies the name of the account for which a service ticket was requested. This includes both user and computer accounts.
- Account Domain: Identifies the domain to which the account belongs.
- Account ID: Represents the Security Identifier (SID) of the account that requested the service ticket.
Service Information
- Service Name: Indicates the name of the service or resource being accessed for which the service ticket is requested.
- Service ID: Denotes the Security Identifier (SID) of the service or resource account in the Kerberos Realm.
Network Information
- Client Address: Specifies the IP address of the computer from which the service ticket request originated.
- Client Port: Indicates the source port number of the client network connection.
Additional Information
- Ticket Options: Represents a set of different ticket flags in hexadecimal format, specifying options such as Forwardable, Renewable, and Proxiable.
- Result Code: Displays a set of different failure codes in hexadecimal format, providing insights into the outcome of the service ticket request.
- Ticket Encryption Type: Specifies the cryptographic suite used for encrypting the service ticket.
- Pre-Authentication Type: Indicates the type of pre-authentication method used for the service ticket request.
- Transited Services: Lists the names of intermediary services through which the service ticket was passed
- Key Encryption Type: Specifies the encryption type used for the session key within the service ticket.
- Client Name: Identifies the name of the client requesting the service ticket.
- Client Realm: Indicates the Kerberos Realm to which the client belongs.
Event 4769 Result Codes
| Result code | Kerberos RFC description | Notes on common failure codes |
|---|---|---|
| 0x1 | Client’s entry in database has expired | |
| 0x2 | Server’s entry in database has expired | |
| 0x3 | Requested protocol version # not supported | |
| 0x4 | Client’s key encrypted in old master key | |
| 0x5 | Server’s key encrypted in old master key | |
| 0x6 | Client not found in Kerberos database | Bad user name, or new computer/user account has not replicated to DC yet |
| 0x7 | Server not found in Kerberos database | New computer account has not replicated yet or computer is pre-w2k |
| 0x8 | Multiple principal entries in database | |
| 0x9 | The client or server has a null key | Administrator should reset the password on the account |
| 0xA | Ticket not eligible for postdating | |
| 0xB | Requested start time is later than end time | |
| 0xC | KDC policy rejects request | Workstation restriction, or Authentication Policy Silo (look for event ID 4820) |
| 0xD | KDC cannot accommodate requested option | |
| 0xE | KDC has no support for encryption type | |
| 0xF | KDC has no support for checksum type | |
| 0x10 | KDC has no support for padata type | |
| 0x11 | KDC has no support for transited type | |
| 0x12 | Clients credentials have been revoked | Account disabled, expired, locked out, logon hours. |
| 0x13 | Credentials for server have been revoked | |
| 0x14 | TGT has been revoked | |
| 0x15 | Client not yet valid – try again later | 0x16 | Server not yet valid – try again later |
| 0x17 | Password has expired | The user’s password has expired. | 0x18 | Pre-authentication information was invalid | Usually means bad password |
| 0x19 | Additional pre-authentication required* | 0x1F | Integrity check on decrypted field failed |
| 0x20 | Ticket expired | Frequently logged by computer accounts | 0x21 | Ticket not yet valid |
| 0x22 | Request is a replay | 0x23 | The ticket isn’t for us |
| 0x24 | Ticket and authenticator don’t match | |
| 0x25 | Clock skew too great | Workstation’s clock too far out of sync with the DC’s |
| 0x26 | Incorrect net address | IP address change? |
| 0x27 | Protocol version mismatch | |
| 0x28/td> | Invalid msg type | |
| 0x29 | Message stream modified | |
| 0x2A | Message out of order | |
| 0x2C | Specified version of key is not available | |
| 0x2D | Service key not available | |
| 0x2E | Mutual authentication failed | May be a memory allocation failure |
| 0x2F | Incorrect message direction | |
| 0x30 | Alternative authentication method required* | |
| 0x31 | Incorrect sequence number in message | |
| 0x32 | Inappropriate type of checksum in message | |
| 0x3C | Generic error (description in e-text) | |
| 0x3D | Field is too long for this implementation |
How Does Kerberos Authentication Align with Event ID 4769?
Kerberos authentication and Event ID 4769 are intricately linked components within the realm of network security monitoring, with each playing a crucial role in verifying and granting access to resources within a domain environment.
Kerberos authentication, named after the three-headed guardian of Hades in Greek mythology, operates on the principle of mutual authentication between clients and servers. It relies on a trusted third-party authentication service, known as the Key Distribution Center (KDC), to issue and validate cryptographic tickets, enabling secure communication and access control within a network domain.
Event ID 4769, on the other hand, represents a specific event logged within the Windows infrastructure when a service ticket is requested by a user or service within the Kerberos authentication process. This event serves as a beacon, illuminating the shadows of network activity and providing crucial insights into access requests, user interactions, and potential security incidents within the domain.
The alignment between Kerberos authentication and Event ID 4769 lies in their symbiotic relationship within the authentication lifecycle:
1. Initiation of Authentication Process: Kerberos authentication begins with a client initiating a request for access to a specific resource within the domain. This initial request typically triggers Event ID 4768, signaling the request for a Ticket Granting Ticket (TGT) from the KDC.
2. Acquisition of Service Ticket: Upon successful validation of the TGT by the KDC, the client obtains a service ticket, granting access to the requested resource. This pivotal moment is captured by Event ID 4769, which logs the details of the service ticket request, including account information, service details, and network specifics.
3. Verification and Access Control: The service ticket obtained by the client is presented to the target server hosting the requested resource. The server validates the ticket using its own cryptographic keys, ensuring the authenticity and integrity of the request. If the ticket is valid, access is granted, allowing the client to interact with the resource securely.
4. Monitoring and Analysis: Event ID 4769 logs provide administrators with a wealth of information regarding service ticket requests, enabling them to monitor user activity, detect anomalies, and investigate potential security incidents. By analyzing these logs, administrators can identify unauthorized access attempts, track user interactions, and mitigate risks to the network environment.
Understanding Event ID 4769
Within the tapestry of Windows logs, Event ID 4769 emerges as a critical indicator of network activity, specifically capturing the moment when a Kerberos service ticket is requested. Understanding the nuances of this event is paramount for maintaining robust network security measures.
Anatomy of Event ID 4769
In dissecting Event ID 4769, several key components come to light. The event reveals crucial details about the requester, including their identity, domain affiliation, and security identifier. Additionally, it delineates the targeted resource, providing insights into the service or resource being accessed within the domain environment. Furthermore, Event ID 4769 encapsulates network specifics, such as the client’s IP address and port, facilitating geographic tracing and anomaly detection. Lastly, it sheds light on the parameters governing the usage of the service ticket and the encryption methods employed, offering insights into the security posture of the authentication process.
Why Monitor Event ID 4769?
Monitoring Event ID 4769 transcends mere logging—it’s a cornerstone of proactive network security. By scrutinizing service ticket requests, organizations can detect unauthorized access attempts, identify anomalous behavior patterns, and audit user interactions with critical resources. This event serves as a sentinel, enabling organizations to fortify their security posture and thwart potential threats.
In the dynamic realm of cybersecurity, maintaining a vigilant stance is imperative. Monitoring Event ID 4769 emerges as a crucial practice, serving as a watchful guardian against potential threats, offering a multitude of benefits.
Vigilance extends to detecting unauthorized access attempts, where anomalies in service ticket requests serve as red flags for nefarious activities such as unauthorized access attempts or credential misuse. Additionally, monitoring Event ID 4769 facilitates the identification of suspicious network activity patterns. Unusual ticket requests may signify reconnaissance efforts or lateral movement within the network, providing valuable insights for threat detection and mitigation.
Furthermore, Event ID 4769 plays a pivotal role in auditing user access to resources. By tracking user interactions with critical resources, organizations can ensure compliance, maintain accountability, and fortify their security posture against potential breaches or insider threats. Overall, monitoring Event ID 4769 serves as a proactive measure, empowering organizations to stay ahead of emerging threats and safeguard their digital assets effectively.

 Important Group Policy Settings & Best Practices to Prevent Security Breaches
Important Group Policy Settings & Best Practices to Prevent Security Breaches 15 Most Common Cyber Attack Types and How to Prevent Them
15 Most Common Cyber Attack Types and How to Prevent Them Why Active Directory Account Getting Locked Out Frequently – Causes
Why Active Directory Account Getting Locked Out Frequently – Causes
