Lepide Auditor for Active Directory provides a scalable means of auditing changes made to configurations and permissions. Get the security intelligence you need to properly protect and audit Active Directory, including the “who, what, where, and when” of all changes made. Bolster Active Directory security, speed up investigations, mitigate the risks of privilege abuse and meet compliance requirements.
Audit all changes to Active Directory and Group Policy, with before and after values of every change and the answers to the who, what, when and where questions.
Improve access controls with reports on failed logon events, concurrent logon sessions, logon history, users logged on to multiple computers and much more.
Understand your AD structure with in-depth reports on the current state of users, groups, AD permissions, GPOs, GPO settings, and more.
Generate pre-defined Active Directory audit reports that are mapped to specific compliance regulations, including GDPR, HIPAA, PCI, CCPA and more.
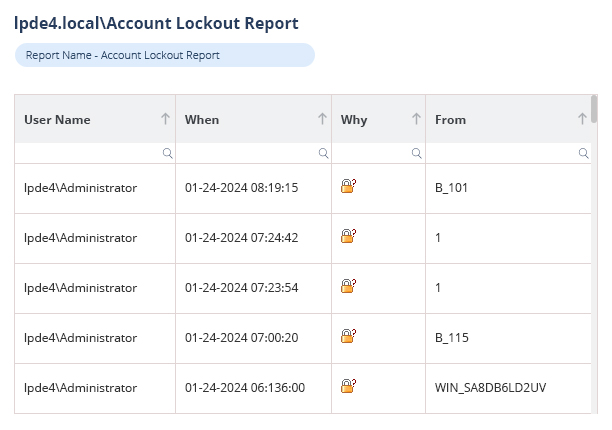
Helps you track account lockouts source and provides option to unlock them. Investigate which tasks, services, or processes causing account lockouts.
Improve your ability to detect and respond to insider threats and compromised accounts with proactive anomaly spotting and behavioral analysis.
Quickly and easily sort your AD Auditing data and refine your results as needed. Save searches to create custom reports for your specific needs.
Rollback any unwanted or unplanned change in Active Directory to its original value. You can even retrieve objects from tombstone and recycled states.
Audit and report on your inactive users in AD. Inactive users are often an entry point for attackers. Spot and manage inactive users to reduce your threat surface.
Automatically remind your users to regularly change their passwords to maintain a compliant and secure password policy.
Identify which of your users have passwords that are set to never expire. This is a potential security threat and breach of compliance regulations.
Get instant visibility over potential threats and unwanted changes with real time alerts. Automate your response with script execution off the back of alerts.
Take a virtual tour of the Lepide Data Security Platform in our web-based demo. See how Lepide aligns with your use case, whether it be ransomware, Active Directory security, Microsoft 365 security, data protection, data access governance or more.
Launch in-browser demo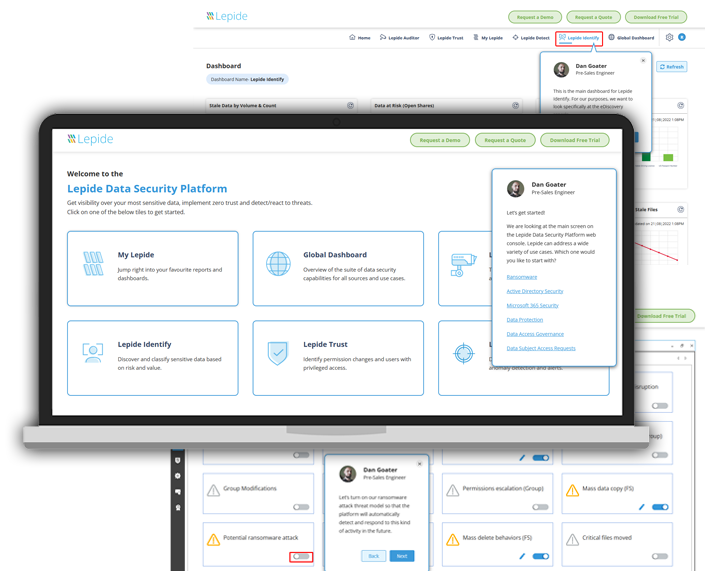
Leverage the Lepide Active Directory auditing software to address critical business problems that require urgent attention. Reduce your threat surface area, detect insider threats and compromised user accounts, and simplify IT operations and management tasks with our complete AD auditing solution.
Our interactive dashboards give you all the critical Active Directory auditing information you need to properly visualize your AD structure and spot critical changes. Easily audit permissions and configuration changes, spot potentially dangerous security states that need immediate attention, and monitor the health of your AD. Customize the dashboards to suit your specific needs.
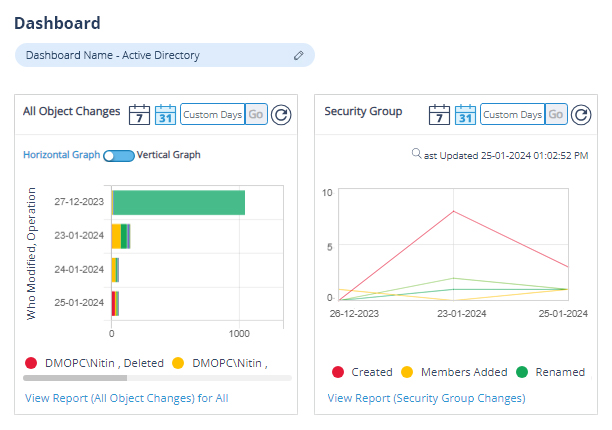
Active Directory structures can become complex and difficult to understand as an organization grows and evolves. Attackers can easily exploit a lack of visibility over this structure. Our Active Directory audit software gives you the ability to easily see who has what levels of access and how they got them so that you can easily visualize your AD structure.
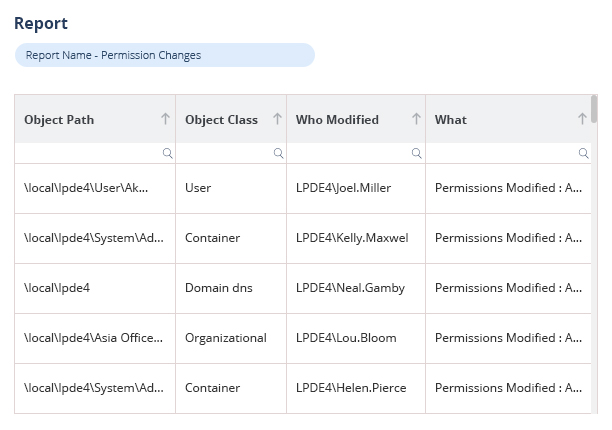
Delve into dozens of pre-defined Active Directory modification reports to get instant insight into all critical modifications that could indicate security risk. Spot modifications to infrastructure, containers, users, computers, groups, and more. Pre-defined threat models capture suspicious or unwanted behavior/changes in real time and can send out alerts or trigger automated responses to contain the threat.
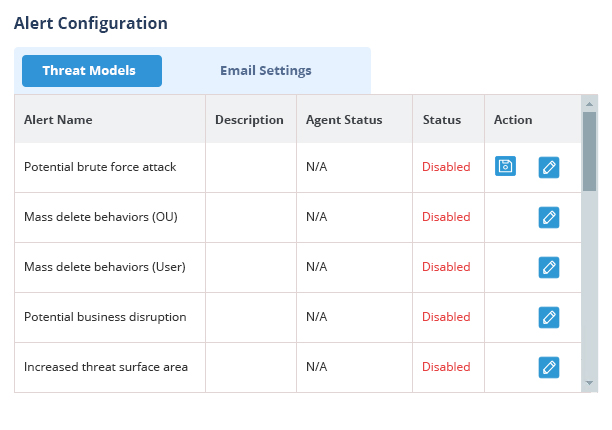
Our Active Directory auditing tool gives you the ability to easily investigate insider threats and compromised user accounts with a detailed audit trail and interactive searching, sorting, and filtering. Investigating incidents using the native audit log in AD is near impossible. With Lepide, you can demonstrate effective and efficient incident investigations and threat response.
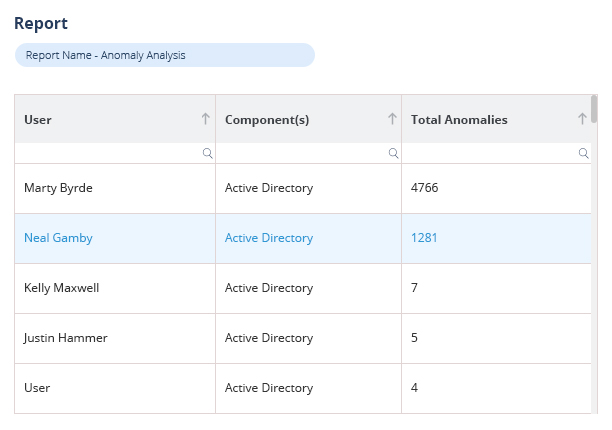
The Lepide Active Directory auditing software enables you to identify potential areas of risk within your Active Directory security states. Identify inactive users, open shares, stale data, users with non-compliant passwords, misconfigurations and excessive user permissions, so that you demonstrate your commitment to reducing overall security risk for one of the most common security threat entry points; your Active Directory.
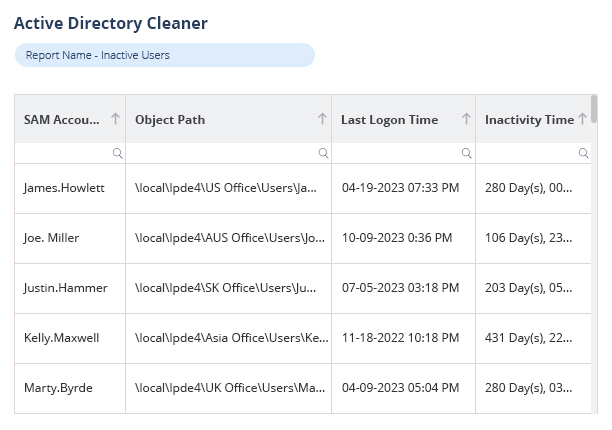
Our Active Directory auditing tool helps IT teams simplify and automate often time-consuming tasks and helps to reduce downtime from common IT helpdesk requests. Easily identify the source of account lockouts, restore deleted objects with the click of a button, remind users when their passwords are about to expire, and more.
Our Active Directory auditing software helps organizations overcome the limitations of native auditing, by aggregating event log data into “single-pane” reports. Below is a non-exhaustive list of what changes you can track with our Active Directory auditing tool.

We use Lepide for the security of our Azure and On-prem environment, its real time alert system is awesome!

Lepide is straightforward to use and effective right off the bat. Plus, the level of patience, attentiveness and technical knowhow is far beyond most support and sales teams I’ve seen before.

We chose Lepide as they were able to offer us threat detection and response, and a way of separating out reporting duties to a web console – all from one platform.

Lepide is a perfect fit for our IT Security and Compliance requirements. It helps us cut out a lot of wasted time and money and now we know we can be compliant with industry standards.

Lepide’s Active Directory Auditing software enables you to audit all critical Active Directory changes, including which users can create, manage or delete domain controllers, user and computer accounts, security groups, organizational units, trust relationships, administrative workstations and more.
Lepide also enables you to audit changes to configurations and permissions that could result in users with excessive privileges. This is critical when implementing a policy of least privilege.